Hackers are exploiting URL rewriting features—originally designed to protect users from malicious links—to launch increasingly stealthier phishing attacks.
Perception Point’s latest report reveals a significant rise in the abuse of these security tools, allowing attackers to mask dangerous phishing links behind the trusted domains of well-known email security vendors.
New phishing threat emerges
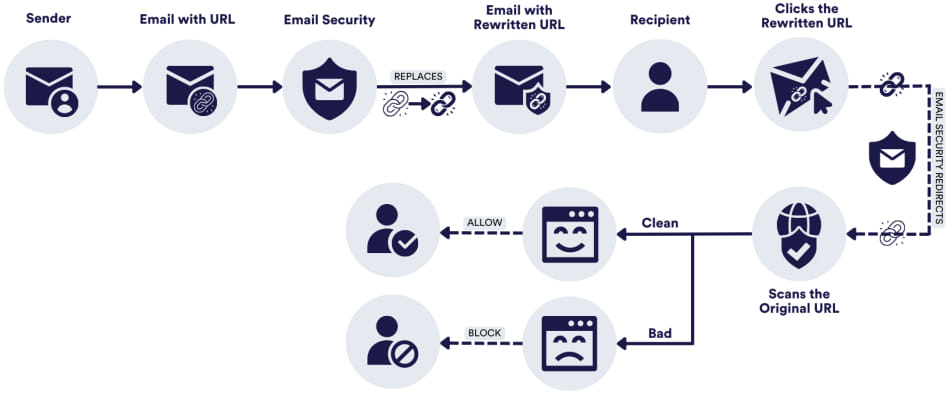
URL rewriting, a security feature used by many email protection services, modifies links within emails to redirect them through the vendor’s servers. This step allows the link to be scanned for threats before the user is directed to the intended content. Vendors like Proofpoint, INKY, and Mimecast employ this technique to safeguard users, scanning links either upon delivery or at the moment they are clicked. While this system aims to enhance email security, it has recently become a target for cybercriminals.
Perception Point
Beginning in mid-June 2024, security researchers at Perception Point observed an alarming increase in phishing campaigns that leverage these URL rewriting features. By carefully manipulating these rewritten URLs, attackers have successfully hidden phishing links behind the trusted domains of the security vendors themselves. This clever exploitation not only bypasses detection but also exploits the inherent trust users place in these familiar domains.
How URL rewriting is being exploited
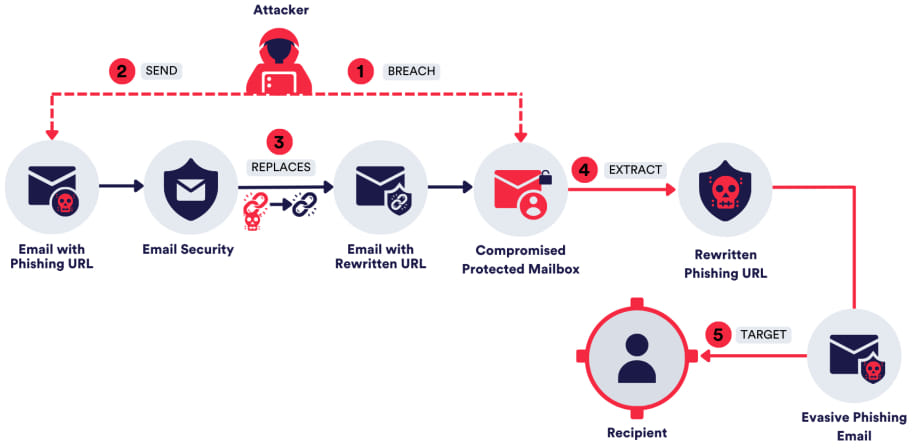
Attackers have developed methods to take advantage of the trust and security associated with URL rewriting. One common technique involves compromising a legitimate email account protected by a URL rewriting service. The attacker then sends a “clean” URL to this account, which, after passing through the security service, is rewritten to include the vendor’s domain. This rewritten URL, which appears legitimate, is later weaponized to direct users to a phishing site, bypassing most traditional security checks.
Perception Point
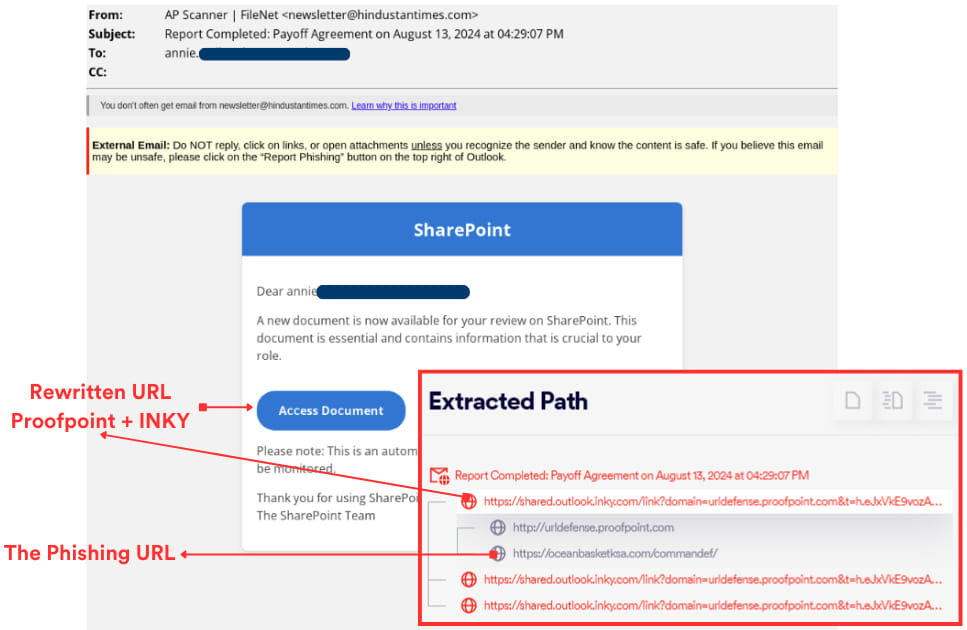
For example, in a recent phishing campaign intercepted by Perception Point, attackers used a “double rewrite” technique involving both Proofpoint and INKY. An email containing a malicious link was first rewritten by Proofpoint’s security system, and then by INKY, embedding an additional layer of security that ironically helped mask the true intent of the link. When victims clicked on the seemingly safe link, they were redirected to a phishing site after solving a CAPTCHA challenge, where their credentials could be stolen.
Perception Point
Perception Point’s report details several real-world examples where this tactic was employed:
- Attackers exploited both Proofpoint and INKY’s URL rewriting services in a sophisticated phishing campaign, leading victims through a CAPTCHA challenge to a fake Microsoft 365 login page designed to steal credentials.
- In another case, a phishing link rewritten by Mimecast’s URL Protection service redirected users to a phishing site masked by the domain mimecastprotect.com.
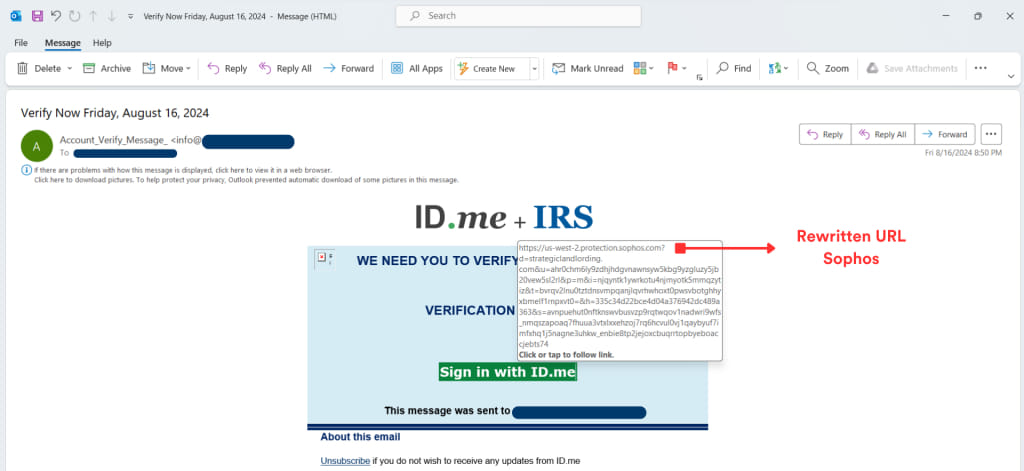
- Attackers used Sophos’s URL rewriting service to disguise a phishing link as an urgent IRS verification request, ultimately redirecting targets to a phishing website aimed at harvesting personal information.
Perception Point
Solutions
The manipulation of URL rewriting features represents a significant challenge for traditional email security tools. These attacks are particularly dangerous because they exploit the gap between when a URL is rewritten and when it is weaponized, making it difficult for most security solutions to detect the threat in time. The trust users place in well-known security brands only exacerbates the problem, as even vigilant employees may be fooled by these seemingly safe links.
To counter this emerging threat, Perception Point advocates for a more dynamic approach to email security. Their solution incorporates Dynamic URL Analysis, which actively browses and analyzes the behavior of URLs before the email reaches the inbox. This, combined with advanced anti-evasion techniques such as CAPTCHA breaking and geo-fencing detection, provides a higher level of protection against these novel phishing techniques.
This article first appeared in CyberInsider, written by anonwriter on August 20, 2024.























