Perception Point has once again discovered a new phishing trend. Perception Point intercepted this new Slack attack campaign through our Phishing detection mechanism accompanied by advanced email traffic analysis.
In this update, we will show how attackers are leveraging Slack’s referral URL in order to lead victims to phishing pages, thus evading legacy solutions.
We will keep sharing information on new trends for you to be better prepared for the next attacks. In case you’ve already been the victim of such attack or want to make sure it won’t happen to you, we encourage you to reach out to see how we can help.
IOCS.
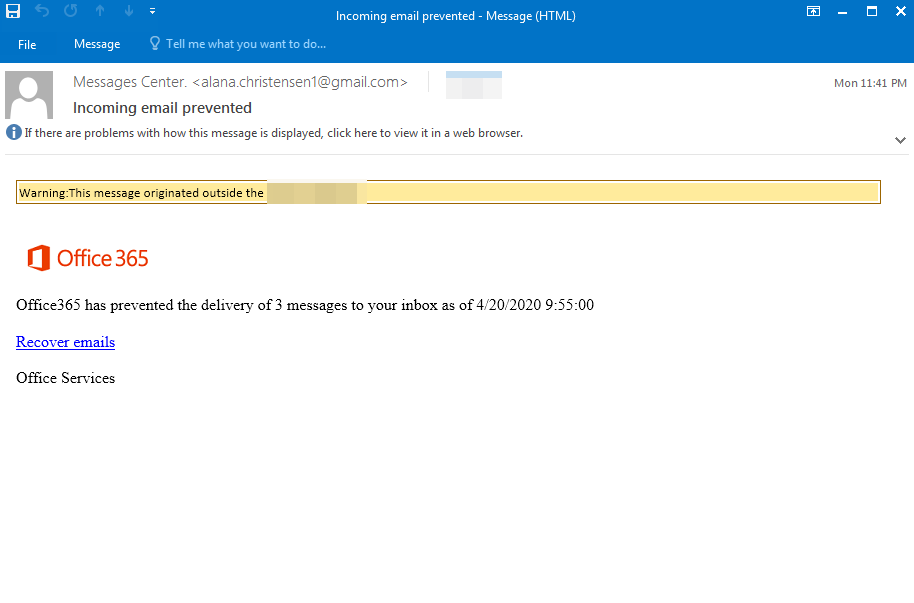
- Subject: Incoming Email Prevented
- Sender: “Messages Center” [email protected]
- Source IP: 202.191.119.79
- Phishing URL:
• https[:]//slack-redir[.]net/link?url=https%3A%2F%2Fstoragemanage.blob.core.windows[.]net%2Fstoragemanage%2FAp3dX.html%23
• https[:]//securityjobs[.]today/wp-content/hjhdf/indexa.php?P=_93894574342hdfjsixaoweue5_j1489738549283781331983743fncn_Product-UserID&u_1
Explanation.
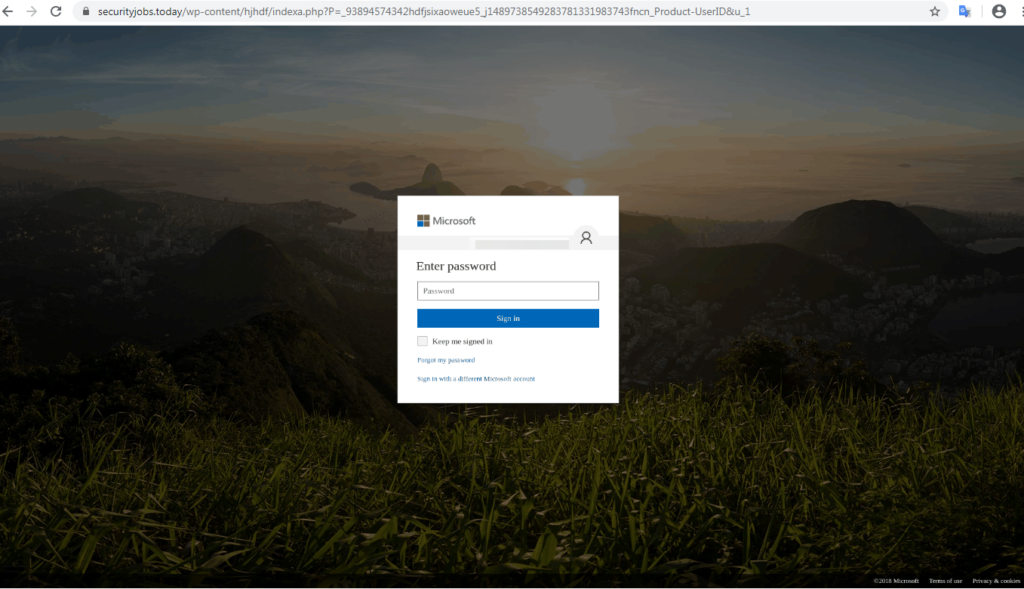
In this attempt, one can see that the attacker has masked himself to look like “Office 365 Message Center” and is attempting to entice the end-user to click on a link that will allow them to recover “blocked emails”. However, there is no real “blocked emails” and once the user clicks on the link, a malicious phishing site will come up in order to steal credentials.
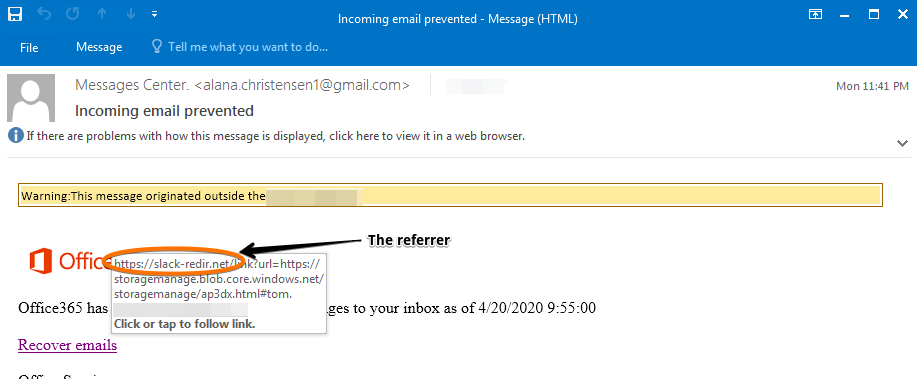
As is evident in the below screenshot, the attacker is using a “Slack referrer URL” to delivery their phishing site. By “hitchhiking” Slack’s legitimate URL domain, it allows the attacker to bypass multiple security layers, masking itself as a legitimate site.
So, what is a referrer URL?
The referrer URL appears in the first part of the URL, and it identifies the address of the webpage (i.e. the URL) which is linked to the resource being requested. In other words, it refers to the address of the previous web page that leads to the current requested page.
Once the victim clicks on the link and passes the referrer, the page will successfully redirect to the final page which is a well-designed phishing site (see below image), attempting to look like a Microsoft 365 log-in page and steal credentials.