Background.
USPS – the United States Postal Service – is an independent agency of the executive branch of the United States federal government, responsible for providing postal service in the United States, including its insular areas and associated states. USPS, as well as other shipping services such as DHL, UPS, FedEx, are common targets for phishing, impersonation attacks, and ransomware, and lately, due to the major growth in online shopping and deliveries, we are seeing an increase in not only the numbers of these attacks but also the level of sophistication.
In this campaign, the attacker is using various techniques to steal people’s credit card numbers by sending phishing emails related to deliveries from national postal systems. The emails try to lead users to phishing websites that capture their credit information. This is a widespread attempt that affects at least 26 countries, including the United States, Switzerland, China, Japan, and Singapore. There have already been reports about this campaign in the Hong Kong press and the United States.
In order to help the public and raise awareness, we decided to post about this spoofing attempt through a comprehensive blog that contains screenshots and recommendations. We hope this will help people understand how to prevent ransomware, phishing, and other cyber attacks.
Spoofing USPS.
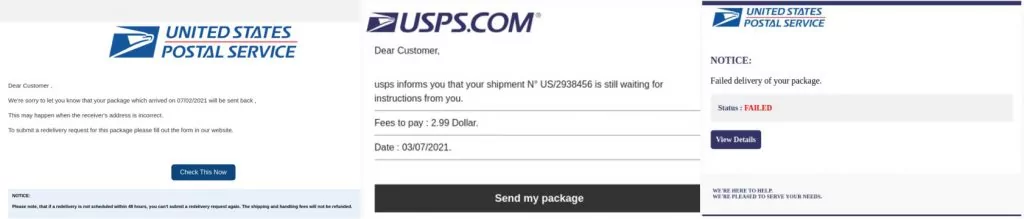
In the attacks that were recently detected and intercepted by our advanced email security platform, it appears that the attacker chose to impersonate USPS and distribute a notice of a failed delivery. As you can see below, the commonality is that the display name is changed to US Postal Service but the emails were sent from domains that do not belong to the company such as “magneta.de”, “healmylifeenergy.com”, “servicesinforeviews.com”
The Attack Flow.
Step one: The email is sent to the user
The user receives an email that looks very legitimate and contains the USPS company logo.
The attacker designed the email to prompt action and entice the user to click the “View Details” button.
Step two: The user clicks on the button and starts to fill in the details
Clicking the “View Details” button led us to a web application with the same design as the actual USPS website.
The attacker spoofed USPS website (www.usps.com) and leverages a similar domain that is quite misleading and easily missed www.tools-usps.com.
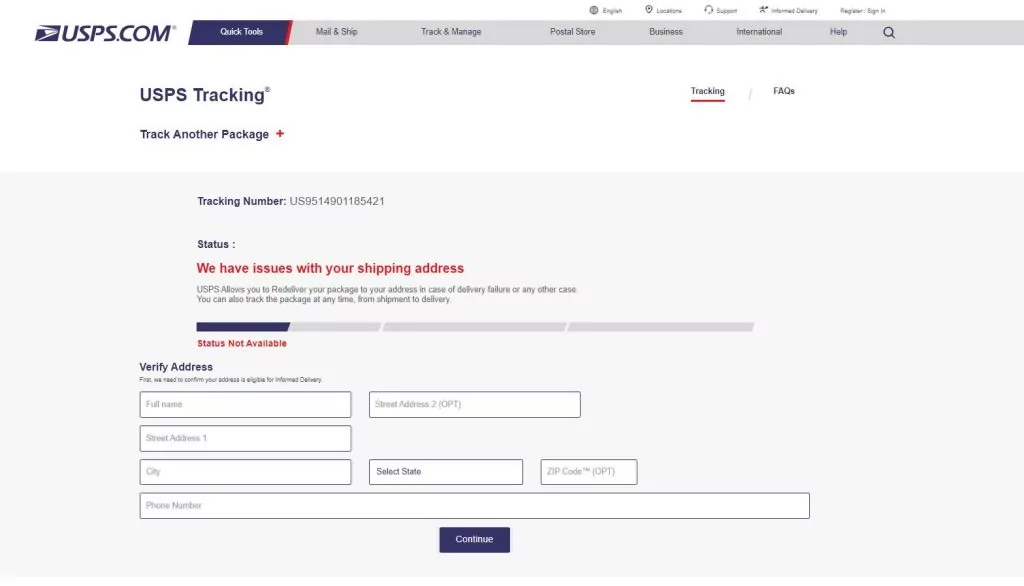
After clicking the button, we were led to the “index.html” page, or to a captcha that is designed to create legitimacy in the eyes of the users.

The page is seemingly a legitimate USPS page that asks to verify the delivery address. The attacker has also added validations to the format of the input, which increases the level of reliability.
Hints to Identify a Fictitious Site
At first glance, the website seems legitimate, but if we take a deeper look we will notice the following details:
- The URL
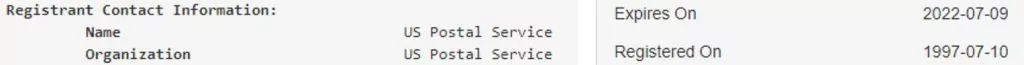
The URL doesn’t belong to USPS and was created a day before the attack was first seen.

This is in contrast with the real USPS domain which belongs to the company and was created at 1997:
- Lack of Validation
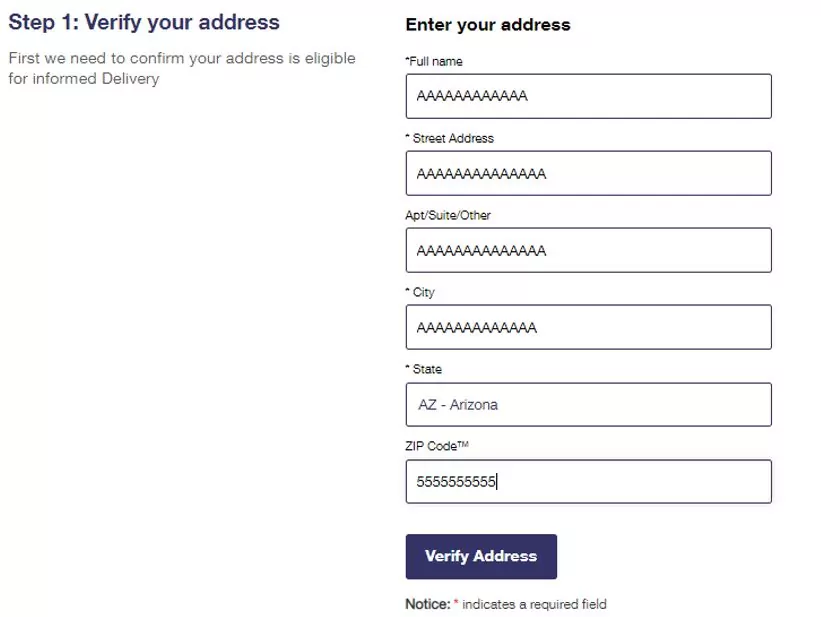
There is no validation on the correctness of the input, we were able to continue the process with random details:
- No Favicon
USPS favicon doesn’t appear on the tab that was opened, unlike the real website.
In comparison to:
Step three: Stealing the credit card details
After filling in the requested details on the previous page, we were led to a page which asks for credit card details.
Similar to the previous page, there were validations for the correctness of the input but we were able to continue with fake details.
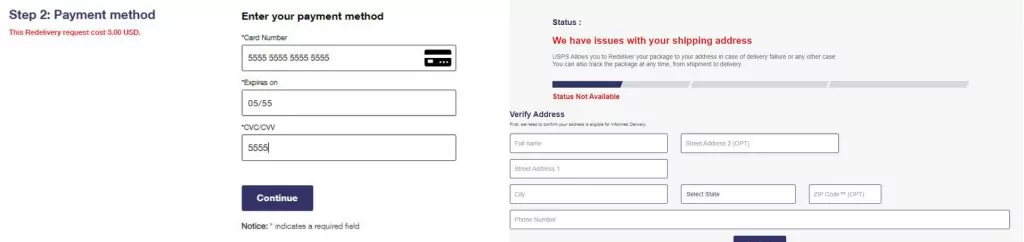
After filling in the details, they are sent to the attacker, followed by the display of additional pages that were created only to increase the perceived reliability.
Step four: Increasing reliability
After clicking on “Continue” on the previous page – we were taken to a page which pops up a loading gif and a couple of seconds later it redirected us automatically to a OTP (one-time-password) page.
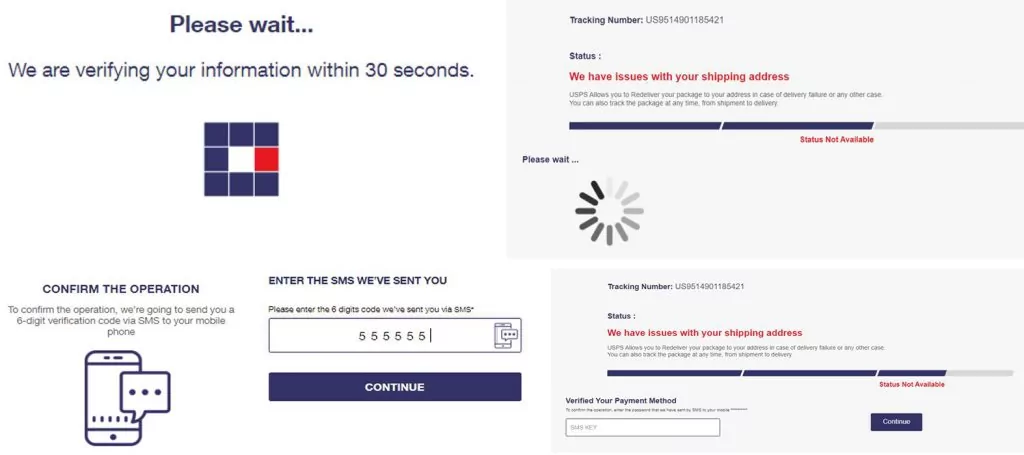
The only purpose for the above pages is to increase the reliability of the attack in the eyes of the user, after gaining his credit card details. Of course, the OTP (one-time password) is fake and no SMS was ever sent to us. We tried to continue by filling a fake one and were led to another page asking to re-enter the OTP:
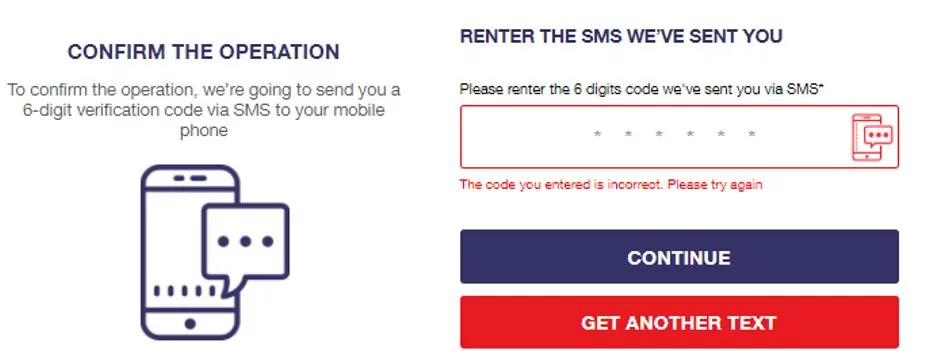
Clicking on “Get Another Text” returned us to the previous page to start the process again.We went back to the re enter OTP page, and filled in a fake OTP again. Next, it led us to a confirmation page, which is the last page of the attack which says that the payment was completed successfully and the shipment address was updated.
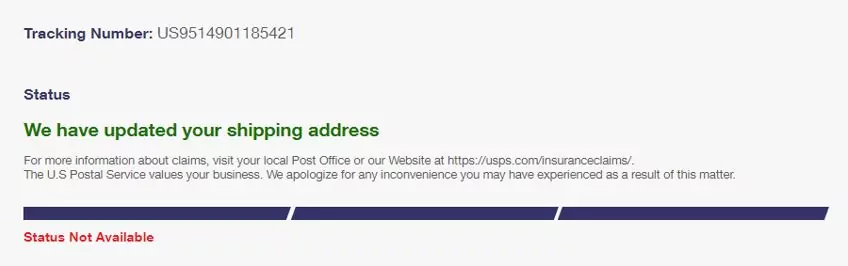
After a couple of seconds, we were redirected automatically to the official USPS website.
Best practices for avoiding email
phishing scams.
- Always check the display name and sender’s email address. Changing the display name is very common so validate the email address as well, to decrease the chance of a successful spoofing attempt.
- Question the need for submitting your credit card details – in this case, if the user didn’t create any shipping order, there is no reason for such a request.
- Avoid clicking links if you are not sure about them. If you click a link from an email, inspect the website even if it seems to display non-malicious content.
- Before giving away details, always check if the domain is known to you and that the website is protected by SSL (HTTPS and not HTTP).
- Not sure of the reliability of the website? Try clicking different buttons and see where it leads you, in our case all of the other buttons on the main page didn’t work – not a typical behavior.
- To avoid such cases, we would recommend to actively log into the official website and to check if your account has any outstanding debts.
- You can always try to enter fake details to check the website’s behavior, such as validations on invalid content etc.
- For organizations, use an advanced email security solution with dynamic analysis of files and URLs, so that these types of email attacks won’t ever get to the user’s inbox. By intercepting these emails, you don’t need to rely on your employees’ ability to catch these sophisticated of phishing attacks.























