Overview.
Due to the sudden remote-work situation, IT teams are deploying VPN’s for all their employees in order to ensure business continuity. VPN is one of the necessities of almost every company, even more so now. Attackers understand this new situation and as a result, are using it to their advantage. The attacker sends an email to employees that appears to be coming from the IT department of their own company, with instructions on how to work from home and install a VPN.
The content of the emails is always changing but the objective is usually to steal user-credentials, using a phishing link hidden in a “legit” looking link. In addition, it appears that all the attacks are conducted by the same phishing kit and the phishing URLs are hosted on multiple servers on Azure.
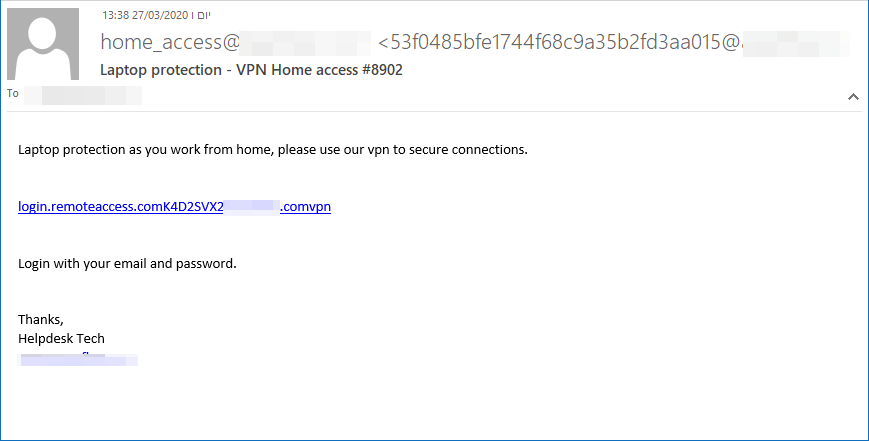
Below is a screenshot of one such attack. IOC’s can be found on the next page.
IOC’S.
Subjects:
- Additional VPN Channels
- Laptop protection – VPN Home access #8902
- VPN Portal – Home Access Connection #4207
- VPN connect from home #3718
- Home connection – VPN #8243
- VPN- Work from home connection #3613
From addresses:
- VPN-Tunnel <[email protected]>
- “[email protected]” <[email protected]>
- “[email protected]” <[email protected]>
- “[email protected]” <[email protected]
- [email protected]
- [email protected]
Sender IPs:
- 149.72.253.54
- 149.72.210.181
- 149.72.46.6
- 149.72.148.1
- 149.72.235.28
- 149.72.210.223
- 149.72.185.154
- 149.72.228.46
- 149.72.26.120
- 149.72.187.27
Phishing URLs:
- https[:]//thingsdoing[.]z19.web.core.windows.net/
- https[:]//cmakrkp033[.]z19.web.core.windows.net/
- https[:]//benching22[.]z19.web.core.windows.net/
- https[:]//cmakrkp66[.]z19.web.core.windows.net/
- https[:]//cmakrkp044[.]z19.web.core.windows.net/
- https[:]//cmakrkp88[.]z19.web.core.windows.net/
- https[:]//bbreakt88[.]z19.web.core.windows.net/
- https[:]//touchg33[.]z19.web.core.windows.net/























