Overview.
We’ve become used to headlines showing how attackers use conventional emails to perpetrate phishing attacks. In this article, however, we will present a novel Salesforce phishing attack in which the attacker leverages the Salesforce platform to carry out the attack and why advanced phishing protection is needed.
Salesforce, with over 50,000 employees, has over 150,000 customers worldwide including the likes of IBM, Paypal, and Morgan Stanley.
In this particular case, the attackers impersonate the Israel Postal Service. Indeed it’s the first time we’ve seen such an attack.
Perception Point’s advanced email security service managed to intercept these phishing campaigns targeting multiple Israeli organizations. What’s clear is that this is just the beginning, as attackers are constantly changing tactics in order to successfully carry out phishing attacks – and organizations need to ensure they’re adequately protected against these evolving threats.
Legitimate Use of Salesforce Mass Email Service for the Phishing Attack
In this case, it seems the attackers actually used the Salesforce Mass Email service, for carrying out this phishing attack.
Mass Email gives users the option to send an individual, personalized email to each recipient, thus creating the perception of receiving a unique email, created especially for you.
This is the first time we’ve observed the abuse of Salesforce services for malicious purposes.
Spoofing attempts of Salesforce are nothing new to us. Attackers spoof emails from Salesforce for credential theft, is a typical example. In this case, the attackers actually purchased and abused the service; knowing that most companies use this service as part of their business, and therefore have it whitelisted and even allowed in their SPF records. It is for this reason that your organization needs advanced phishing protection.
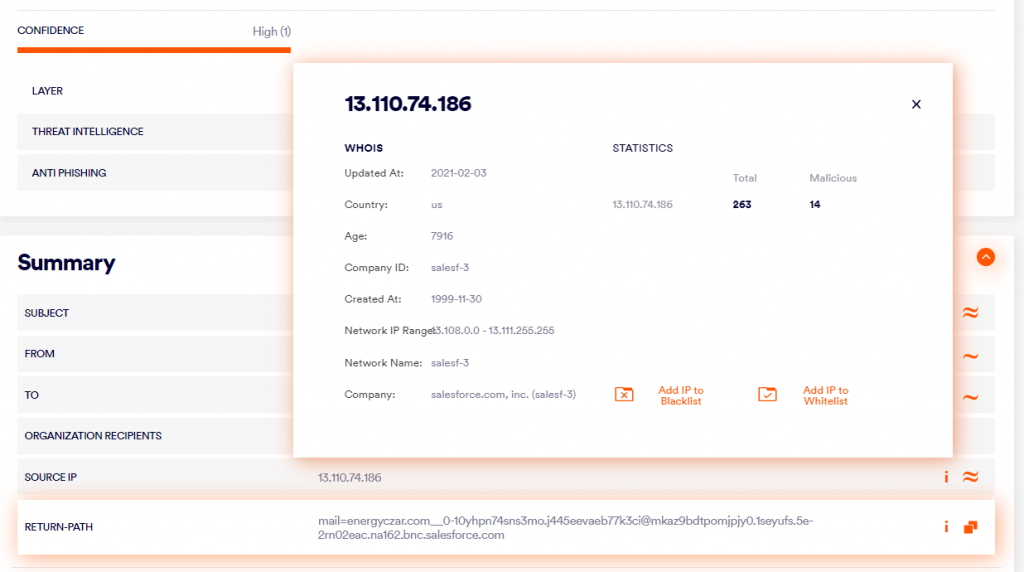
Most email security services are not able to detect attacks using the legitimate Salesforce platform, as they blindly trust that Salesforce is a safe source – even whitelisting the service’s IP addresses to reduce friction.
The Whitelist Vulnerability
While Salesforce’s recommendation is to whitelist their entire IP range, this creates a vulnerability in your company’s network.
Creating this type of whitelist is essentially ignoring the fact that the platform might be used for malicious purposes. By creating such a whitelist, one is basically creating a hole in one’s organizational security that such emails can sail straight through.
When users receive such emails, they are unable to distinguish that the email was sent via a Mass Email platform.
The Perception Point email security service, with advanced phishing protection, is able to detect this type of attack, and ensure that it never enters the employee’s inbox.
The Phishing Email

This is a spoofing attack purporting to be from the Israel Postal Service.
The attacker is deceiving the victim by “alerting” them that their package has been held up as a result of not paying shipping fees.
In this way, the attackers have created a sense of urgency, pressuring the victim into entering their credentials.

We can see in the email’s headers:
- X-Sender: [email protected] (Standard sender of all salesforce.com emails)
- X-SFDC-User: 0055e000004u6Ee (ID of the user who sent the email)
- X-mail_abuse_inquiries: http://www.salesforce.com/company/abuse.jsp (URL of salesforce.com’s email abuse policy)
- X-SFDC-EmailCategory: apiMassMail
- We also saw it was missed by some major email protection services (Proofpoint, ForcePoint, etc.)
The Phishing Attack Flow
Step 1: The Email is Sent to the User
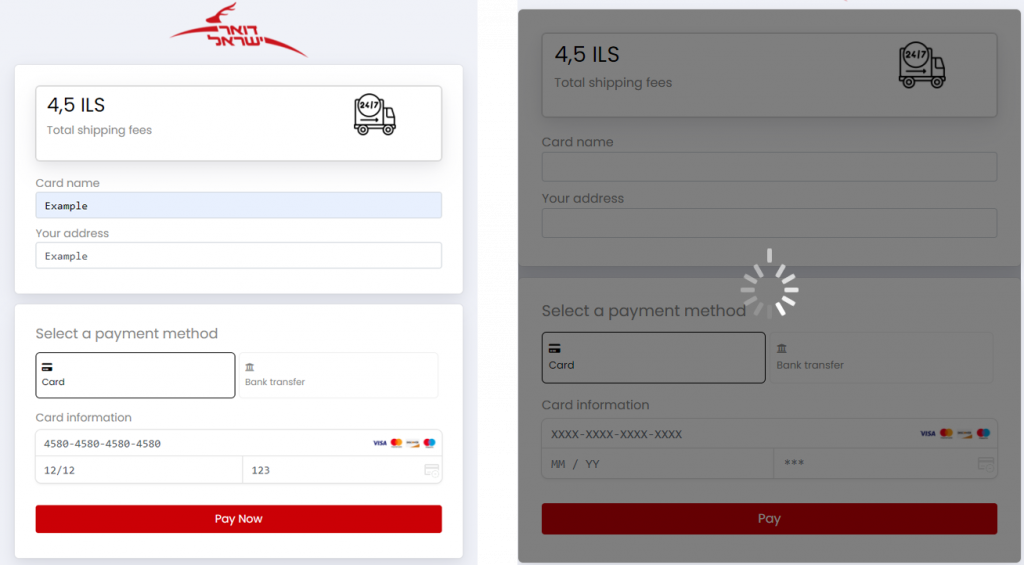
This email contains a link which automatically redirects us to https[:]//packisreall[.]com/ilen/.
This site is a spoofed website of the Israeli Postal Service where the user is prompted to enter their credit card details.
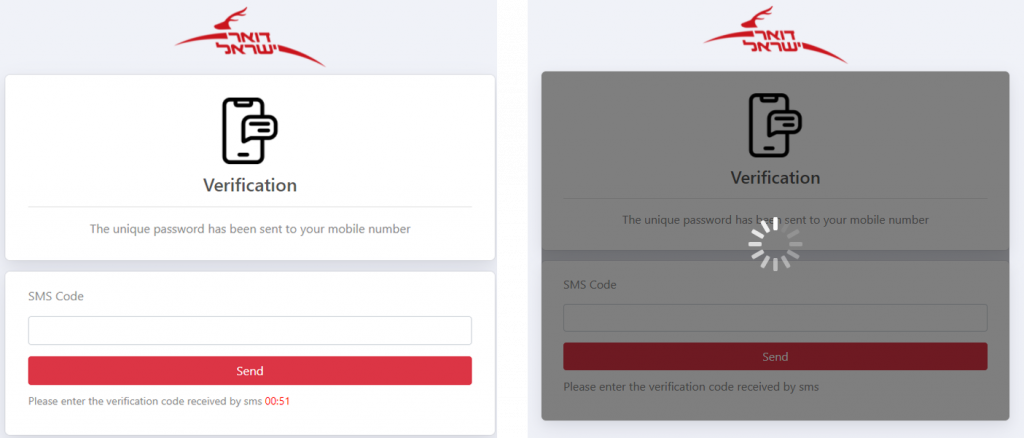
Step 2: Verification Code
The victim is redirected to another page, in which a verification via SMS code is required.
The Attacker’s Server
While investigating the attacker’s server, it was discovered that the malicious server was accessible without any authentication.
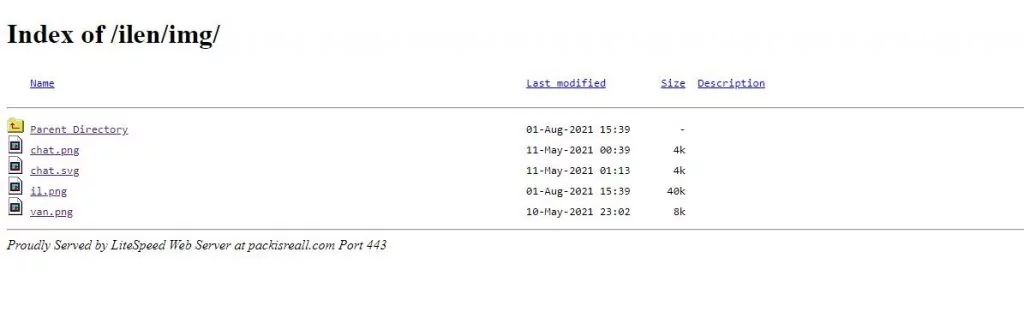
As you can see, this site is “Proudly Served by LiteSpeed Web Server at packisreall.com Port 443”.
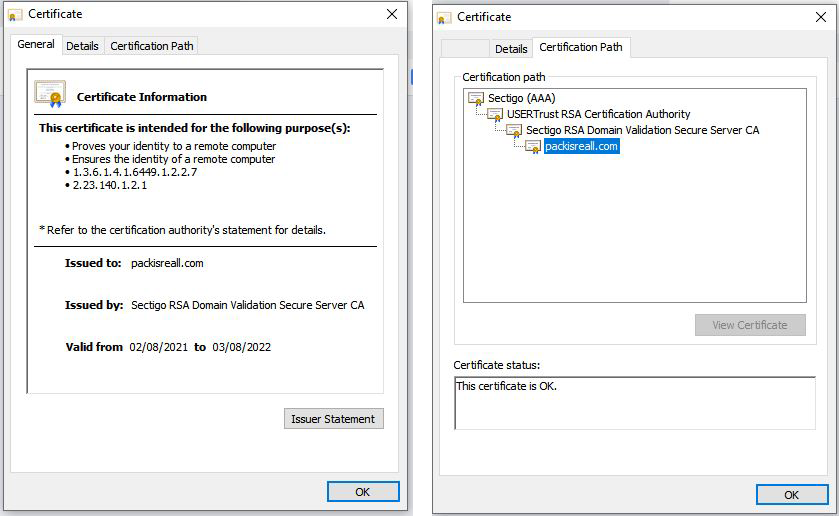
The Website Certificate
The site was developed and hosted by LiteSpeed Web Server and even has a certificate that was issued by “Sectigo RSA Domain Validation Secure Server CA”.
This shows both the lengths attackers will go to in order to trick users into parting with credentials and how easy it is for attackers to do so.
Recommendations.
This type of attack is frightening. It shows that no source can be trusted, even a domain such as salesforce.com which is well known and considered “safe”. We recommend the following initial steps:
- Always check the authenticity of the sender by checking if the display name and the email address match
- Question the need for submitting your credit card details – in this case, if the user didn’t create any shipping order, there is no reason for such a request
- Avoid whitelisting the IP addresses of mass email sending services within your organization
Finally, consider a solution for your company that does all of these things for you. Today, attacks have become so sophisticated that they are impossible to spot with the naked eye – and without deep technical knowledge. Perception Point’s advanced email security service, with advanced phishing protection, will ensure that these types of emails never reach your users, keeping them and your organization safe. Read more about advanced email security detection technologies to help secure your business.
Credit to Miri Slavoutsky & Shai Golderman























