In this sophisticated spear phishing attack campaign, attackers, using social engineering techniques, attempted to lure unsuspecting victims to enter their login credentials to fake login portals impersonating Microsoft, Gmail, WebMail, and WorldClient and were conducted en masse to achieve their goals.
The Email: Spear Phishing + Social Engineering
This spear phishing attack campaign started with a baited email enticing the recipient to open the attachment or click on the link to a webpage. As we have seen in other attacks, the emails usually focus on some segment of business operations, e.g., finance, human resources, logistics and general office operations and point to an attachment or link related to topics requiring user action. These topics include remittances, invoices, outstanding payments, requests for quotes (RFQ), purchase confirmation, shipment status, voice mails or fax delivery via email, to name a few. To make the email seem more legitimate, some criminals integrate specific information about the target in meaningful ways, including within the subject of the email.
As you can see from the example below, attackers sent emails as if they were from within the organization, with the subject line citing the customer’s name and a specific and relevant topic like “Fund Distribution Report”.
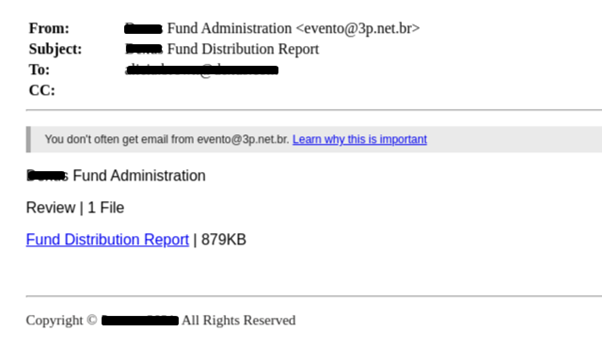
The goal of the email was to prompt the victims to click on the attachment titled “Fund Distribution Report”. This leads to https[:]//smcjk2knbr[.]live/, which redirects the victim randomly to one of three URLs that host the same website. For the sake of persistency, all three websites look the same, so that if one website is discovered and shut down, the remaining two continue to operate.
Our email security engine immediately detected that both the email format and sender name does not match the company’s format or name, and the sender domain does not exist, both telling signs that the email is a phishing attempt.

The Spear Phishing Attack Chain
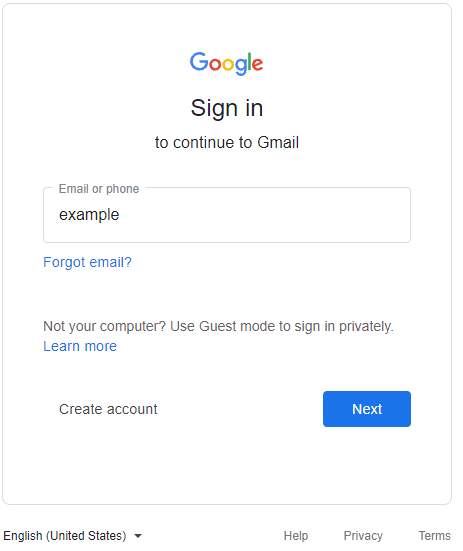
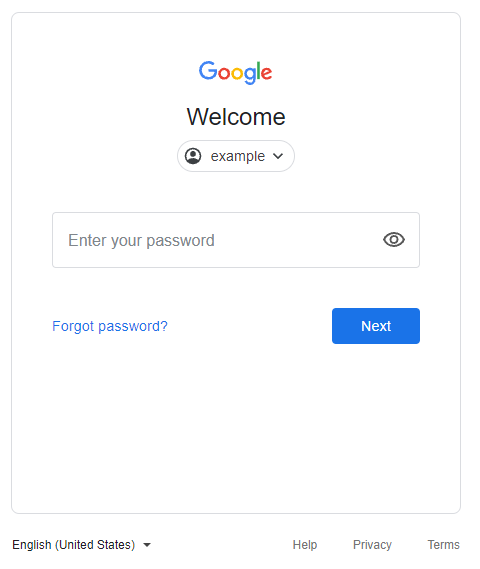
After the victim clicks on the fake attachment, they are presented with what appears to be a typical login page. To lower suspicion, scammers often highlight the need for heightened security or that the service logged the user out. In some cases, the pages are sent with the user’s email address already included which enhances the legitimacy of the request, and only prompts for the password.
In this case, a timer is displayed in order to create a sense of urgency, pressuring the victim into entering their credentials.

This spear phishing attack campaign is quite sophisticated in the sense that it represents a new technique that integrates spear phishing, custom webpages and the complex cloud single sign-on ecosystem to trick users into unwittingly divulging their credentials. This tactic uses seemingly benign webpages that, once opened, closely mimic legitimate login screens for Gmail, WorldClient, WebMail and Microsoft.
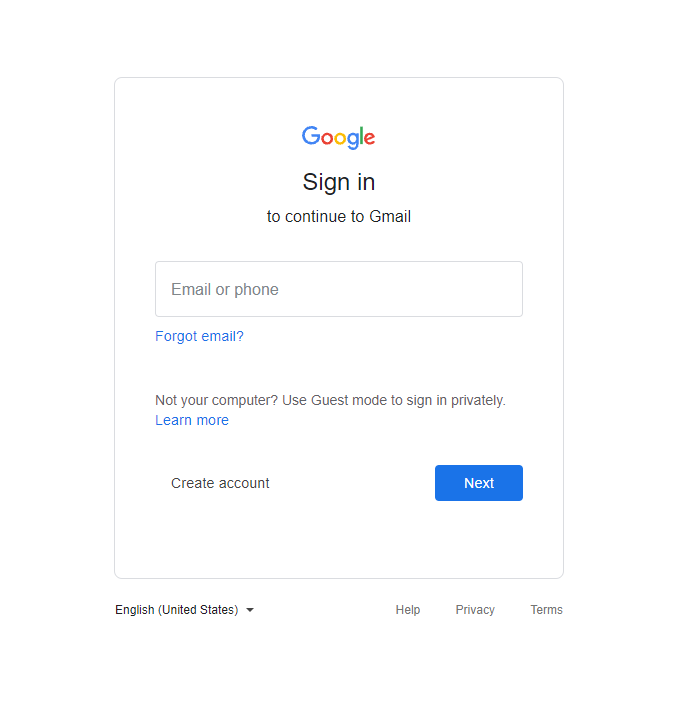

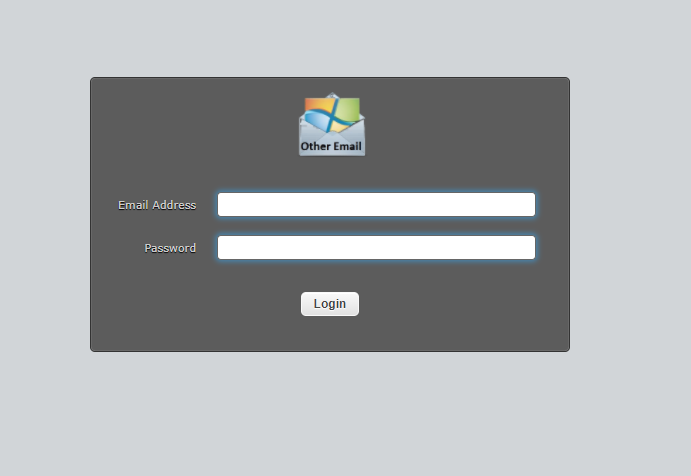

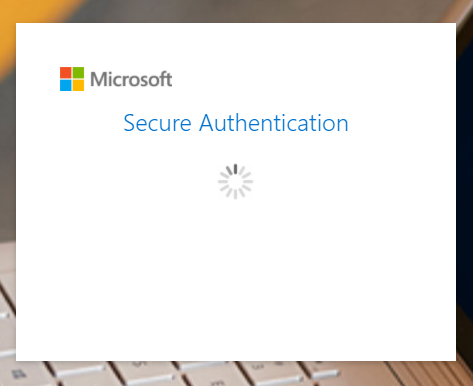
Upon entering their credentials, the victim receives an error message. For example, in the fake Microsoft login below, the authentication of the credentials seems as if it’s “stuck” and shows an endless animation.

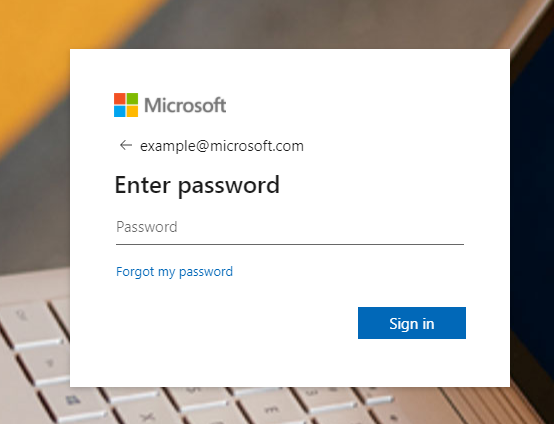
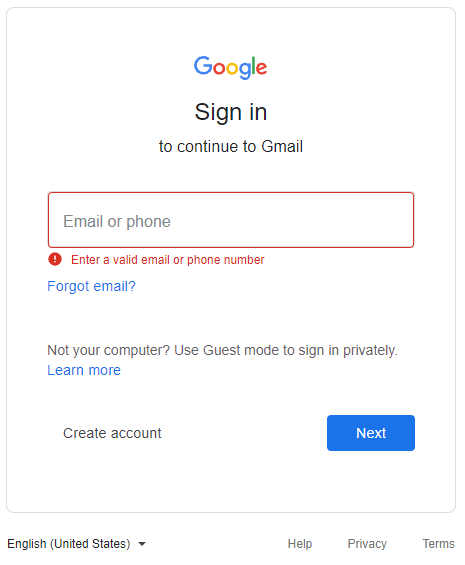
In the Google fake login, the user receives an error that the submitted credentials are not valid.
At this point, the attackers have already obtained the information they were looking for, the credentials, and are one step closer to defrauding a company or user. Now the attacker can conduct an initial reconnaissance of the user’s documents, transactions and correspondence, for example. Armed with this information, an attacker is now better informed to be able to: identify additional targets of value, understand business processes and approval chains, leverage the user’s documents or shared file access to create custom phishing documents, and use the account for financial gain or to pivot into more lucrative environments by masquerading as the account user.
Creating “Legitimacy”: Certificates & Hosting Site for the Spear Phishing Attack
Some attackers believe they can increase the chances of a victim to download files, or open links by simply pointing the victim to a website on a legitimate hosting service where the above techniques are incorporated within a hosted page. In this spear phishing attack campaign, the attackers created three different websites, all hosted on cPanel and all have valid hosting certificates. It can be very challenging to detect these tactics given their level of sophistication
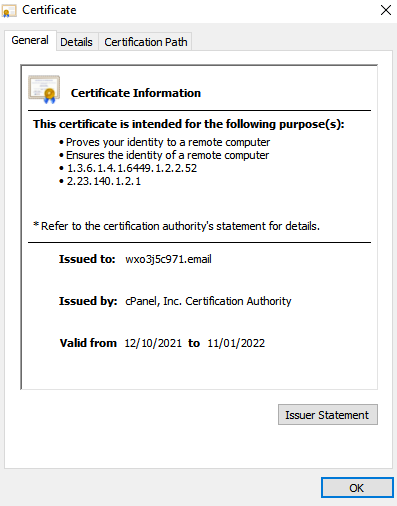
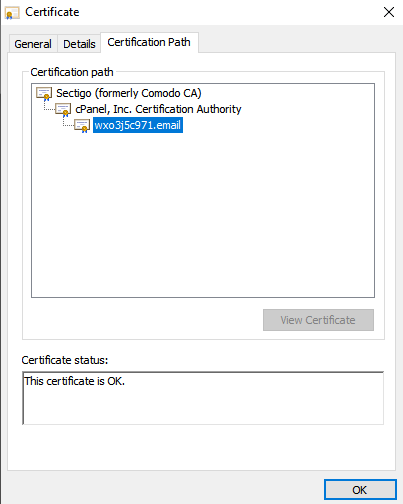
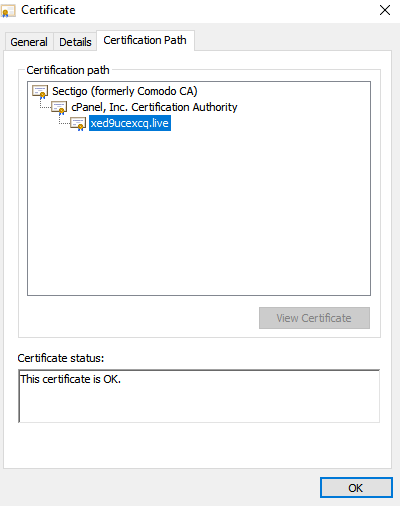
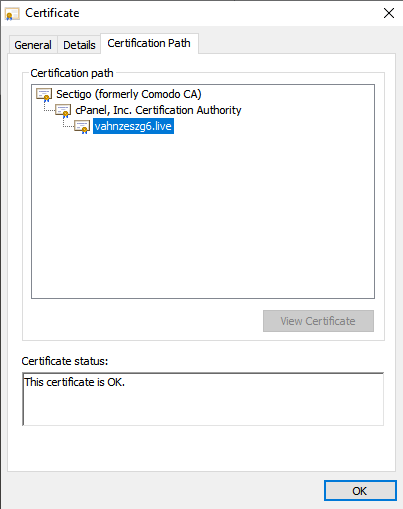
IOCs
From: [email protected]
IP : 158.69.244.219
Original site: https[:]//smcjk2knbr[.]live/
Redirects to:
- https[:]//wxo3j5c971[.]email/
- https[:]//vahnzeszg6[.]live/
- https[:]//xed9ucexcq[.]live/
Recommendations To Mitigate Spear Phishing Attacks
This spear phishing attack campaign deployed fairly sophisticated techniques to obtain victims’ credentials, including seemingly legitimate login pages, and using credible hosting certificates. In order to avoid becoming the next victim of such an attack, Perception Point’s Incident Response Team recommends the following to mitigate the risk of email compromise:
- Continue to educate and train your employees about email security and the risk of clicking on unknown URLs and attachments.
- Better safe than sorry. Avoid clicking on links that you’re not 100% sure about, and even if you end up clicking on a link from within an email, inspect the website thoroughly even if it seems to display non-malicious content.
- You can always try to enter fake details to check the website’s behavior, such as validations of invalid content.
- Keep in mind that many cybersecurity products will not automatically detect the tactics discussed in this spear phishing campaign. Consider using an email security solution that incorporates the following capabilities:
- Dynamic Scanning: the process of actually detonating files & URLs inside an isolated environment in order to detect malicious code execution.
- Image Recognition: deploying an engine that uses several advanced image recognition algorithms to validate if any URL is a legitimate site.
- Recursive Unpacking: unpacks the content into smaller units (files and URLs) in a recursive manner to identify hidden malicious attacks.
- URL Reputation: incorporating data from the four top URL reputation engines monitoring global traffic for phishing attempts.
- Threat Intelligence: combining multiple threat intelligence sources with a unique internally developed engine that scans URLs and files in the wild to warn about potential or current attacks.
Credit to Din Serussi & Shai Golderman of the Perception Point Incident Response who first reported and documented this attempted phishing attack.
Here’s some related content you may enjoy: How to Prevent Phishing Attacks























