Perception Point recently detected multiple high-volume phishing campaigns in which the attackers are using URL evasion and geofencing techniques while spoofing a variety of worldwide banking institutions, notably Standard Bank, Banco Bradesco, and Citizens Financial Group Inc. This is an ongoing campaign which has already affected dozens of organizations worldwide. We predict that in the following weeks and months attackers will add more banking brands to these phishing campaigns.

The current phishing campaigns are targeting the employees of multiple companies. However, this type of attack has the potential to quickly escalate to a potential breach in the organization. As soon as an employee enters his log in credentials, attackers can leverage this information to log in into the user’s work mail (ATO) and laterally move across the organization with malicious intent that could lead to theft of funds via BEC, compromised data and the deployment of malware including ransomware.
Unique Elements in this Phishing Campaign
The Use of Rebrandly
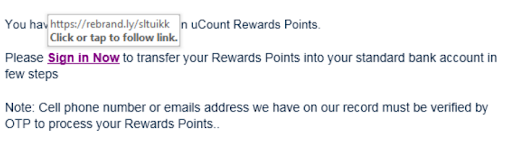
While attackers regularly change the spoofed banking institution, one element in these campaigns always remains the same and this is the use of URL shortener service called Rebrandly. The purpose of using this service is to hide the actual URL and replace it with a shorter one that is difficult for the victim to discern as malicious.
Geofencing
Another common recurring feature in this phishing campaign is the use of geofencing techniques to ensure only users from specific locations are actually redirected to the phishing page. This is unusual as most campaigns related to banking credential theft and fraudulent financial activity normally target large numbers of victims without much thought behind it. These campaigns are more carefully targeted and the spoofed banking brand matches the country of the organization to make it more credible.
The Use of Sentiment
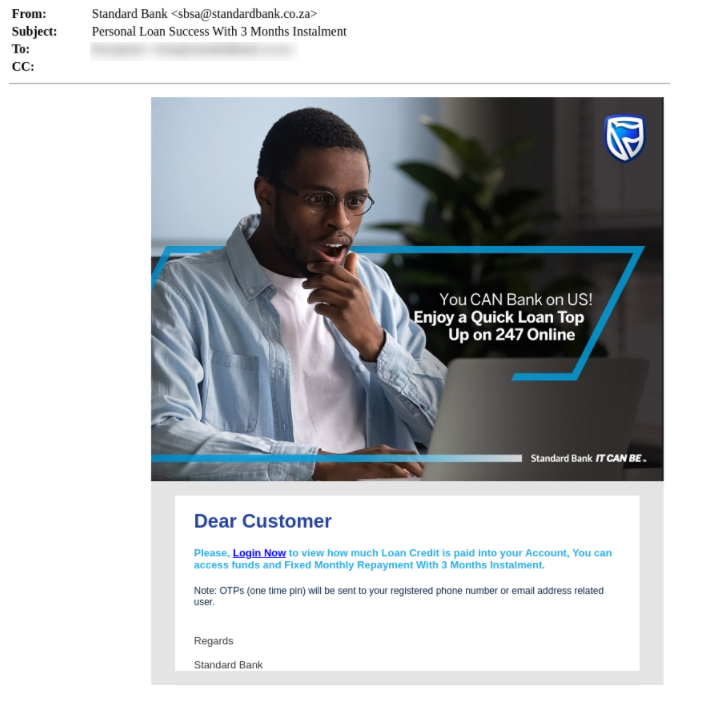
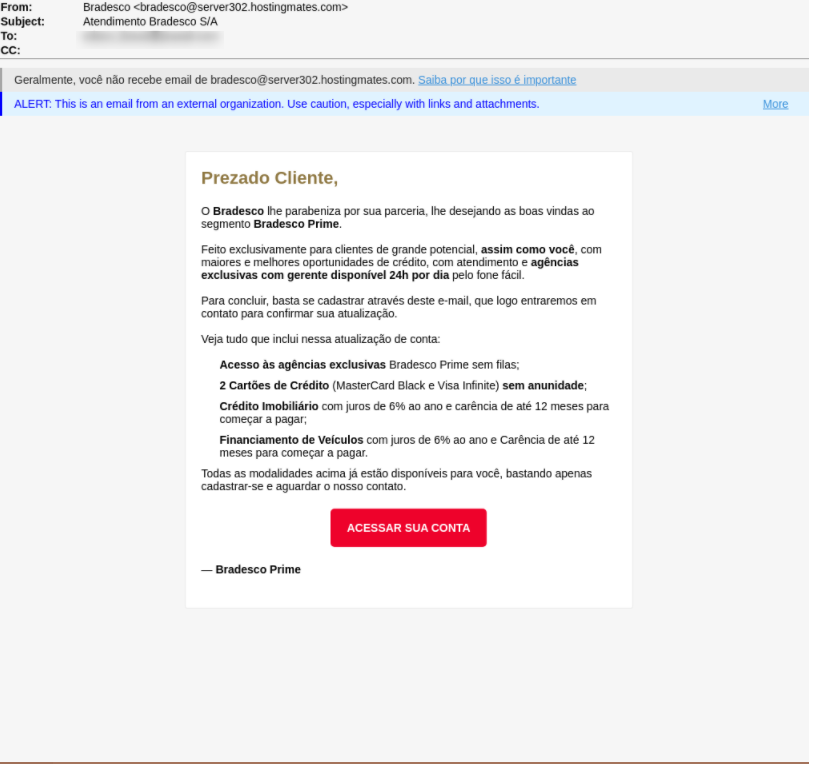
We have noticed two different approaches taken by attackers in these campaigns. The first approach uses a positive sentiment in which the attackers claim that there is a special reward or in some cases a unique deal that the user is qualified for. The second approach leverages urgency where the attackers claim that there is a suspicious account activity. Both approaches aim to entice the user to click the link embedded in the email which leads to a spoofed log in webpage.
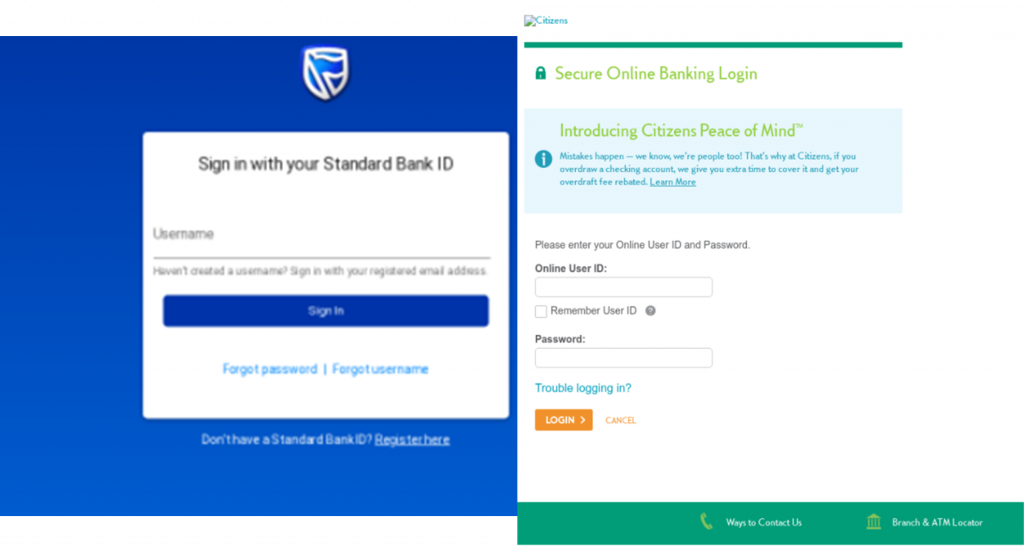
After the user submits his details he will be redirected to the spoofed bank webpage or in some cases to a random website chosen by the attacker.
Recommendations
There are multiple tips and signs that users should look out for in order to spot this phishing campaign:
- Hovering with the mouse over the links embedded in the emails will show the URL. If the URL does not match the domain of the brand, it is a red flag.
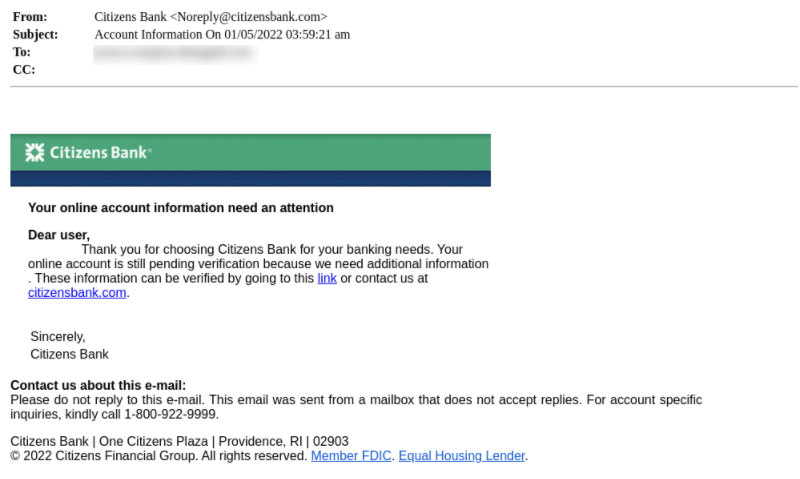
- The emails will address the user with “Dear Customer”. Banks have enough information on its users so when they send mails they will usually address the user. However attackers usually don’t have this information which is why the emails will be vague.
- It is extremely easy for attackers to spoof email addresses, which is why users must check the domain of the sender. If it is not the domain of the brand then it is an indication of a phishing attack. However if it is the domain of the brand then users should check if the address has the authority to send emails from that domain (SPF).
- If the email contains a direct link to a login page to update personal information, it is always preferable to go directly to the bank’s website by manually entering the address in your browser.
- Many email security products will not detect the tactics discussed in this phishing campaign, and you should look for a solution that has the following capabilities:
- Image Recognition to validate if any URL is a legitimate site.
- Recursive Unpacking that unpacks email and attachment content into smaller units (files and URLs) in a recursive manner to identify hidden malicious attacks
- URL Reputation that monitors global traffic for phishing attempts.
- Advanced Threat Intelligence that scans URLs and files in the wild to warn about potential or current attacks

Here’s some related content that you may enjoy: How to Prevent Phishing Attacks
IOCs:
From Addresses:
Citizens Bank[email protected]
Citizens [email protected]
Bradesco [email protected]
Standard Bank [email protected]
Standard bank [email protected]
Standard bank [email protected]
SBSA [email protected]
IP Addresses:
173.231.248.10
196.32.229.2
173.231.241.39
199.250.217.82
199.250.216.126
173.231.248.15
173.231.242.6
23.235.198.62
23.235.223.152
66.154.14.183
1.14.93.73
119.91.146.34
URLS:
https://rebrand.ly/0hfdklu —-> https://yarentekstil.com/citizens/shawn.htm
https://rebrand.ly/2zqngo4 —-> http://www.triumph-stag.de/wp-includes/ID3/acesso/
https://rebrand.ly/bl4ezuu —-> https://orableurfodiff.darmanpluss.ir/weell.hh/vsvsetr/vddfvdv/vdvfvdvf/bgbgbtg/hjjhhgfgg/nbfbfdb/vebfggdver/edvcxzvvdf/vdbdfbdb/hyjtujduj/fgbfbgfvbg/bgfbbrtth/sdcdfsr/xm_xx/wmwuyzgu=/
https://rebrand.ly/qe5k41z —->https://wp.adufes.org.br/wp-includes/js/thickbox/fusks3/f4f4/fr344r3/d4d4/dedfrr4/fvgd3/d43/sp_xx/mntm5ytc=/
https://rebrand.ly/vkmx6oa —->https://asimhalimsh.com/s7/Home/
Kudos to the Perception Point Incident Response Team, notably Ofek Ronen for their analysis!























