The past few months have witnessed a rise in attacks targeting the hospitality industry. More specifically, we have seen multiple attacks convincingly impersonate Booking.com to execute malicious payloads. In this post we examine some of these attacks that have resurfaced, targeting hotels, just in time for the new year.
Booking the Phish
In the first attack, the attacker impersonates Booking.com and sends a message to a hotel. The message claims that a former guest of the hotel has written a disparaging review, and urges the hotel to reply to the complaint, resolving the issue.
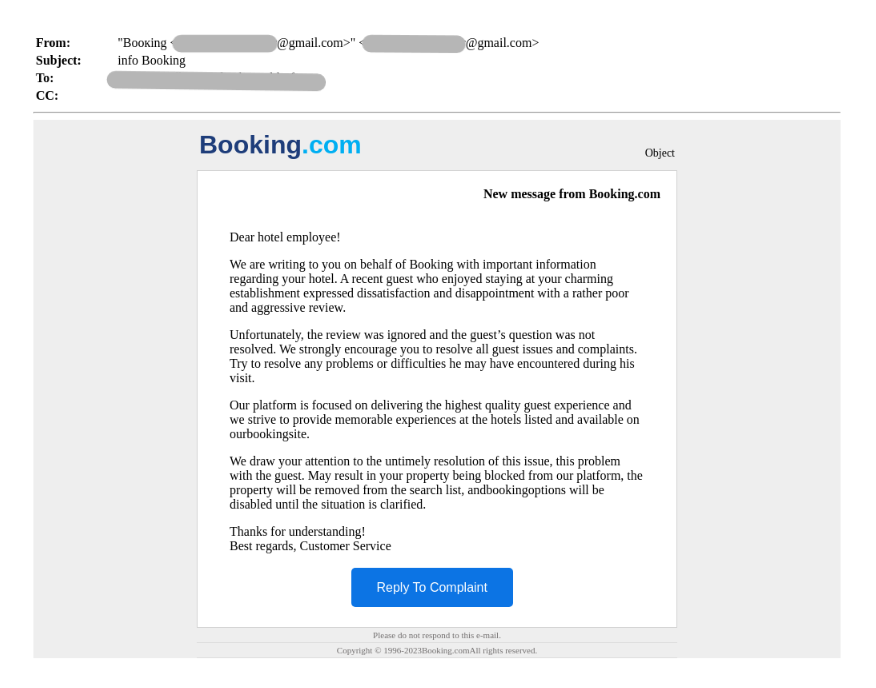
However, upon clicking the “Reply To Complaint” link, the recipient is led to a fake Booking.com website. The URL used is extremely similar to the actual URL that Booking.com uses:
Fake URL: hxxps://account[.]booking-sign[.]com/sign-in?op_token=vNGgY0o3sJ8LRVeu
Real URL: https://account.booking.com/sign-in?op_token
The target is urged to log into the site to manage their property. Unlike on the real Booking.com website, there is only one option to sign in, as opposed to offering linked services like Google, Facebook, etc.
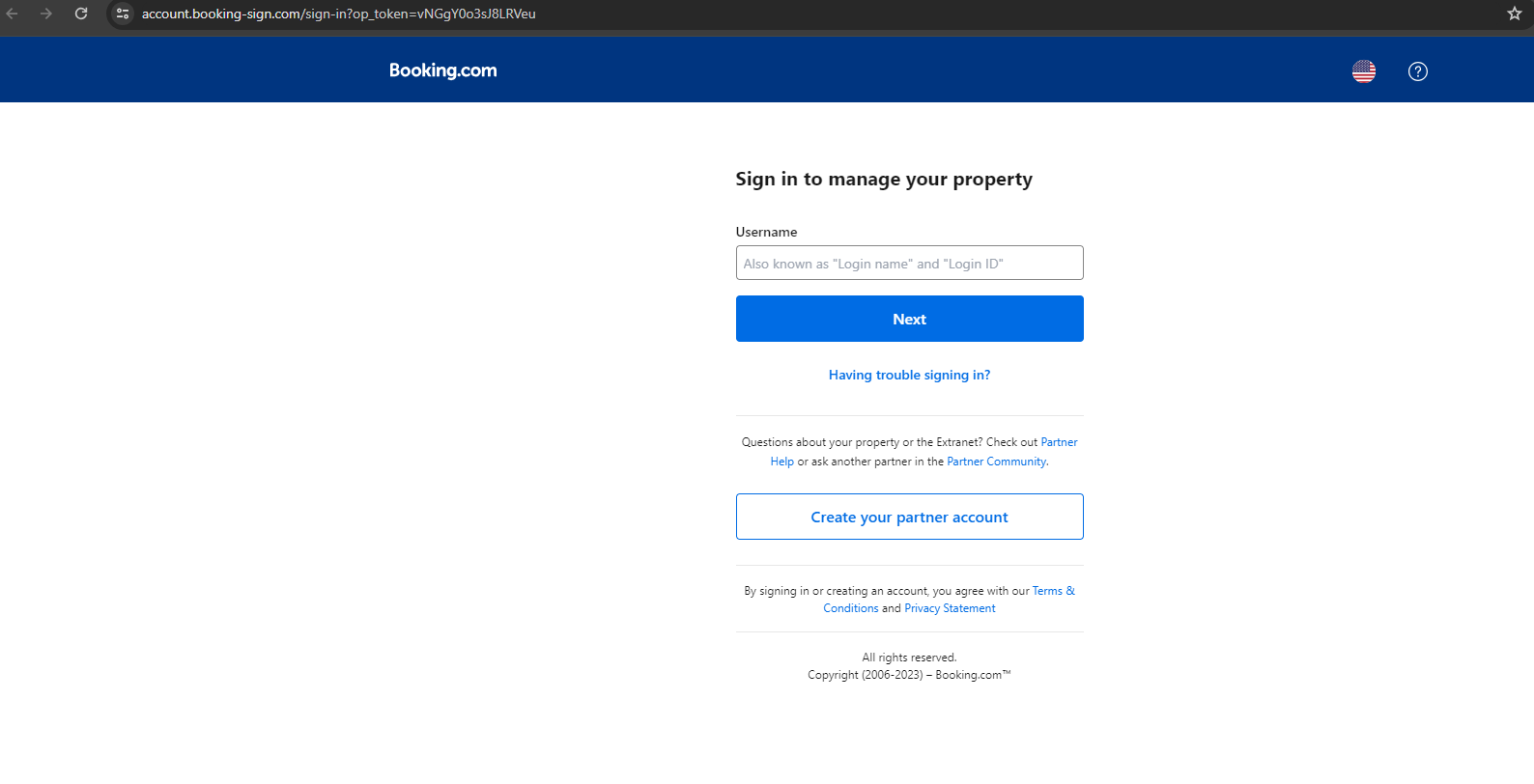
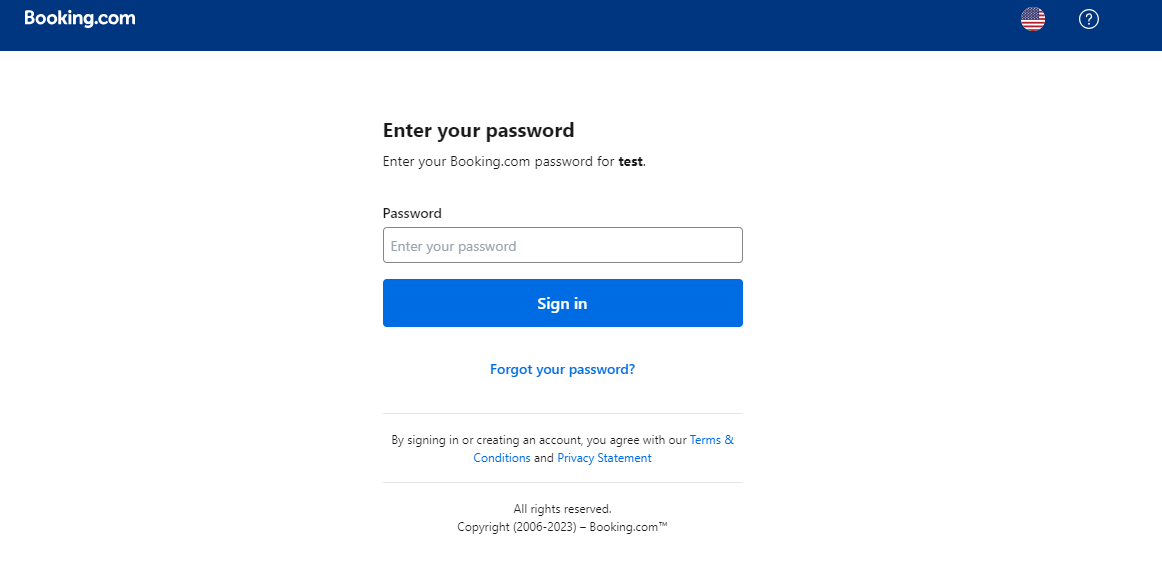
Upon entering the username, the target is asked for the password.
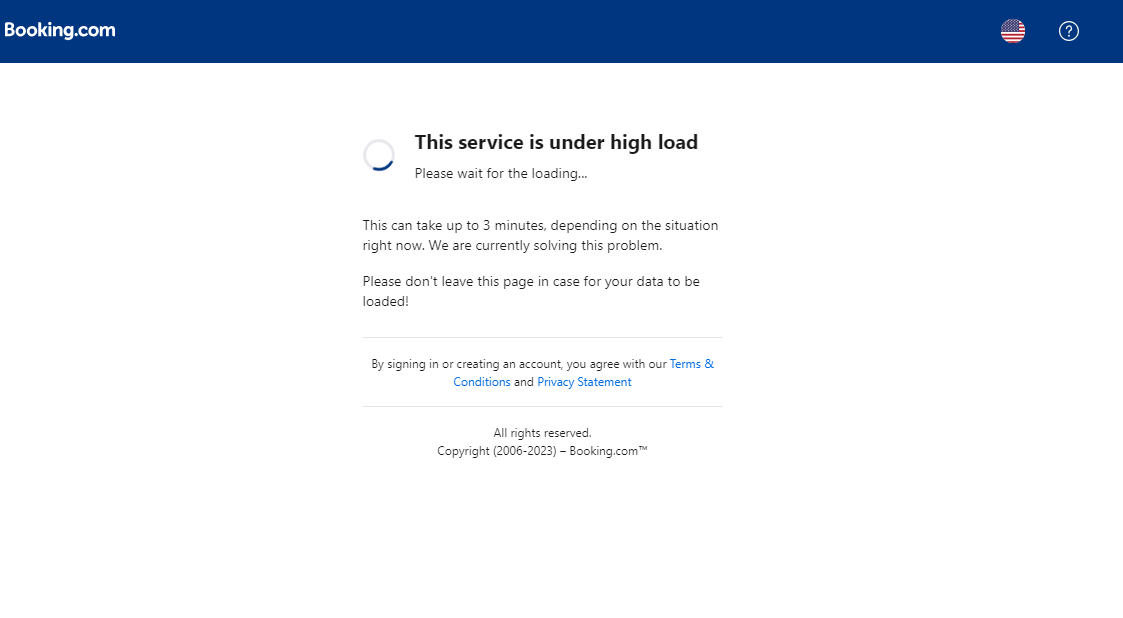
Once the target enters the password, they receive a loading message and are instructed to not leave the page. In actuality, there is nothing to load as the attacker has successfully stolen the hotel’s Booking.com credentials.
This Booking Seems Extra(net)
In another variation of the attack, attackers pose as Booking.com and send hotels a message, informing them of a change in policy. The message explains that if hotels do not log into the property management portal, Extranet, regularly, they risk account deactivation.

The user is urged to click the provided link, which leads to a spoofed Extranet login page. Once the user logs in with the hotel credentials, the attacker has successfully gained access to their Booking.com account.
Phishing Without Reservations
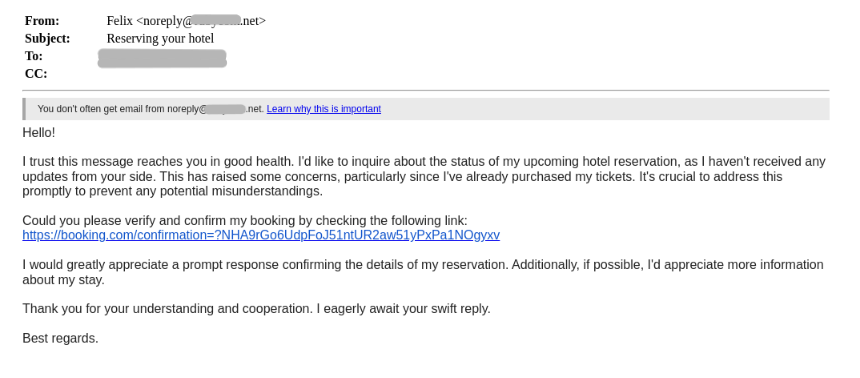
Another method attackers have been using to access hotels’ Booking.com credentials is by posing as future guests. Attackers send hotels a message, requesting details about their upcoming reservation. They ask the hotel to confirm their reservation by sending a link that appears to come from Booking.com. The danger lies in clicking the link, which leads to a spoofed Booking.com login page. The aim, of course, is for the user to login with the hotel’s credentials, only to be stolen by the attacker.
Hospitable Hacking
All of these attacks possess the same goal: to gain access to a hotel’s Booking.com profile. However, that is just the first step in the larger aim to execute mass phishing campaigns against hotel guests. By possessing hotels’ Booking.com credentials, attackers are privy to guest information, including emails, phone numbers, and in some cases even credit card details. While it is certainly useful to hack a hotel, the real payload lies in the customer data.
The hospitality industry is in the business of keeping customers happy. The strategies employed in these attacks exploit that desire, leveraging advanced social engineering tactics to achieve their malicious goals. Responding to a guest complaint, maintaining their property management portal, and addressing a future guests’ concerns are all high stakes scenarios that require urgent consideration from hotel employees. It is perhaps hotels’ hospitality that makes them such hospitable targets for attackers.
For more information on attacks targeting the hospitality sector, check out these blogs:
Stealing More Than Towels: The New InfoStealer Campaign Hitting Hotels and Travel Agencies
Booking.com Customers Hit by Phishing Campaign Delivered Via Compromised Hotels Accounts
























