As cyberattacks continue to target and breach organizations across diverse sectors, the hospitality industry finds itself in the crosshairs of a new threat. Perception Point’s team of security researchers recently discovered a sophisticated phishing campaign targeting hotels and travel agencies. This campaign is particularly concerning due to its highly targeted nature and its use of advanced social engineering techniques.
Suite Pattern with a Sinister Twist
Perception Point’s researchers have observed numerous variations of InfoStealer attacks, all focusing on hotels and related businesses. The common starting point? Booking a hotel reservation. This serves as the entry point for adversaries to initiate their malicious activities. But as you’ll see, what follows is far from ordinary.
Checking In: Setting the Ground for the Attack
Upon booking the stay, an attacker’s second move is seemingly innocent: they send an email to the hotel’s reservation desk in response to the automatic confirmation message they received. This email could be a query about making a new reservation or a reference to an existing one. In some instances, the email might even include a personal touch, mentioning that the sender’s son will be accompanying them.
Once the targeted hotel’s employee replies, the attacker ups the ante. Their follow-up email is carefully crafted to elicit both empathy and a sense of urgency. For example, they might claim that their son is prone to anaphylactic shock due to specific allergies. In other cases, the attacker could appeal to the hotel’s sense of responsibility towards elderly guests, stating they have parents over 70 and wish to print photos for them during their stay.
The Baited Hook: When Trust Becomes a Trap
Having established a rapport and a sense of urgency with the target, the attacker moves on to the next phase of their scheme. They send over a URL, ostensibly containing crucial documents – medical records for their child or an important map they would like to print out for their elderly parents.
To add a touch of legitimacy, they even provide the hotel representative with a password to unlock these so-called “important files.”
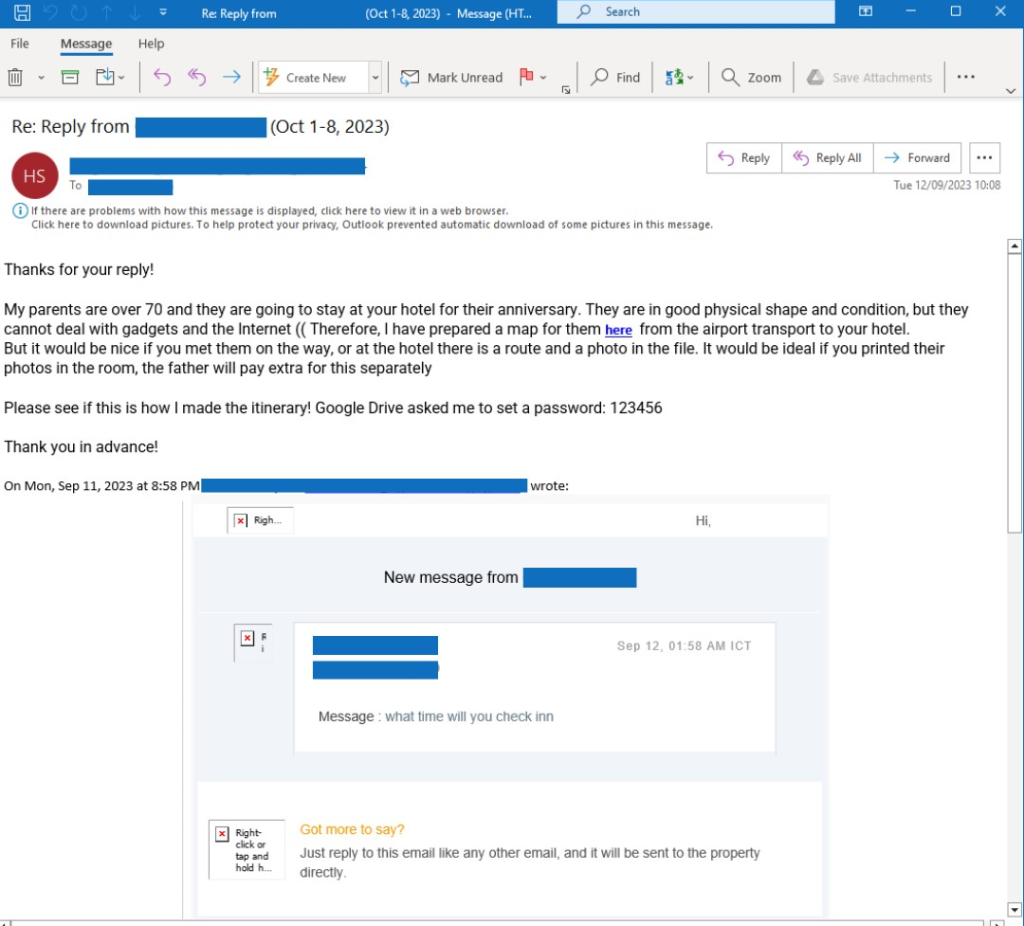
Social engineering involves elderly parents, anniversaries, and navigation difficulties
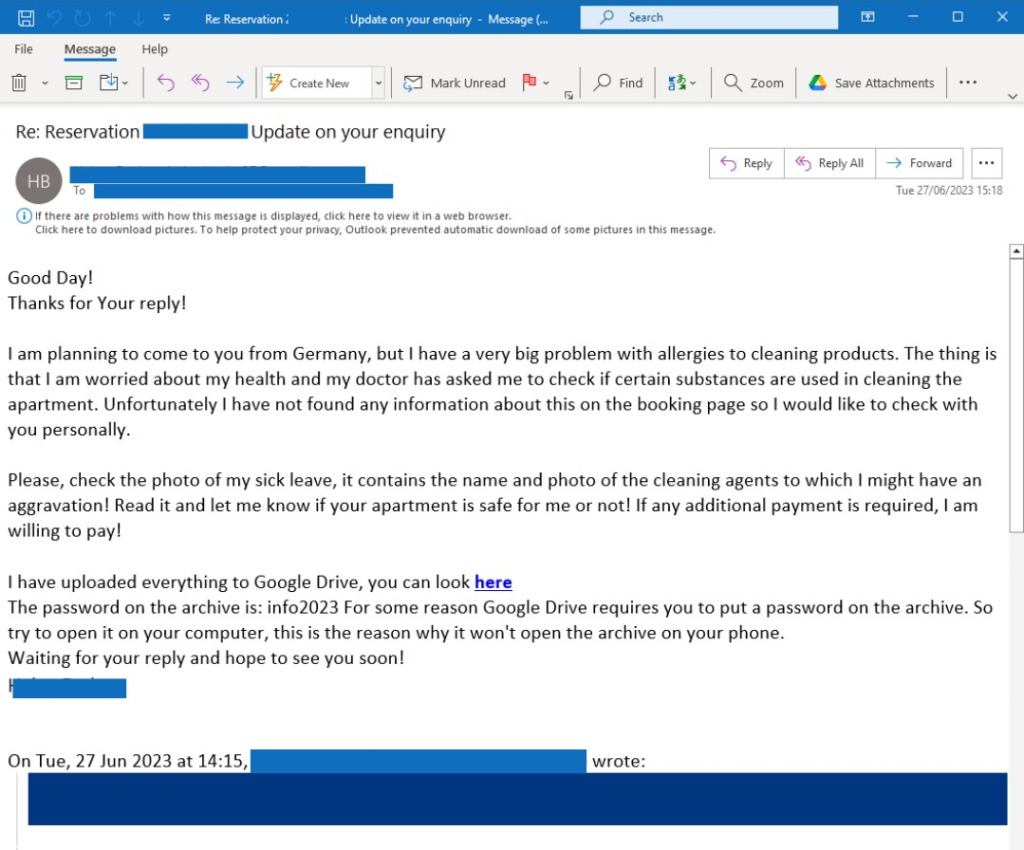
In a different example, a worried guest suffers from allergies to cleaning products
No Keycard Required: InfoStealer Unleashed
But here’s where the plot thickens: the URL doesn’t lead to any genuine documents. Instead, it directs the victim to an archive type file (filled with executable files) hosted on a common file sharing platform (Google Drive, DropBox, etc.). Once downloaded and opened on the victim’s endpoints, it unleashes Infostealer-type malwares that infiltrate the victim’s system, siphoning off sensitive data.
By the time the malware has been executed, it is often too late. The Infostealer malware is designed to operate stealthily, capturing login credentials, financial information, and other sensitive data without raising any immediate red flags. This makes timely detection and response crucial for mitigating the impact of the attack.
Check-In, Log-In, Steal Info: The Complete Attack Flow
To give you a clearer picture of how these attacks unfold, we’ve outlined a 10-step process that encapsulates the attacker’s modus operandi. This step-by-step breakdown serves as a roadmap, detailing each stage of the attack from initiation to execution.
- Initial Booking: The hacker makes an online booking, opting for free cancellation to minimize risk.
- Confirmation Email: An automated confirmation email is sent to the hacker.
- Crafting the Reply: The hacker uses this email to reply with a specific request or question about the reservation.
- Adding the Lure: A link to a file-sharing service is attached to the email, along with a plaintext password.
- Targeting the Victim: The email is sent either to the online booking service’s support or directly to the hotel.
- Clicking the Bait: The support representative opens the email and downloads the archive using the provided link.
- Decrypting the Archive: The downloaded archive is encrypted but easily decrypted using the provided password.
- The Deceptive File: Upon decryption, an executable file with a misleading name and a PDF icon is extracted.
- Triggering the Trap: The representative double-clicks the executable, unknowingly launching the malicious code.
- Data Exfiltration: The endpoint becomes infected, and sensitive information starts being transmitted to the hacker.
From Mini-Bar to Malware: What Makes This Campaign Different
Precision Targeting: This isn’t a scattergun approach. The attackers have done their homework, zeroing in on hotels and organizations in the hospitality sector. This level of specificity suggests a meticulously researched and executed campaign.
Emotional Manipulation: The attackers aren’t just relying on technical prowess; they’re exploiting human vulnerabilities, too. By weaving in scenarios involving family members with health conditions or specific needs, they tap into the victims’ empathy, effectively sidestepping rational scrutiny.
Multi-Step Interaction: Unlike typical phishing attacks that involve a single email, this campaign involves a series of interactions, making it more convincing. The password-protected archive adds another layer of perceived legitimacy, lulling the victims into a false sense of security.
Advanced Evasion: These aren’t the average InfoStealer executables. They come equipped with advanced anti-sandboxing techniques, effectively evading detection from even the most sophisticated sandboxes. Detection relies solely on threat intelligence and static signatures or Yara rules. Ingeniously, the files can recognize when they’re in a sandbox environment and self-destruct, thereby bypassing detection mechanisms.
Behavior
Emails are usually sent from generic domains [“gmail”, “outlook”, “yahoo”, “yandex”]
Emails involve words related to the reservations [“allergies”, “allergy”, “hotel”, “booking”, “reservation”, “guest”, ”medical”, “doctor”, “medical”, “illness”, “sick”, “wheelchair”, “allergic”, “compensation”, “unsatisfactory”, “dissatisfaction”]
Hosting services used [“drive.google.com“, “docs.google.com“, “filetransfer.io“, “gofile.io“, “cdn.discordapp.com“, “dropbox.com“, “mega.nz“, ”filedn.com”]
Archives used – [“7z”, “zip”, “rar”, “rev”, “bz2”]
File names contain words like [“allergy”, “hotel”, “report”, “medic”, “recommendation”, “information”, “requirements”, “booking”, “payment”, “confirmation”, “reservation”, “document”]
Exicons used in the campaign:
Malware families [“Vidar”, “StealC”, “Lumma”]
Fortifying the Front Desk: How Hotels Can Guard Against These Sophisticated Attacks
- Cultivate a Culture of Skepticism: Don’t just trust; verify. Always confirm the identity of anyone requesting sensitive information or access to internal systems. A quick phone call or secondary email can go a long way in establishing legitimacy.
- Empower Your Staff Through Education: Knowledge is your first line of defense. Ensure your team is well-versed in recognizing phishing techniques and knows the proper channels for reporting potential threats.
- Invest in Robust Email and Browser Security: Opt for an email security solution that comes equipped with anti-evasion and next-gen dynamic detection capabilities. This adds an extra layer of defense, making it harder for phishing emails and unknown malware to slip through the cracks. Robust protection of the organization’s enterprise browser can also be detrimental to stopping malicious downloads from affecting the endpoints.
Reach out to us for more information on how to secure your organization against advanced threats.
IOCs
SHA256 List [“7083e4774a68e23dd2f9239e5108f6615ff945a0673e7e975ab2ca2d4cb297d3”, “5365eb23e9dc4d3dc3c4eceae3266cbe586119c706c92c9a9902d7252ec73f83”, “9d1357bd8dab703f05ccac6bb5d3795a8ba5e5448e9b1dc7a7babef322d0fb98”, “5780ed8b0d40ad27404f10cd789f6b9e6bf58d78a046ad51a6bd9bb7c596989a”, “1a2e3bcc76ecc493d27592455fb947b5087d5a7497c317c59bca8b2b1b3223b8”, “762319e1763b8562091216c4d5ffa61f6045a982690d0e357b666d22ce439c82”, “0345b46e9e6785955bd4c6c1942a0e03d2403c77625b5124e5b73791c6b89034”, “b1cfc4b89b560fc11be26a216162162ceaace507b697954633d3229e34c4b178”, “c8ad5b16a404af9d88ba5b0caf01c08272659a07c2b8281da5e012f7f9e33a49”, “81dacd747676798317aab35e377aa0b368b708ba9369dcf26f971e6011b12610”, “fbfd2477b5502947fe25d5e434782f5cbe31ed479954d7b72379260d83a4252d”, “dc8cfd8478b22828a848f43b5d3c6582f94da8fe6ce0a2fa29dee575951fc945”, “b63d41c60aa52cae9806a4fe233d9a55b0c2dfdc67f215ab66c660503cc1a5f3”, “5196d0ce3bdb5504cfedd615c220d15cbd69315192348cae3b610ae15629c1bc”, “D5eb3924a89990cb0e7583376c02d9e1edcc3919e0a46b1c44be7c91f28fef0c”]
C2
45.9.74[.]92
5.42.64[.]28
94.228.170[.]65
81.19.137[.]220
188.114.96[.]0
78.47.122[.]222























