With the rise of sophisticated evasive threats and the commoditization of cyberattack kits, the need for advanced security solutions has never been more crucial. At Perception Point, we take pride in our commitment to staying at the forefront of innovation to address the evolving challenges of protecting the user’s modern workspace.
Our comprehensive approach secures your email, browser, and collaboration apps via a combination of a cutting-edge advanced threat prevention platform, powered by multi-layered threat detection engines, and an all-included managed incident response service, operated by in-house cybersecurity experts.
Today, we are introducing our latest breakthrough – the GPThreat Hunter™, a game-changing addition to our Advanced Threat Prevention security stack, powered by OpenAI’s latest GPT-4 model.
The Evolution of GPThreat Hunter
The Perception Point solution, equipped with AI-powered proprietary detection layers, already successfully identifies 99.95% of malicious cases. As an integral part of our solution, all customers receive a managed incident response service, composed of human cyber experts who handle false positives, hunt for false negatives, and analyze ambiguous and complex cases, all in record time of ~17 minutes on average per case.
In-line with Perception Point’s customer-first mindset, we are constantly looking for ways to further improve our service by handling ambiguous cases automatically and focusing our experts on the most complex investigations and cyber research.
Enter GPThreat Hunter™, an autonomous IR analyst that leverages the power of OpenAI’s GPT-4 model to automatically resolve a vast amount of ambiguous security cases without human intervention and with unprecedented accuracy and speed. This new capability is able to detect and prevent malicious items (e.g. emails) x100 faster than the average analyst, further improve the solution’s detection engines, unveil new attack tactics, and most importantly secure more human expert time for hardcore investigations, research and threat hunting.
How GPThreat Hunter™ Works
GPThreat Hunter™ is automatically activated when the system flags a case as ambiguous. It compiles a detailed context package, including the full text of the item in question, evidence from existing detection engines, and the algorithms that marked the item as suspicious. This package is then analyzed by custom multilingual LLMs that are continuously trained by Perception Point, and subsequently sent to the OpenAI GPT-4 model, which delivers an instant verdict along with a confidence score and a comprehensive explanation of its reasoning. The model also autonomously quarantines the threats and immunes the system against similar future attacks.
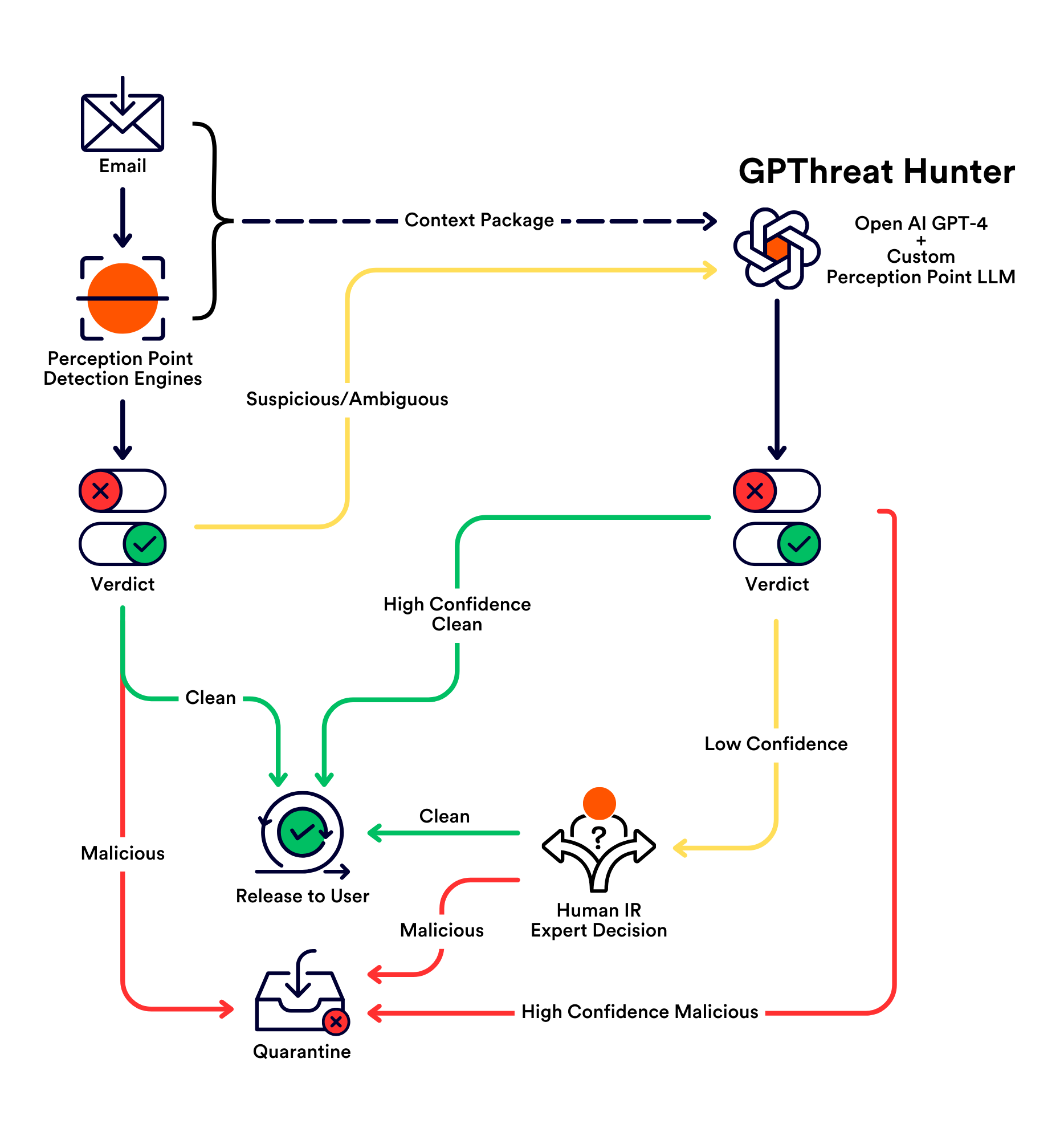
This innovative approach is made possible due to the extensive validated dataset that has been curated over several years by Perception Point’s incident response experts, which acts as the ground truth for tuning the model’s performance.
Private model hosting ensures that GPThreat Hunter™ operates with the highest standards of data privacy and security, in line with Perception Point’s commitment to protecting customer data.
The introduction of GPThreat Hunter™ marks a pivotal moment in our mission to deliver the most advanced security solutions to our customers. By harnessing the power of the GPT-4 model, we are not only enhancing our detection capabilities but also elevating our already stellar incident response services to unprecedented levels. Perception Point customers can now benefit from an even more efficient incident response service that focuses on the most complex cases where human expertise is irreplaceable.
Key Benefits of GPThreat Hunter
- Faster Remediation: Significantly reducing the time required to classify and remediate suspicious cases, providing quicker responses compared to average human analysts.
- Improving the Decision Engine: Enhancing overall detection accuracy and suggesting new algorithms based on newly discovered malicious cases.
- Better Human IR Service: Automating verdicts for ambiguous cases allows expert analysts to redirect efforts towards in-depth investigations, customer requests, threat hunting, and research.
- Enhanced Language Support: Adept at handling cases in various languages, expanding our coverage and protection.
- Explainability: Detailed explanations educate customer admins and end-users, fostering resilience against future malicious cases.
Future Enhancements
Our commitment to innovation drives us to continually develop future enhancements for GPThreat Hunter, including:
- Multi-Modality: Extending beyond text to include multi-modal input, such as images and screenshots.
- Agent Actions: Incorporating an agent component that can take real-world actions, like browsing URLs or researching entities mentioned in emails.
- Interactive Explainability: Offering users a fully interactive chat interface to discuss items with GPThreat Hunter.
At Perception Point, we are dedicated to pushing the boundaries and delivering the best cybersecurity solutions to protect the user’s workspace. GPThreat Hunter is a testament to our ongoing commitment to providing cutting-edge solutions for a rapidly evolving threat landscape.
I invite you to join us on this exciting journey as we continue to innovate and strengthen our cybersecurity solutions and help make every day a bad day for the threat actors.
Your security is our priority, and GPThreat Hunter™ is a giant leap forward in ensuring a safer digital future for all.
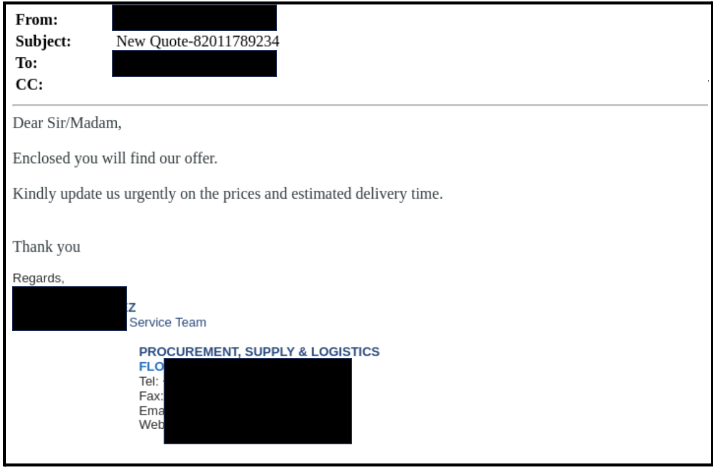
Examples
1. GPThreat Hunter: “The email is a phishing attempt to obtain sensitive information by disguising itself as a trustworthy entity. The email contains a URL payload and the subject of the email includes the organization’s name. The sender is impersonating a known brand’s domain and has a high malicious ratio. The subject also incriminates the email as malicious with a very high confidence score.”
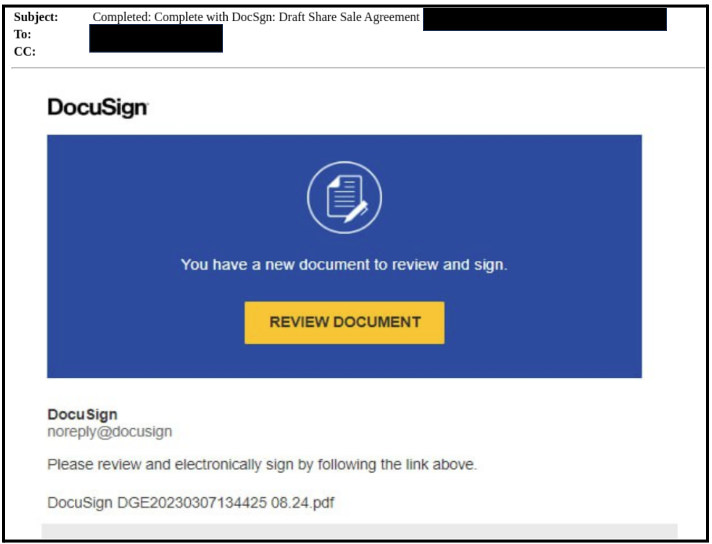
2. GPThreat Hunter: “The email is a potential phishing attempt, as it contains a suspicious attachment and the sender’s email address is not verified. The subject also seems unrelated to the content of the email, which is a common tactic used in phishing emails. The subject also indicates a high likelihood of malicious content.”