Combining Attack Vectors.
Perception Point intercepted an email thread that combined all currently trending attack vectors: impersonation, encrypted archive, and a malicious macro.
Impersonation
The sender requested something irrelevant of the company’s support team in order to seem like a real prospect seeking help.
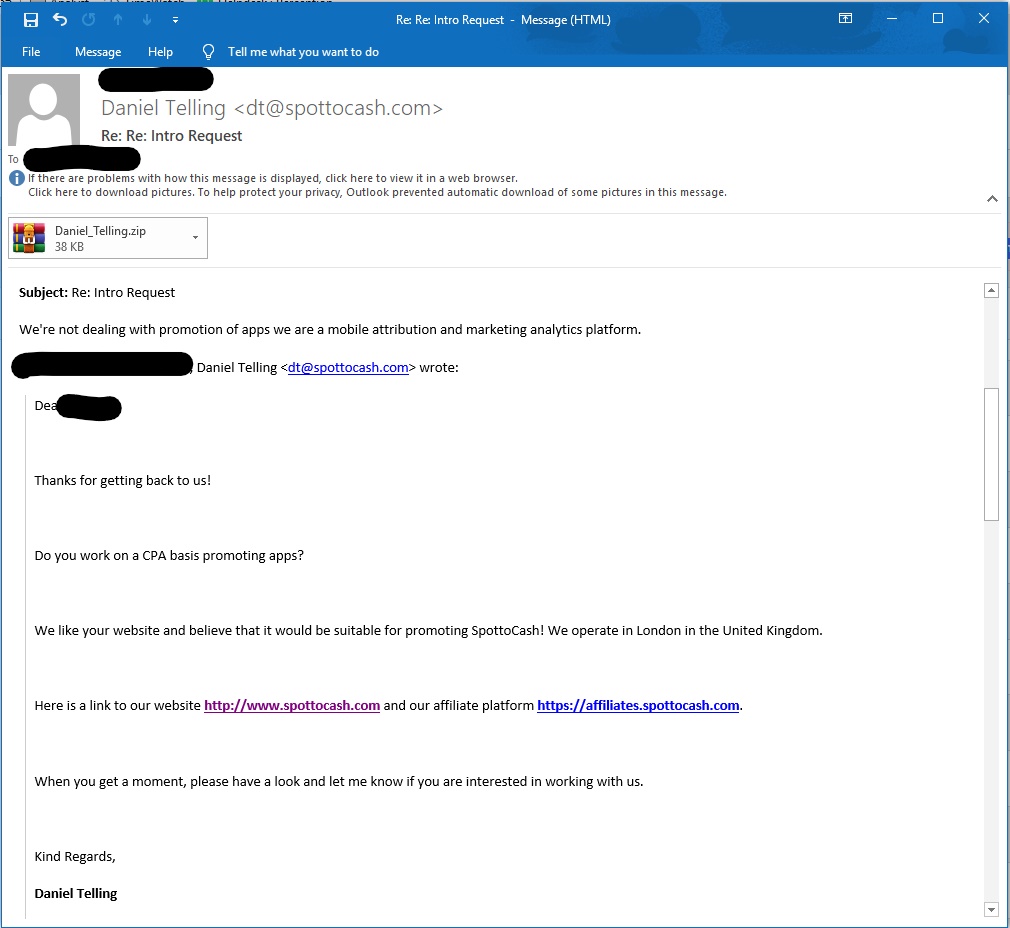
Encrypted File
.After the employee ended the conversation with the attacker. The attacker sent a suspicious zip file without any explanation regarding the file, plus he locked the file and added the password in the email causing it to be harder for detection engines to identify.
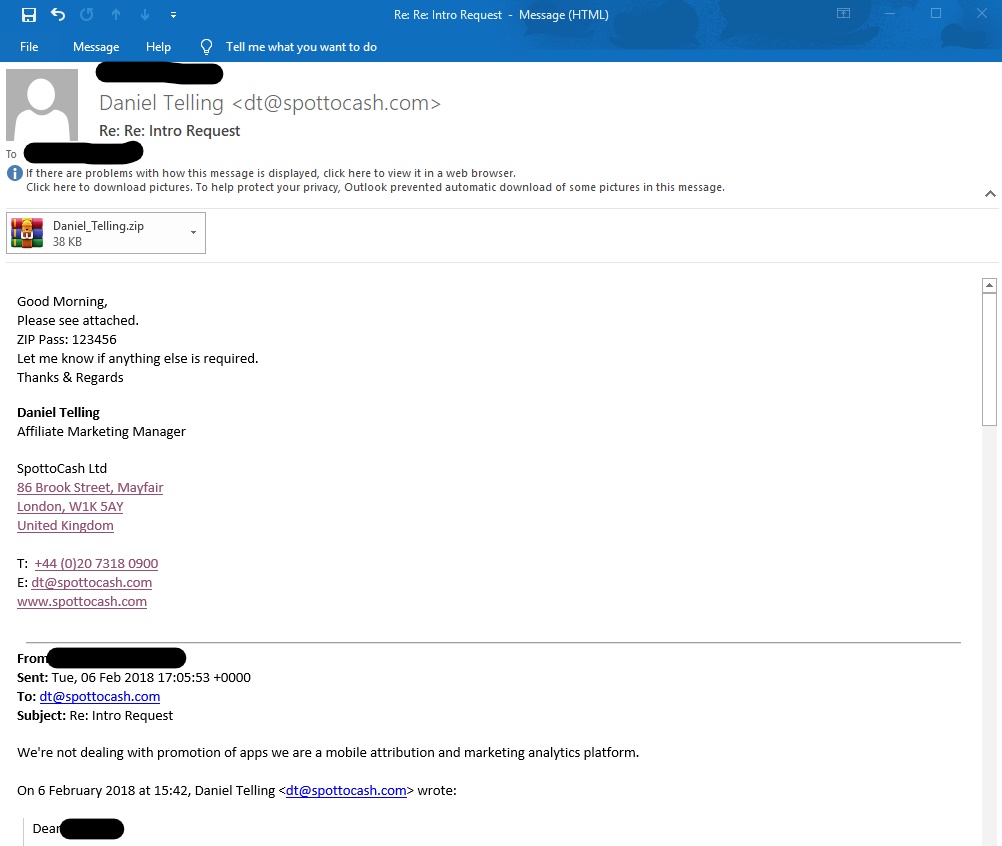
The zip contains a word document named “info05.07.doc”, using our password extraction mechanism, we managed to open the file and scan it.
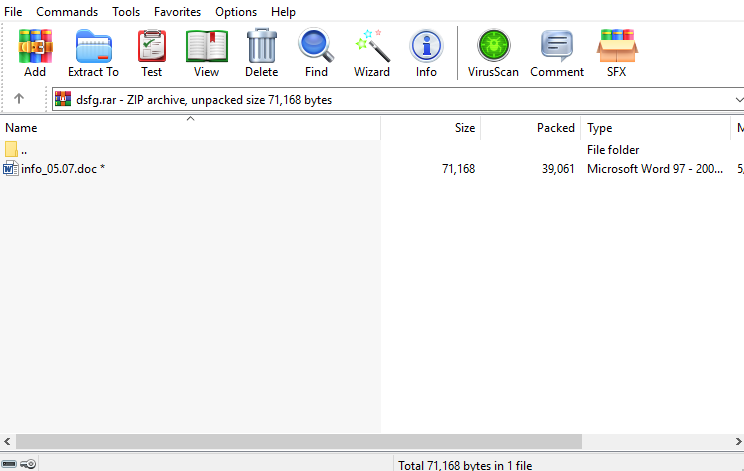
Malicious Macro
The doc file is malicious which contains malicious macro code that executes malicious commands without the users knowledge.
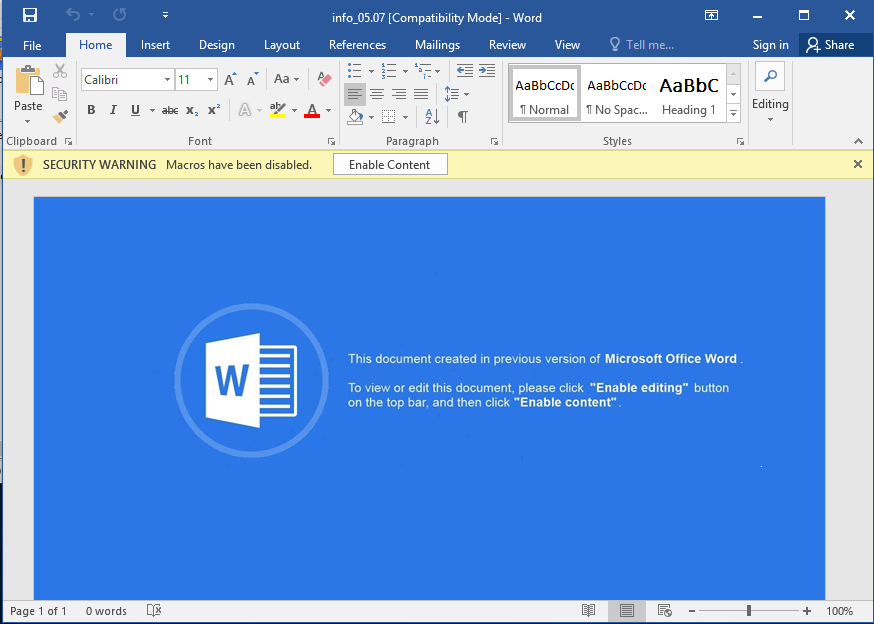
If the user enables the content or even if the configuration of the user enables the file to be opened with automatic activation (common situation) the file start running multiple malicious commands starting with running CMD and PowerShell.
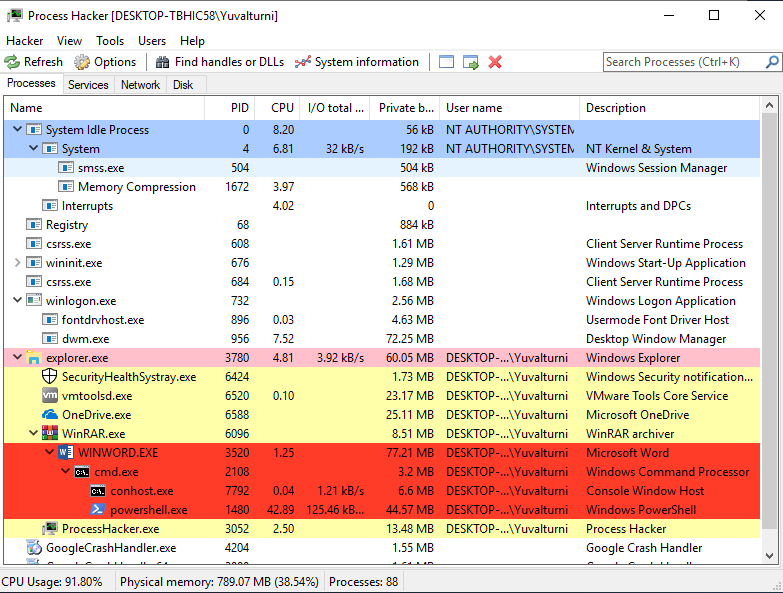
After the file executes his malicious activities the file is closed and tries to hide is activities by closing all the processes and actions he took.
Interested in learning about more attack trends like this one? See our resource page for additional reading material.























