In one of our previous blog posts, we have explored the perilous realm of QR code phishing (quishing) attacks, shedding light on their prevalence and the potential risks they pose to unsuspecting individuals.
As we diligently monitor security threats, a disconcerting trend has come to our attention: quishing tactics are evolving, becoming increasingly sophisticated and more challenging to detect.
Attackers are no longer limited to employing standard QR codes embedded in email bodies. Now, attackers are utilizing a diverse set of techniques to disguise malicious QR codes and circumvent security measures. These techniques include:
- Color Manipulation:
Attackers are now manipulating the color of QR codes, seamlessly blending them with surrounding text or backgrounds to increase their stealth. - Combining Multiple Tactics:
Attackers are using QR code phishing combined with other tactics, such as mimicking CAPTCHAs, MFA, and using two-stage phishing techniques. - Embedding in Multiple Formats:
QR codes are no longer confined to images; they are embedded within various formats, such as PDF documents, videos, and other file types, making detection more challenging.
In this blog we investigate some of these emerging evasion techniques used in quishing attacks. Read on to learn more.
Color Manipulation: Inverted Colors
One of the latest quishing techniques involves using a color-inverted QR code.
An inverted QR code is essentially a QR code that has reversed colors, with the background becoming black and the squares or modules becoming white. In other words, the dark and light elements of a standard QR code are switched in an inverted QR code.
By inverting the colors, attackers aim to make the QR code less recognizable and potentially evade detection by threat detection engines.

The inversion of colors disrupts typical QR code patterns, which may be employed by security mechanisms to identify and flag potentially malicious codes. This obfuscation contributes to the challenge of detecting and mitigating phishing attempts that utilize QR codes.
Combining Multiple Tactics: Multi-Factor Authentication
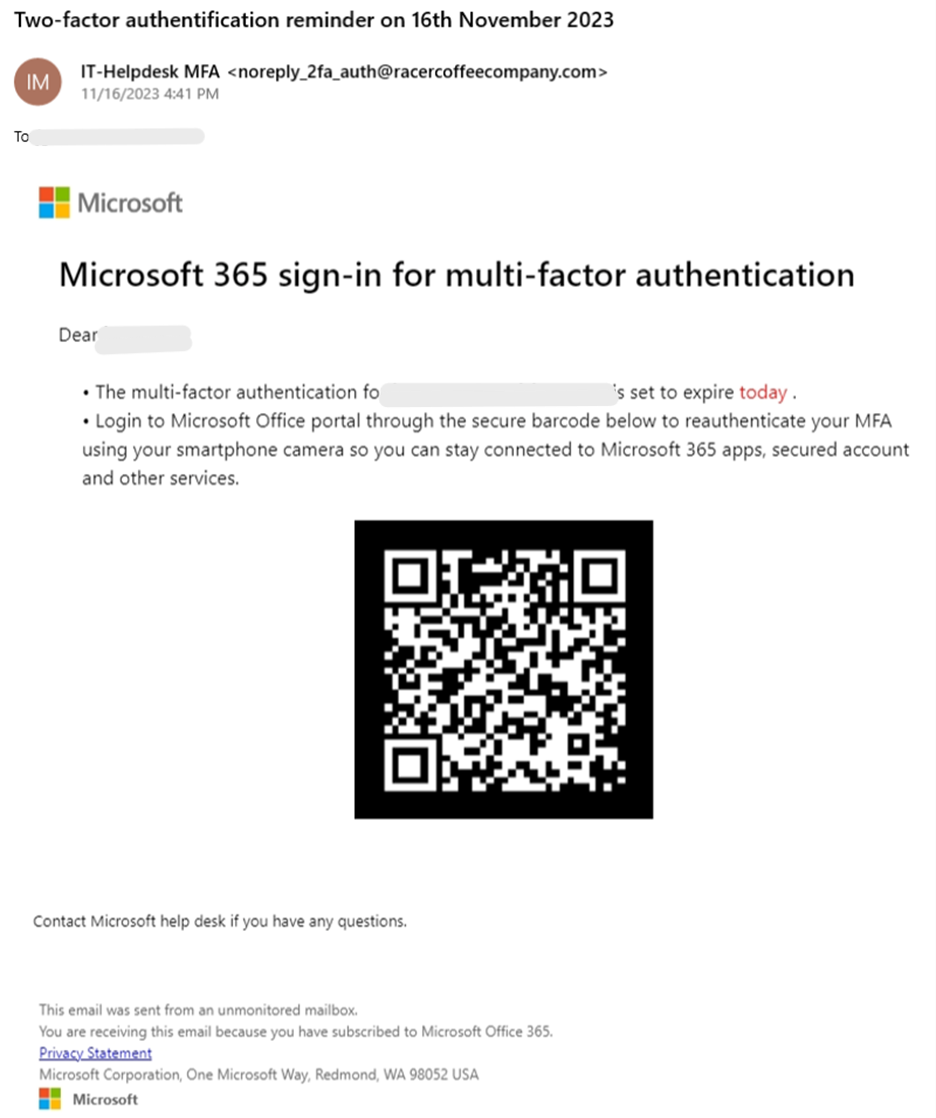
In this quishing variation, an attacker poses as Microsoft 365 and sends the target a fraudulent one-time password (OTP). The user is instructed to scan the included QR code as part of the authentication process.
Translating the QR code using a tool like QR Code Raptor shows that the code redirects the user to a deceptive two-factor authentication (2FA) “check”, hosted on an HTML page.
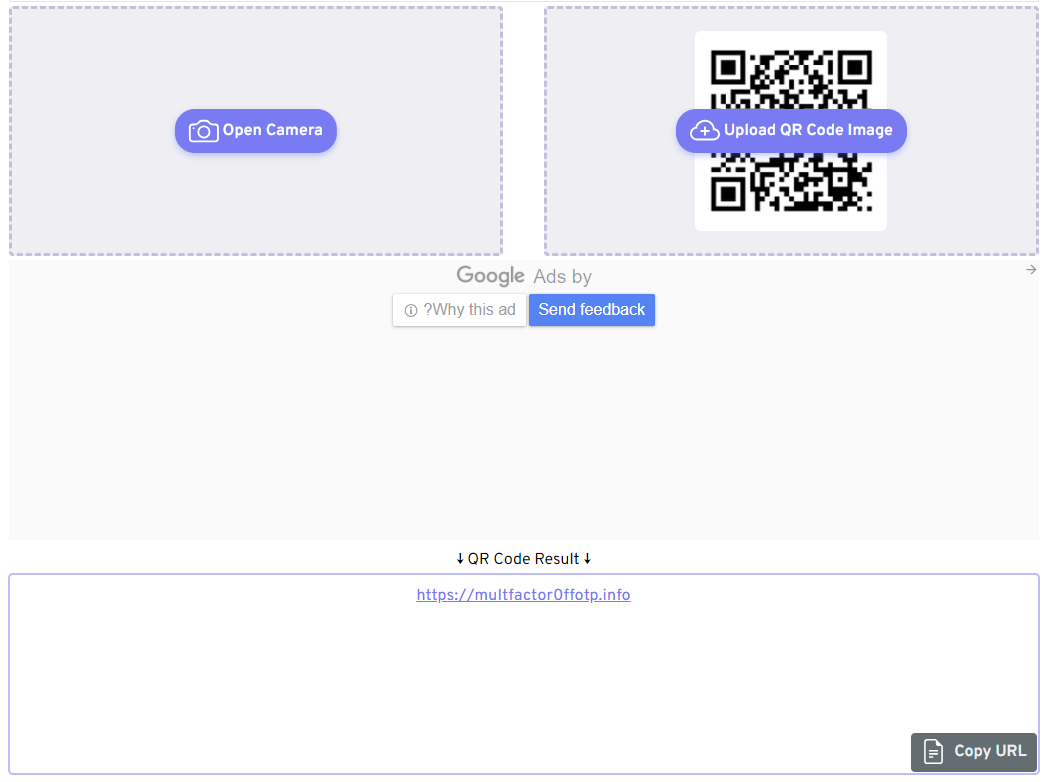
By including the intermediary step of a 2FA “security” check, the attacker aims to lull the user into the attack with an air of legitimacy and a false sense of safety.
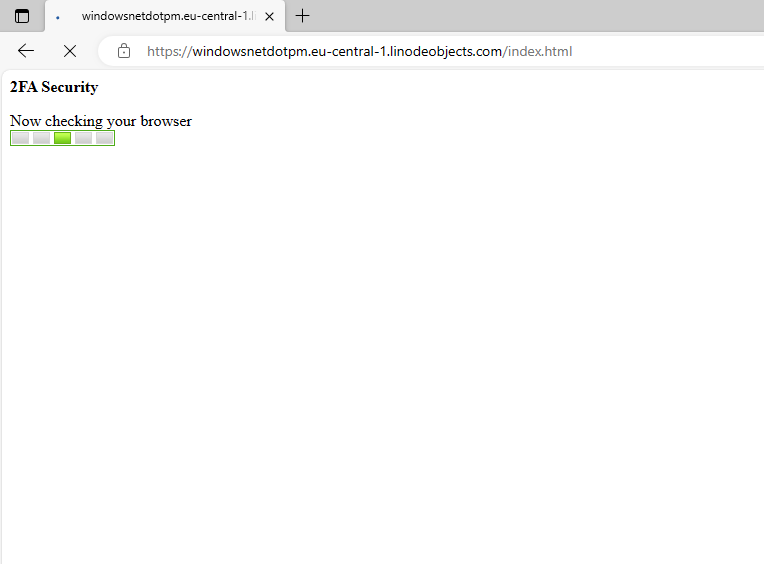
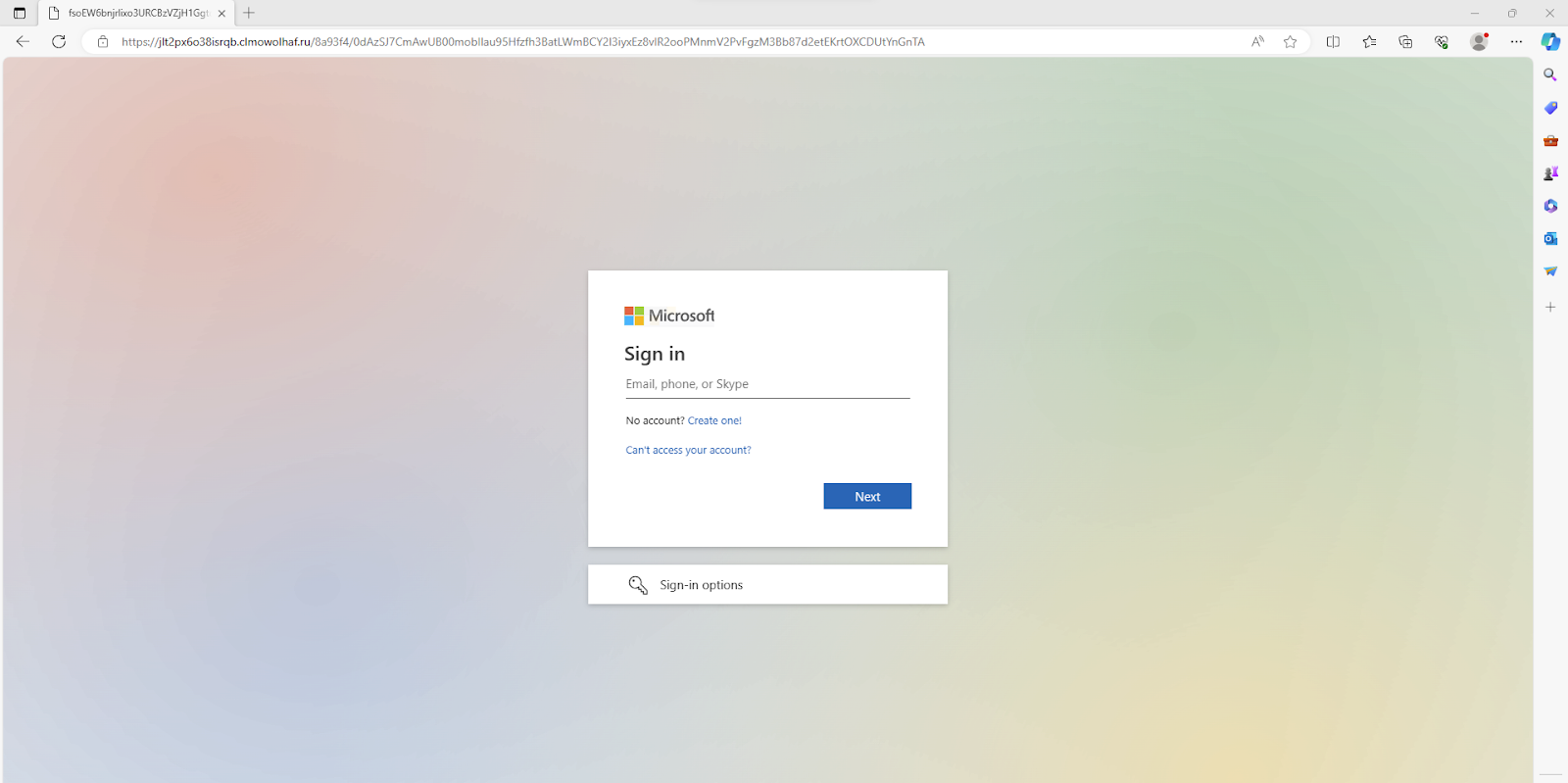
The 2FA page is then followed by redirection to a spoofed Microsoft login page, where the payload is revealed: the user is intended to enter their login credentials so the attacker can steal them.
Combining Multiple Tactics: Signing Off on Quishing
Here, a threat actor sends out an email, impersonating DocuSign. Users are urged to scan the QR code in the email with their phones in order to view their document. This serves as a way to avoid detection, shifting the user to their phones, which are less likely to possess the same security measures as their computers.
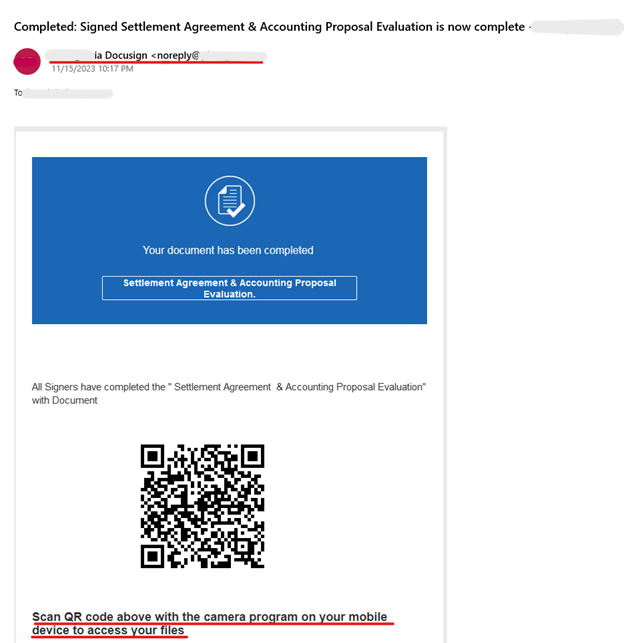
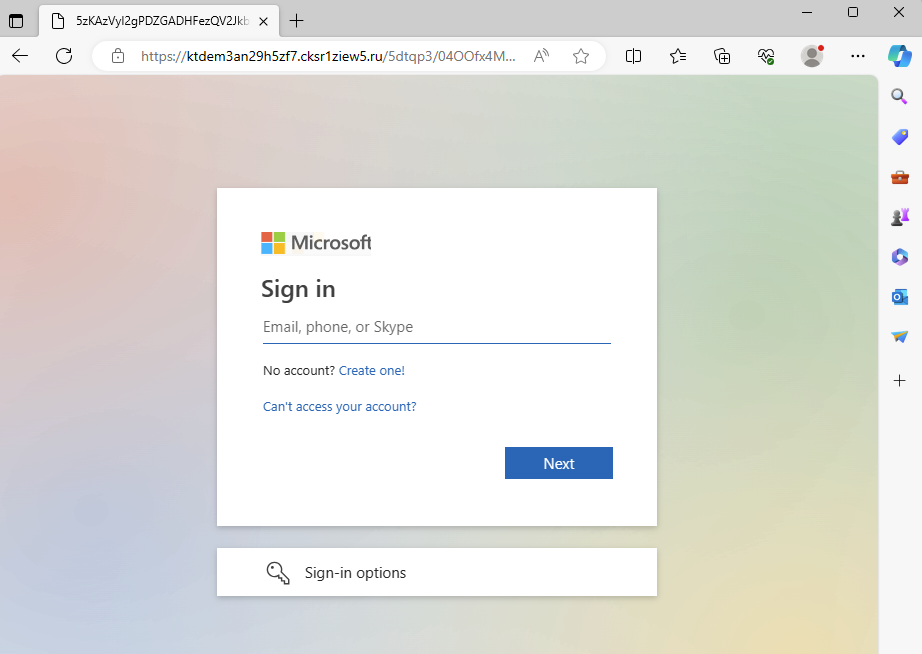
The QR code first directs users to http://www(.)security-0tp0ffice(.)info, which then redirects to a spoofed Microsoft multi-factor authentication page. To proceed, users are prompted to click on a button, thus engaging them in the second part of a two-step phishing attack.
Upon clicking the button, users are taken to a spoofed Microsoft login page, where if they enter their details, they can consider themselves successfully quished.
Combining Multiple Tactics: Captcha This!
A user receives an email, supposedly from Microsoft, with a QR code to authenticate their account.
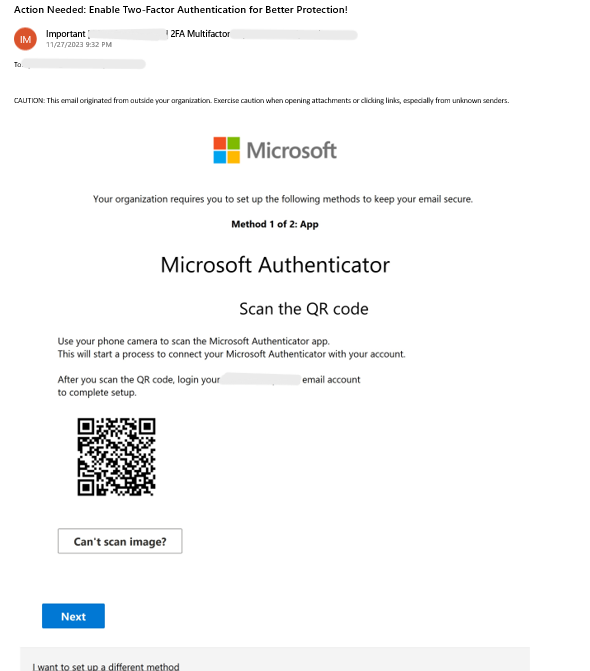
Scanning the QR code leads to a fake Cloudflare CAPTCHA. The attacker uses the CAPTCHA as a form of evasion, mimicking a legitimate security measure to disarm the target and potentially bypass threat detection engines.
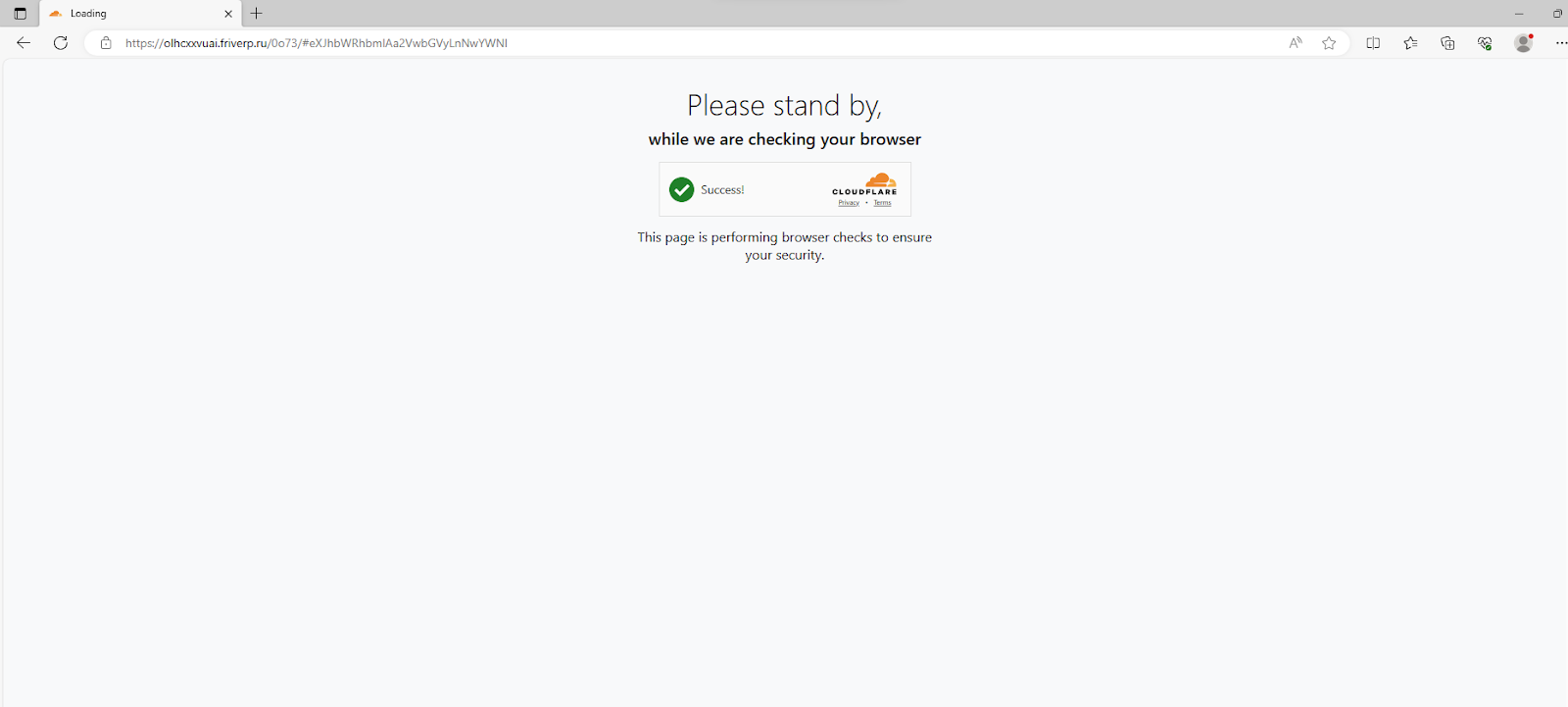
Following the fake CAPTCHA, the user is directed to a phishing site, impersonating a Microsoft login page.
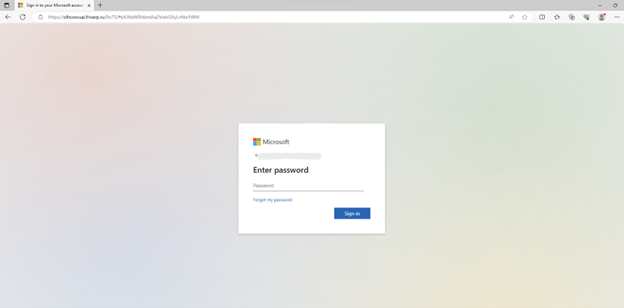
Embedding in Multiple Formats: Please See Attached
An attacker sends an email, impersonating the Human Resources department of an organization, using their name and logo. The email, sent from an iCloud account, contains a PDF attachment claiming to be the “upcoming payroll.” Within the PDF is a fabricated payroll summary featuring a suspicious QR code.
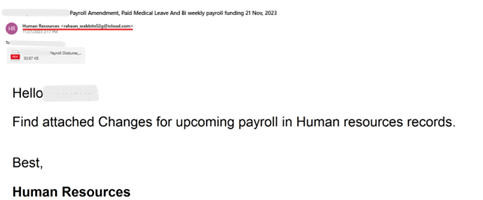

Upon scanning the QR code, it directs the recipient to a website and then redirects them to a secondary one. The redirected URL is concealed using base64 encoding, a technique employed by the attacker to obfuscate the true destination and evade detection.
Decoding the disguised URL shows that the redirect leads users to a fraudulent login page designed to impersonate the organization’s website. If a user enters their password, the attacker can effectively steal their credentials and potentially breach the organization.
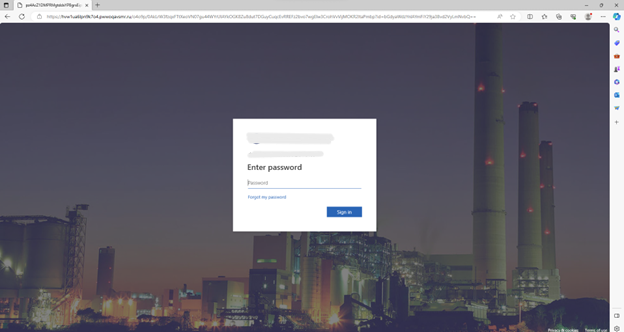
It’s in the HTML
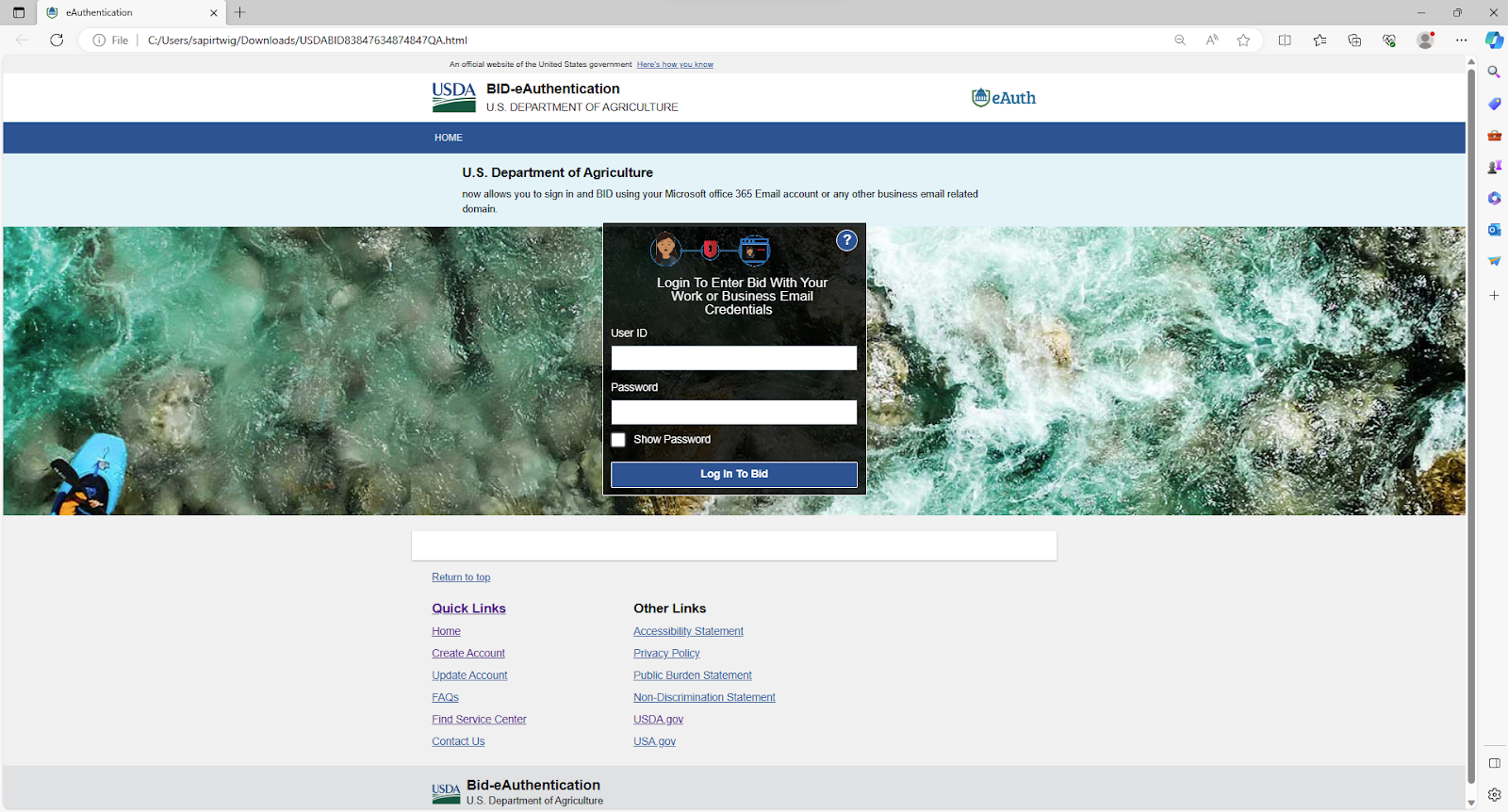
In this attack, the attacker poses as the United States Department of Agriculture (USDA), using the organization’s name and logo. Attached to the email is a PDF attachment, purporting to be an invitation to submit a tender.
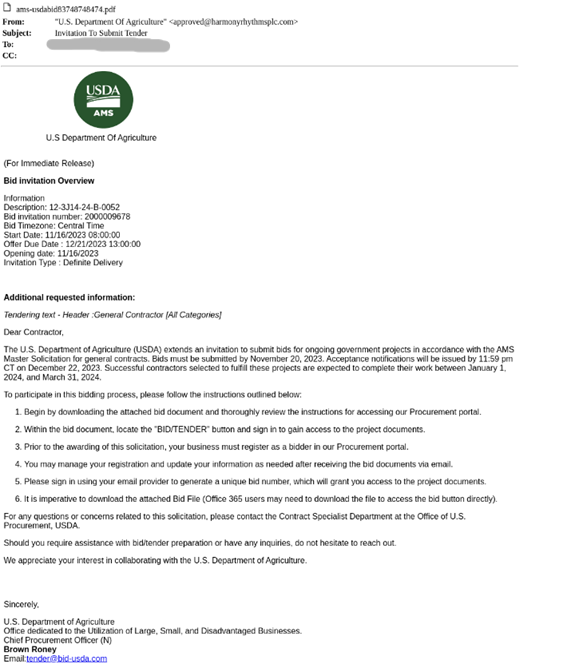
The PDF is a flashy flyer, encouraging contractors to bid on projects. The fake invitation contains two suspicious QR codes for the recipient to scan in order to register for proposals.

Scanning the QR code leads to the URL, which triggers the download of an HTML page.
Upon opening the HTML page, users are presented with a fake USDA login page. In order to submit a bid, they are instructed to login with their “work or business email credentials.” Navigating through this attack flow leads to a familiar payload: stolen credentials.
Addressing the Quishing Challenge
The evolution of these quishing tactics underscores the critical need for robust and adaptable security solutions to combat malicious QR codes. Effective security solutions require novel technology and functionality, including:
- Advanced Image Recognition & Computer Vision Models
Leveraging the latest image recognition algorithms to accurately identify QR codes, irrespective of color manipulation or resolution variations. - Combining Multiple Signals
Using multi-layered detection engines collaboratively to analyze the full context of emails and related entities to determine the benign or malicious nature of QR codes. - Multi-Step Phishing Analysis
Navigating to the QR code link website, to interact with its elements, and conduct an in-depth scan to uncover any hidden phishing forms.
At Perception Point, we are dedicated to staying ahead of the curve and continually refining our quishing detection capabilities. Our unwavering commitment to innovation ensures that Perception Point customers are not only protected against the latest quishing attacks but also fortified against the most advanced and evasive threats targeting user workspaces, including email, browsers, and modern SaaS applications.
As the threat landscape continues to evolve, so do our efforts to safeguard your digital environment. With Perception Point’s advanced phishing detection and quishing prevention, you can trust that your defenses are fortified against the latest techniques employed by malicious actors.
























