What Is Quishing (QR Code Phishing)?
Quick Response (QR) codes have become an integral part of our daily lives. However, with this increasing prevalence comes a new kind of threat: quishing.
Quishing, a portmanteau of QR code and phishing, is a fraudulent activity where attackers create malicious QR codes to steal sensitive information.
In a quishing attack, a user scans a QR code, thinking it’s from a trusted source, and is redirected to a malicious website or prompted to download malware. Typically, the attacker’s end goal is to trick the user into divulging personal information like credit card details or login credentials.
Quishing is a serious concern because it’s not possible for users to differentiate between a genuine and a malicious QR code (unlike traditional phishing attacks where there are often warning signs of an inauthentic message). More significantly, existing anti-phishing mechanisms rely on analyzing text and links within emails. In quishing emails QR codes are typically delivered as images, allowing them to bypass security systems.
In this article
How Do QR Codes Work? Static vs. Dynamic QR
QR codes are two-dimensional barcodes that store information in a machine-readable optical label. Originally developed for the automotive industry in Japan, QR codes have become ubiquitous due to their ability to store more data than traditional barcodes and their ease of use with modern smartphones.
A QR code consists of black squares arranged on a white background. These codes can hold various types of data, such as URLs, text, or other digital content. When scanned with a QR code reader or smartphone camera, the encoded information is quickly retrieved and displayed or processed by the device.
There are two main types of QR codes:
- Static QR Codes: Static QR codes contain fixed information that cannot be changed once the code is generated. They are suitable for use cases where the data does not need to be updated, such as linking to a website URL, contact details, or plain text.
- Dynamic QR Codes: In a dynamic QR code, the encoded data can be edited or updated even after the QR code has been created. This is achieved by embedding a short URL in the QR code that redirects to the actual content, which can be modified as needed. Dynamic QR codes provide improved analytics, such as tracking the number of scans, the location of the scans, and the devices used.

Tal ZamirCTO, Perception Point
Tal Zamir is a 20-year software industry leader with a track record of solving urgent business challenges by reimagining how technology works.
TIPS FROM THE EXPERT
- Employee Education and Awareness: Conduct regular training sessions to educate employees about the risks associated with scanning QR codes from unknown sources. Include information on how quishing works and what signs to look out for. Run awareness campaigns that highlight real-life examples of QR code phishing attacks and the potential consequences of falling for such scams.
- Implement Browser Security Solutions: Use browser security solutions that scan every website a user visits in-depth for potential phishing threats, regardless of their source. Enable automated warnings and blocks for suspicious or known malicious websites. This will help prevent employees from accidentally engaging with phishing sites, regardless of how they arrived at the URL.
- Use Special Formats or Digital Signatures for Official QR Codes: IT should establish a unique format or digital signature for all official QR codes used by the IT organization. This can include specific design elements, such as a company logo or a unique border, as well as digital signatures that can be verified.
- Deploy Mobile Security Controls: Implement Mobile Device Management solutions to enforce security policies across all company-owned and BYOD (Bring Your Own Device) mobile devices. Strengthen mobile browser security policies by disabling or restricting features that can be exploited by phishing attacks, such as pop-ups, auto-downloads, and scripts.
- Deploy Advanced Email Security Solutions: Deploy an advanced email security product capable of detecting and preventing various types of Quishing attempts. This includes scanning for embedded QR codes in emails and analyzing their destinations for malicious intent.
How Quishing Attacks Work: Methods and Techniques
Spoofing
Spoofing, in the context of quishing, involves creating malicious QR code that mimics a legitimate one from a trusted authority or brand. For example, the QR code might appear within a poster that uses a recognized brand’s logo and imagery, or it might be embedded in an email that apparently comes from a trusted vendor’s website domain.
In a QR attack based on spoofing, attackers take advantage of two trust elements: a user’s familiarity with a brand or organization, and their assumption that a QR code will always lead to a safe destination.
Creating a Sense of Urgency or Opportunity
Like in traditional phishing attacks, quishing attacks might use urgency or a missed opportunity, to cause a victim to scan a QR code without carefully examining it or considering the consequences.
According to a consumer warning issued by the U.S. Federal Trade Commission (FTC), here are common urgency tactics used in quishing attacks:
- Covering up the QR code on a parking meter with a malicious QR code. This exploits the urgency of paying for one’s parking and getting on the way.
- Sending a message saying a package could not be delivered, with a QR code to contact the sender or reschedule.
- Pretending there is suspicious activity on the victim’s account, and they need to confirm information to prevent the account from being frozen.
Fake Websites and Transactional Processes
Scammers are becoming increasingly sophisticated in their approaches, and this includes using meticulously crafted fake websites and processes in their quishing attacks. This method involves creating a scenario designed to trick the user into providing their sensitive information.
For instance, a user might scan a QR code that appears to be from the bank. It leads to a site that looks identical to the bank’s official website. The user is then prompted to enter their login details, supposedly to verify your account or update your security settings. The credentials are then sent to the scammer.
Redirecting to Fake Interactive Voice Response (IVR) Systems
A more advanced quishing technique involves redirecting victims to fake Interactive Voice Response (IVR) systems. This can be particularly effective because it mimics the behaviors of legitimate businesses. The use of a call instead of a website can create a false sense of security, making it more likely for the user to disclose sensitive information.
In a typical scenario, a user scans a QR code that purports to be from a well-known company. Instead of being taken to a website, they are connected to a phone number. The number will provide an automated voice system that requires the user to enter sensitive data such as a credit card number, a social security number, or bank account details. Attackers record the information entered by the user.
Quishing Impact and Consequences
Damage to Consumers
Quishing poses a significant risk to consumers, and can lead to financial loss and identity theft. For example, a consumer may scan a QR code in a public place, like a café or a bus stop, thinking it leads to a promotional offer. Instead, they’re directed to a fraudulent website where they’re tricked into entering their credit card details. This information can be used by attackers for unauthorized purchases or sold on the dark web.
Quishing can also lead to the compromise of personal accounts. For example, attackers might send a QR code by email, supposedly from a social media platform. The user is directed to a malicious site and asked to enter their credentials. The attacker compromises the credentials and uses them for identity theft.
Data Breaches
Quishing attacks can also lead to significant data breaches within organizations. Consider a scenario where an employee scans a QR code, believing it to be an internal survey from their employer. This QR code, however, is a quishing attack designed to capture login credentials. Once the attacker gains access to the employee’s account, they can move laterally within the organization’s network, accessing sensitive corporate data.
Scenarios like this can result in major data breaches involving customer information, trade secrets, and other confidential data. Such breaches not only lead to financial losses but also damage the organization’s reputation, compliance violations, and legal exposure.
Business Compromise
Beyond data breaches, quishing can be a gateway to more severe business compromises such as financial fraud and network infiltration. Consider a scenario where an attacker uses quishing to trick employees into making fraudulent financial transactions. For example, a QR code disguised as a vendor payment request could lead to a fake banking portal, resulting in funds being transferred to the attacker’s account.
Another high impact scenario is that an attacker could use a spoofed QR code to deliver ransomware into an organization. By sending a carefully crafted email to an individual with administrative permissions, the ransomware can spread across a network and lead to critical business data held hostage for a ransom.
Real-Life Quishing Attacks (with Screenshots)
Perception Point helps its clients detect and prevent quishing attacks on a daily basis. Here are a few real world examples we encountered.
1. QR Code Embedded within the Email Body as an Image
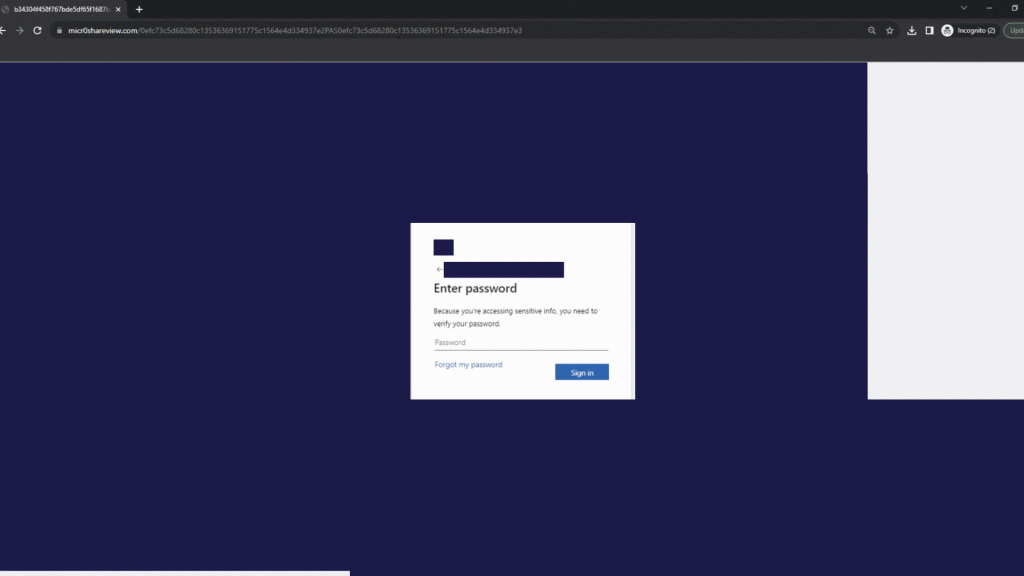
In this example, attackers sent an email that appears to be from a trusted company, Microsoft, with the subject line indicating a security update (e.g., “Multi-Factor Auth”). The sender’s display name mimics the company’s security team, such as “Microsoft MFA Security” with an email address like “[email protected].” The entire email body, including the text, logos, and QR code, is a single embedded image.
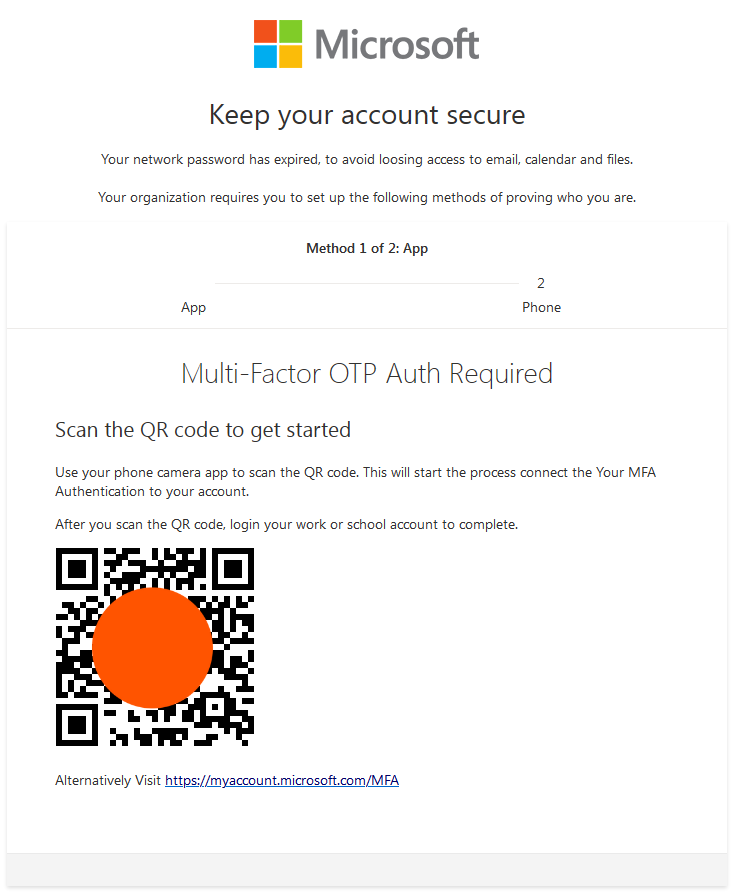
The email warns the recipient that their network password has expired and prompts them to scan the included QR code to connect an MFA method to their Microsoft account. Scanning the QR code directs the user to a fake Microsoft login page designed to steal their credentials. This technique exploits the trust users place in familiar brands and the urgency of security updates.
2. QR Code within a PDF attachment
In this example, the phishing email contains a PDF attachment and appears to be from the payroll department, with the subject line “2FA Salary Report for <NAME> Completed August 22, 2023.” The sender’s display name might be something like “Payroll UPDATE,” adding legitimacy to the message.
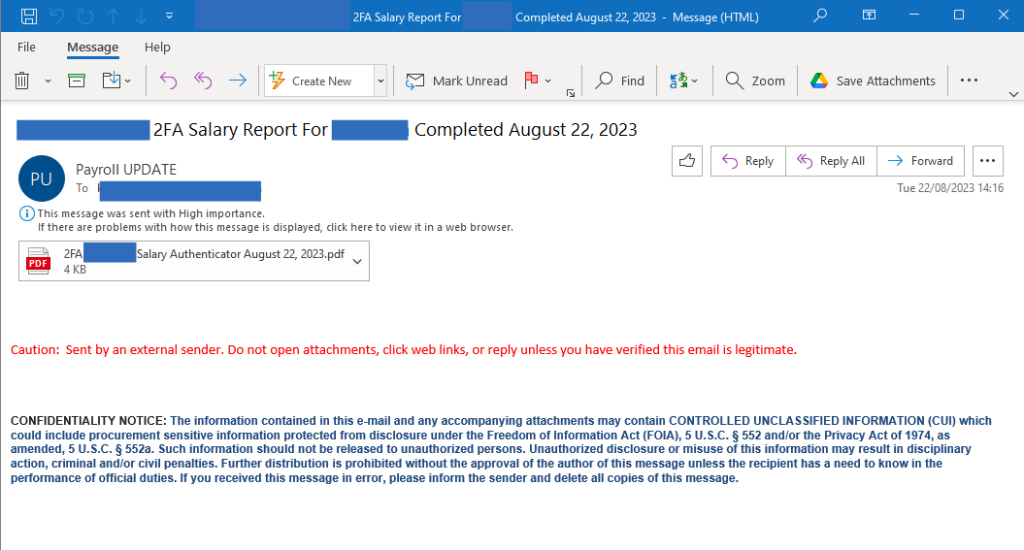
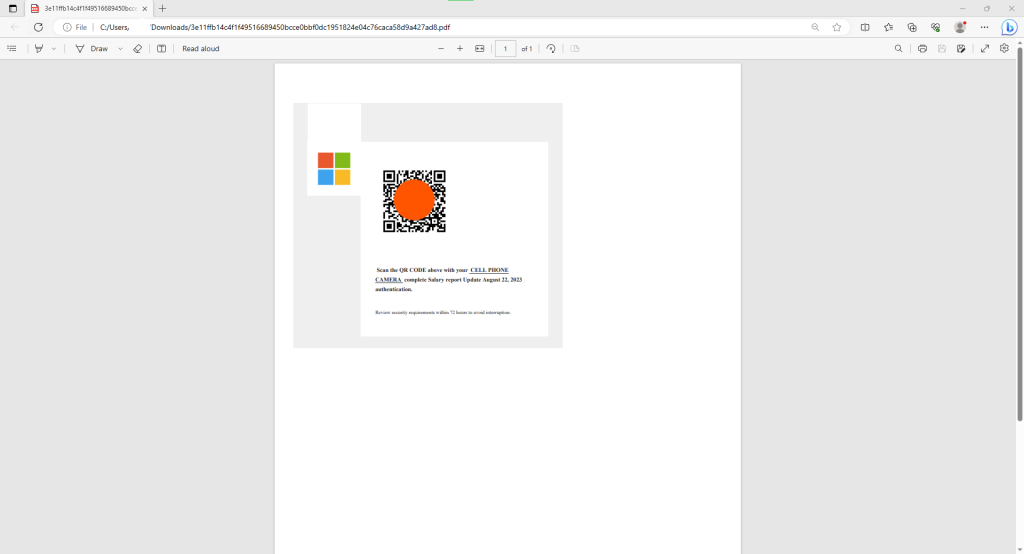
The PDF attachment, named “2FA <NAME> Salary Authenticator August 22, 2023.pdf,” includes a Microsoft logo, a QR code image, and brief instructions to scan the QR code with a cell phone camera to complete a salary report update.
Once scanned, the QR code redirects the victim to a fake Microsoft login form pre-filled with their email address. The attackers even use the target’s company logos to make the spoofed login form appear authentic.
Tell-Tale Signs of a Quishing Attack
It can be very difficult to detect sophisticated quishing attacks. But there are several indicators that can help users identify and prevent quishing attacks, and can help prevent at least some attacks.
Unexpected or Unsolicited QR Codes
Be cautious of QR codes that appear unexpectedly or are received without prior notice. These might be found in unusual places, such as on parking meters, public bulletin boards, or flyers handed out in busy areas. Attackers exploit the urgency of certain situations, like paying for parking or accessing urgent information.
Lack of Context, Unusual Placement or Presentation
Legitimate QR codes are typically accompanied by clear instructions or context about their purpose. For example, a QR code at a restaurant may be labeled to access the menu, or a QR code in a brochure might link to more detailed information about a product. Be wary of QR codes that lack this information or are presented without any explanatory text.
Additionally, check for spelling mistakes, inconsistent fonts, or low-quality printing that might indicate a quishing attempt. Similarly, QR codes that appear to be hastily added to printed materials or websites could indicate a potential quishing attempt.
Suspicious Sender
QR codes sent via email, text message, or social media from unknown or suspicious senders should be treated with caution. Verify the identity of the sender and the legitimacy of the message before scanning the QR code. Even if the message appears to come from a trusted source, such as a bank or a known contact, look for subtle discrepancies such as an unusual sense of urgency, unexpected requests, or language that doesn’t match the sender’s usual tone.
Use of URL Shorteners or Obscured Links
Be wary of QR codes that, when scanned, redirect you to URLs that are shortened or obscured.
If your QR code scanner app allows, always preview the full URL before proceeding. If the URL looks suspicious or doesn’t match the expected domain, do not proceed further.
QR Code Security: 4 Ways to Protect Against Quishing
If you are an individual, here are a few ways to avoid falling prey to quishing attacks. If you work for an organization, educate employees and users on these best practices to prevent quishing and safeguard your network.
1. Verify the Source of a QR Code
A first line of defense against quishing attacks is to verify the source of the QR code. If you encounter a QR code in a public place, ask yourself if it’s from a trustworthy source. If you’re not sure, it’s best to avoid scanning it.
Also, always verify the source of emailed or messaged QR codes. Cybercriminals often impersonate reputable companies in their phishing attempts. If you get an unexpected QR code from a company, contact them through their official channels to confirm its legitimacy.
2. Use a Reliable QR Code Reader
When choosing a QR code reader, look for ones that are created by reputable software vendors and have positive reviews. Some QR code readers could be malicious software distributed by attackers, or software that is not regularly updated and more susceptible to security vulnerabilities.
Also, some QR code readers have built-in security features. These features may include a warning system that alerts you when a QR code is linked to a suspicious website. Using a QR code reader with these security features can add an extra layer of protection against quishing attacks.
3. Preview the Destination URL
Before you scan a QR code, it’s important to preview the destination URL. This can help you identify potentially malicious websites. If the URL looks suspicious, don’t proceed with the scan. Make sure the URL is under a known domain name and is secure (starts with https://).
Here is an example of how to do this in a popular QR scanning app, QR & Barcode Scanner. After scanning the QR code, the application shows the destination URL, which in this case is under a reputable domain, nutella.com. Note however that the URL is not secure (starts with http:// without the ‘s’).
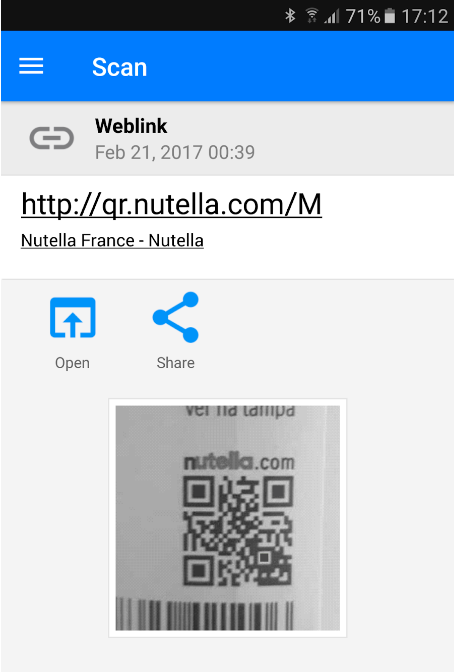
Furthermore, be wary of shortened URLs. Cybercriminals often use URL shorteners to hide the true destination of their phishing sites. If you encounter a shortened URL, use a URL expander to reveal the full URL before scanning the QR code. For example, Urlex is a free website that allows you to expand a short URL to view the destination URL.
4. Advanced Anti-Phishing Solutions
Anti-phishing solutions help protect individuals and businesses from malicious messages that attempt to trick users into divulging personal information, or cause them to visit malicious websites.
However, traditional anti-phishing solutions are blind to quishing attacks, because they are based on images, not text. Perception Point is one of the first email security solutions that addresses the quishing threat.
Perception Point scans all QR codes in messages before they are received by a user. It actually follows the URLs within them to identify if they are malicious. The solution uses image recognition and AI to detect and block quishing attacks at their source before they even get to the end users.
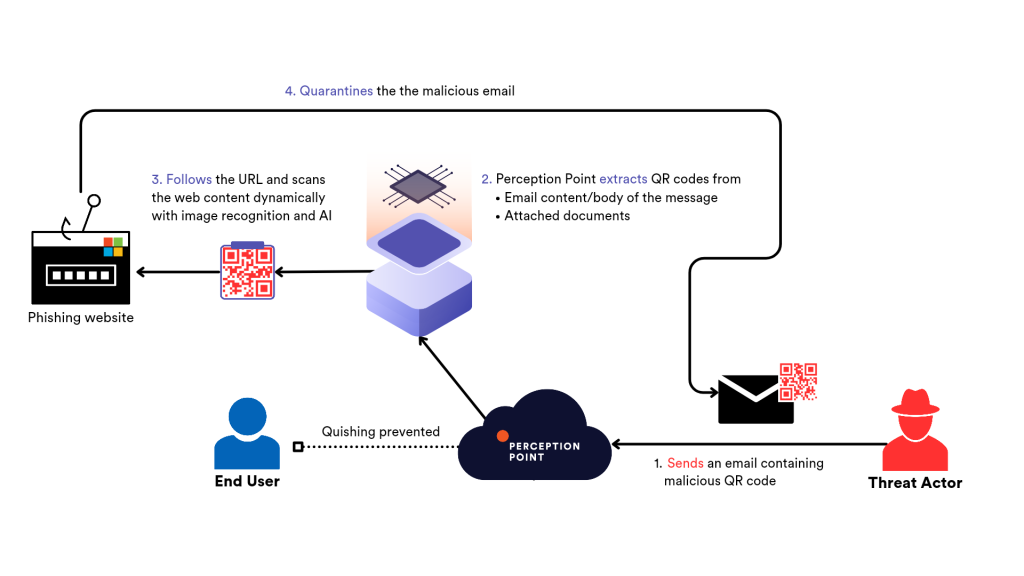
Using real-time image recognition models, QR codes are extracted from the body of the email or from attached images and documents (PDFs, Office files, etc.). A proprietary anti-evasion algorithm then follows the URLs to scan them dynamically for any phishing or malware delivery attempts.
Perception Point phishing detection technology consists of multiple AI and ML detection models including:
- Two-Step Phishing: object detection model examines webpages to recognize clickable elements for further scanning (evasion: end users are first presented with a trusted page, clicking an element within it redirects them to the malicious payload).
- Login Forms Detection: Computer vision models detect input boxes and login forms, crosscheck them with the URL and identify anomalies and prevent credential theft.
- Brand Recognition: Comparing email/URL/file screenshots/images/URL favicons to logos and visual assets of known brands to detect spoofing and phishing. The data is analyzed against known ‘clean’ images (e.g. official Microsoft logos) and known ‘malicious’ ones (impersonation attempts caught by Perception Point).
- Domain Lookalike and URL Lexical Analysis: S-GLocal algorithm incorporates heuristic biological algorithms and modifies them to identify domain lookalikes and impersonation attempts. ML model analyzes the URL structure to find similarities to malicious URLS and to predict whether or not the link is malicious.
- GenAI Decoder™: LLM-based model utilizes transformers to recognize the patterns in AI-generated text and detects malicious social engineering attempts in the email text.
Learn more about Perception Point quishing prevention

Quishing, a portmanteau of QR code and phishing, quishing is a fraudulent activity where attackers create malicious QR codes to steal sensitive information. In a quishing attack, a user scans a QR code, thinking it’s from a trusted source, and is redirected to a malicious website or prompted to download malware. Typically, the attacker’s end goal is to trick the user into divulging personal information like credit card details or login credentials.
QR codes, or Quick Response codes, are two-dimensional barcodes that store information in a machine-readable optical label. These codes can hold various types of data, such as URLs, text, or other digital content. When scanned with a QR code reader or smartphone camera, the encoded information is quickly retrieved and displayed or processed by the device. There are two main types of QR codes:
– Static QR Codes
– Dynamic QR Codes
If you are an individual, here are a few ways to avoid falling prey to quishing attacks. If you work for an organization, educate employees and users on these best practices to prevent quishing and safeguard your network.
1. Verify the Source of a QR Code
2. Use a Reliable QR Code Reader
3. Preview the Destination URL
4. Advanced Anti-Phishing Solutions