Thought Netflix scams were staying behind in 2020? Think again. The Perception Point Incident Response Team recently uncovered an interesting trend. It found 250% increase in the number of Netflix Phishing scams this quarter, with one widely used phishing kit is to blame.
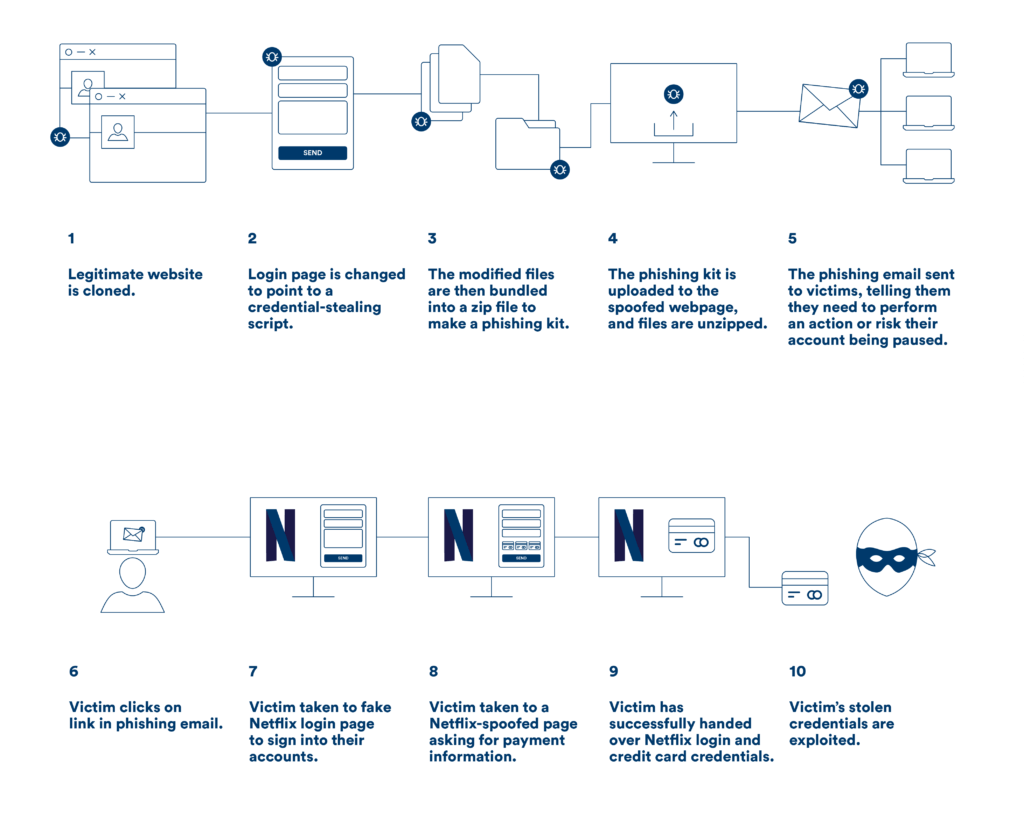
Netflix Phishing Scam Dissected
A deep dive into the data revealed an interesting story. Most of the attacks originated with one Netflix phishing kit. With nearly 151 million users worldwide, Netflix is the #1 streaming service in the world, which makes it a treasure trove for scammers to get data.
This Netflix phishing kit includes three different attacks. Each attack includes several layers with varying evasion methods.
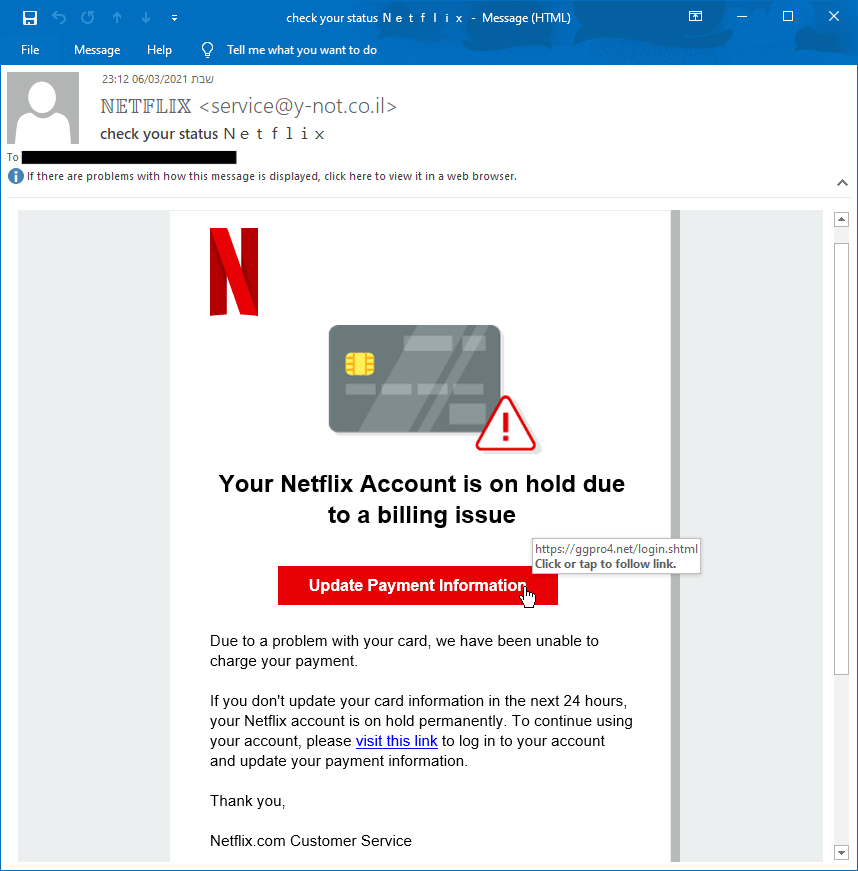
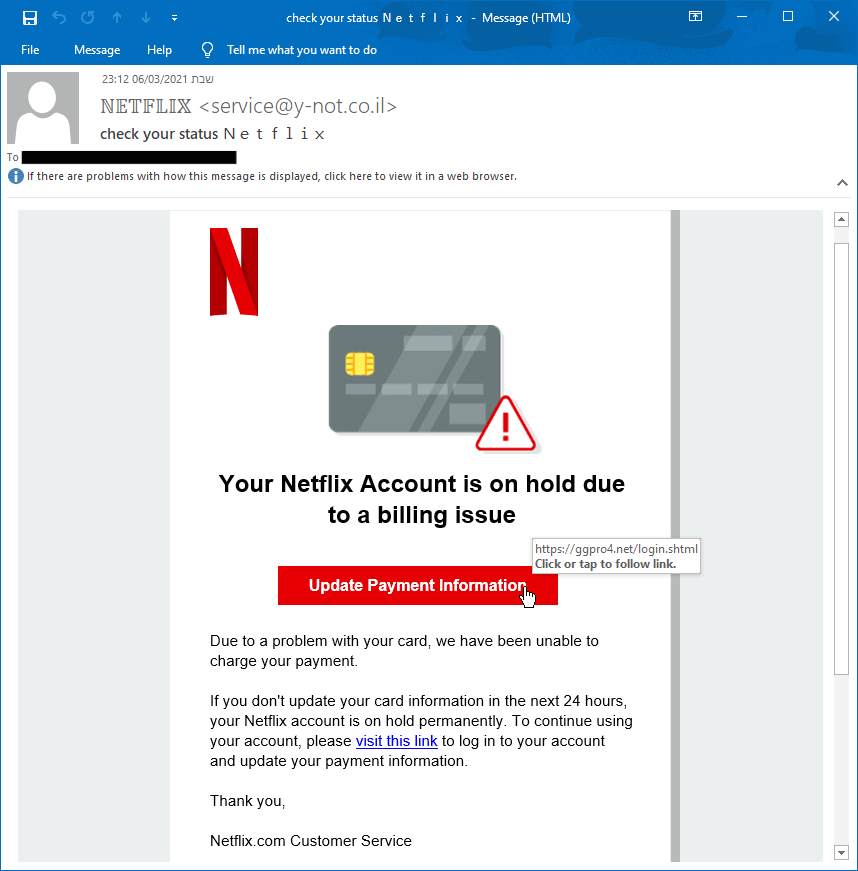
Stage 1. Pretending to be Netflix.
The attacker creates or uses a phishing kit to send an email pretending to be from Netflix. He or she does this by using the brand’s authentic logo and colors to gain legitimacy.
Deception Methods
- Brand Image. Netflix logo
- Email Colors. The exact Netflix color palette.
- Sign-Off. Netflix.com Customer Service.
Stage 2. Creating Fear
The content of the email creates a sense of fear and urgency by stating that the account is going to stop immediately unless the user takes action. When in a state of fear, people are more likely to take action (without much research first.)
Deception Methods
- Subject Line. “Check your status N E T F L I X.” The hacker is hoping the receiver won’t will not notice the spaces between each letter, which helps bypass legacy security tools.
- CTA. Update Payment Information
- Email Body. “If you don’t update your card within the next 24 hours, your Netflix account … “
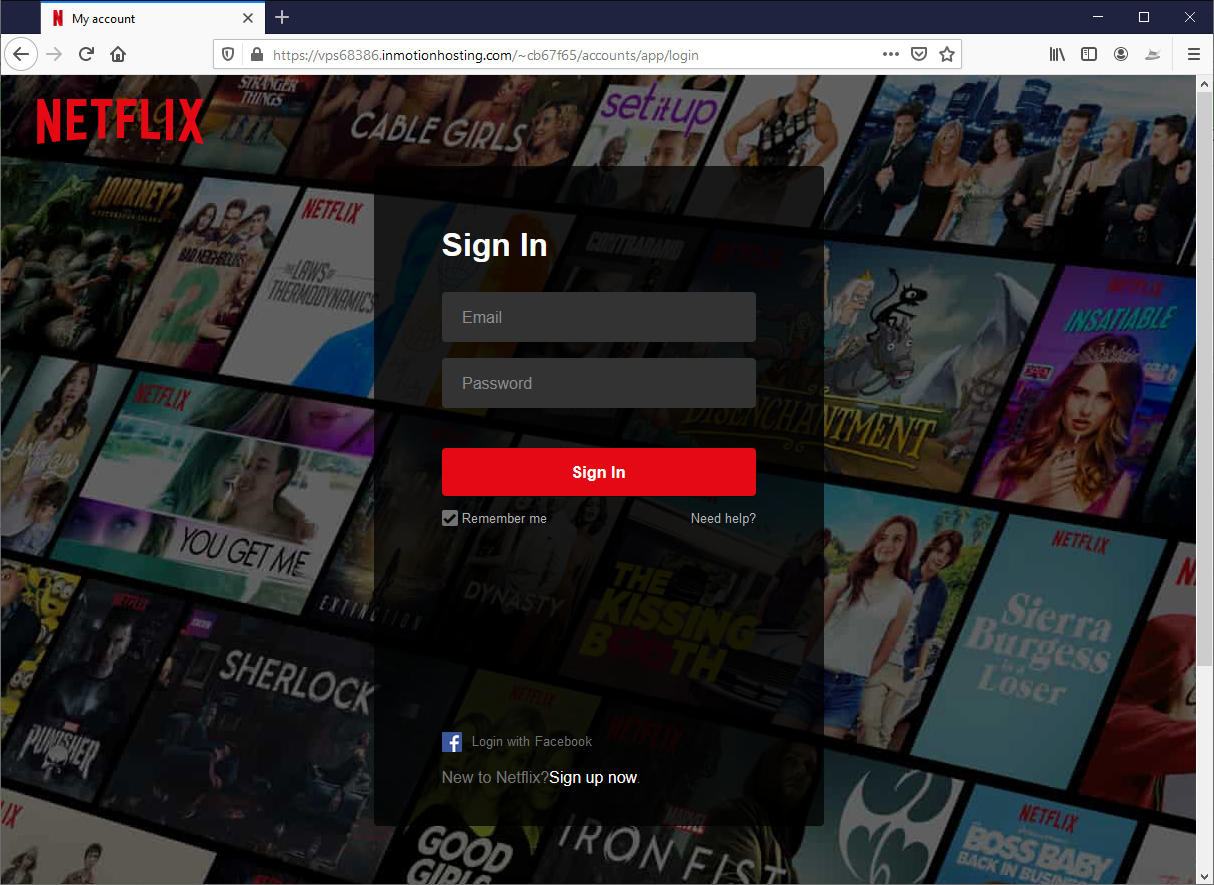
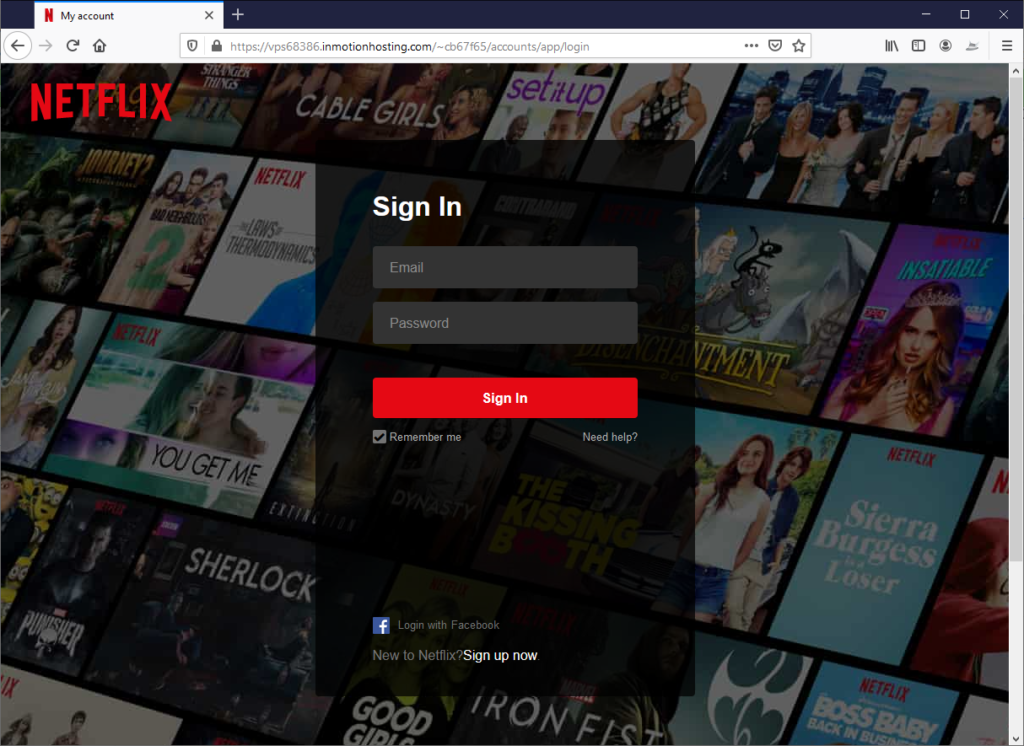
Stage 3. Robbing Netflix Credentials
Before users can update their credit card information, they must first sign in. As you can see, the attacker perfectly spoofed a Netflix sign-in page.
Deception Methods
- Legitimate cloud hosting. The phishing page hosted on the Inmotion Hosting service, which offers tools for WordPress, WooCommerce, Drupal, Joomla, cPanel, Magento, Jetpack, Prestashop, and WebPro Dashboard.
- Brand Spoofing. The Netflix logo is authentic and the website wallpaper mimics the look of a real Netflix login page. The hacker is banking on the fact that most people don’t think to look at the URL if the page looks legitimate.
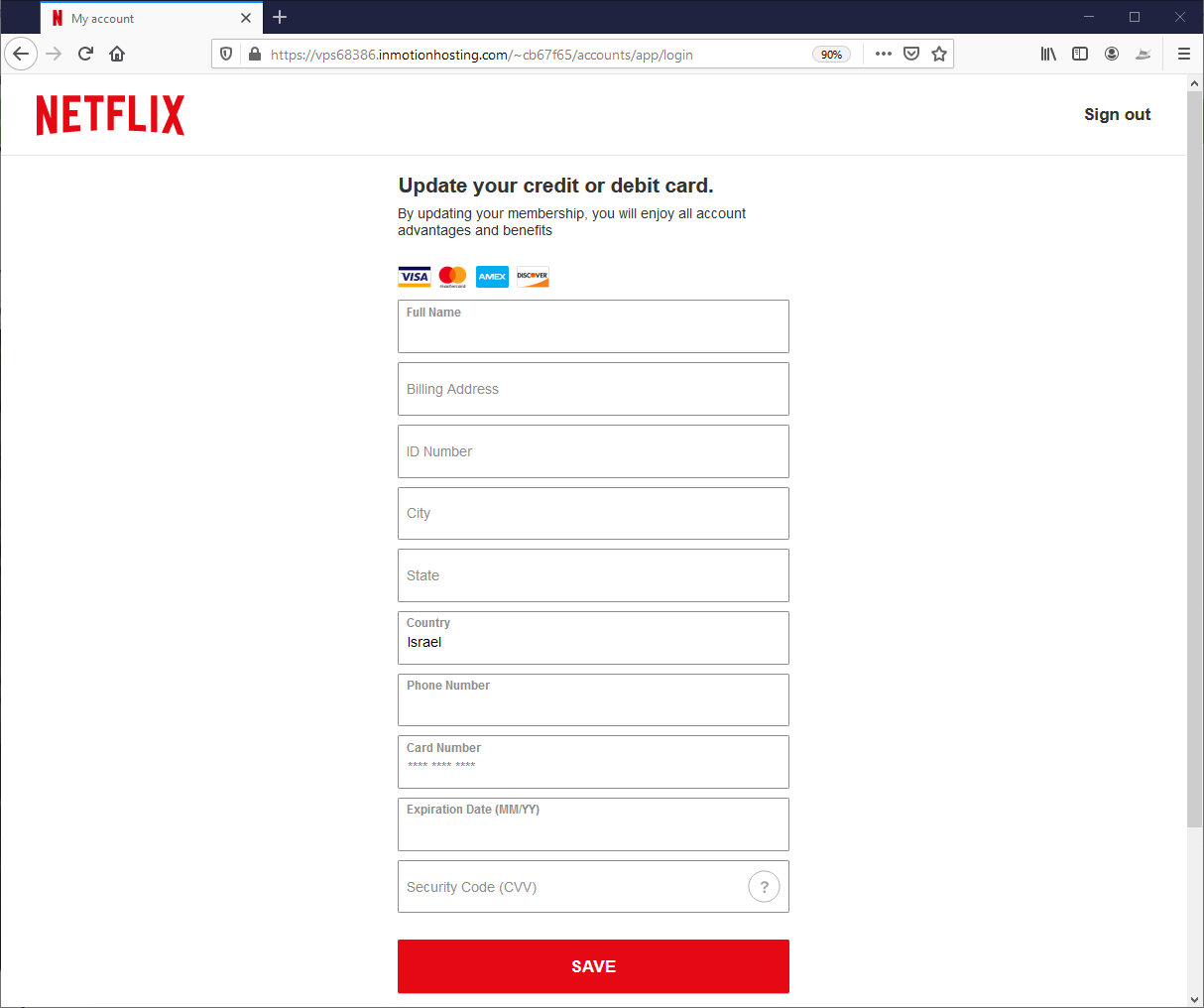
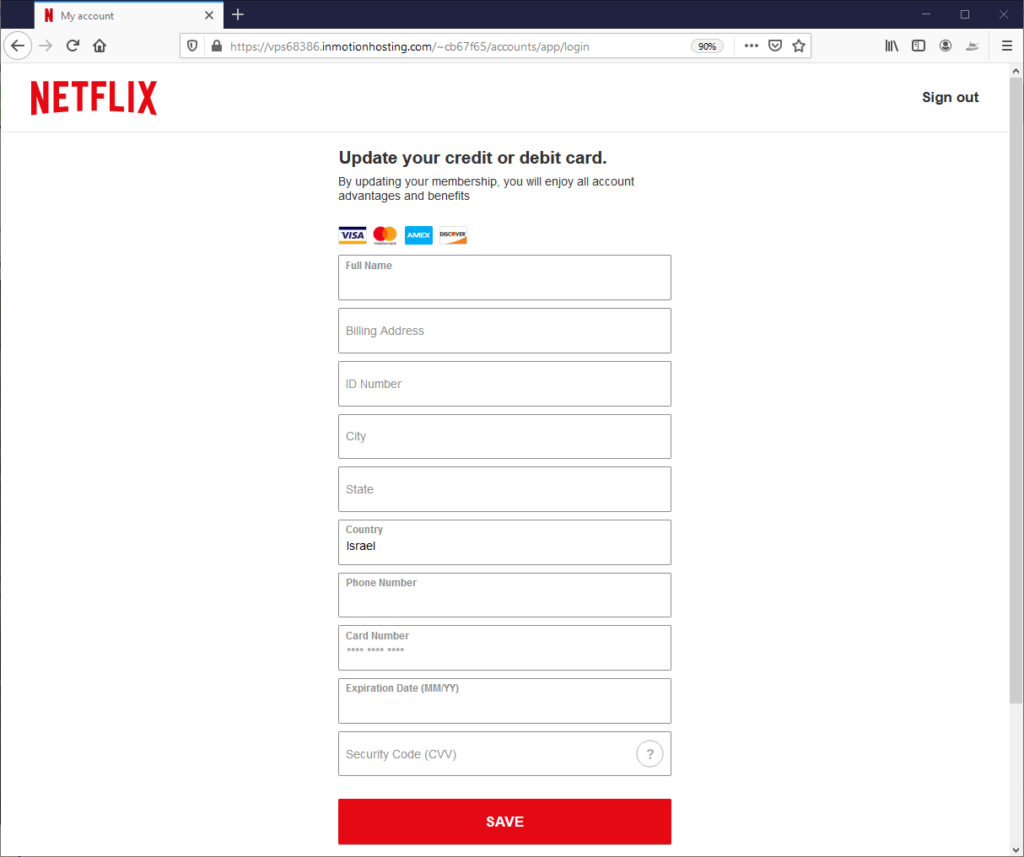
Stage 4. Stealing Credit Card Information
Once logged in, the user sees the payment page where he or she can insert their credit information.
- Legitimate cloud hosting. The phishing page is hosted on the same service as the the spoofed Netflix login page.
- Brand Spoofing. The page perfectly matches a real Netflix page by using the Netflix logo and brand colors.
Phishing Kits Explained
Attackers with minimal programming skills can create massive malicious campaigns with these tools.
How They’re Found
Would-be criminals get access to the tools by going to a marketplace (on the darknet) that offers them as packaged products, so it works in much the same way any other eCommerce site operates.
How They Work
Attackers get to pick from a variety of product variants, add them to their shopping carts and pay, and bam, the criminal has a ready-made kit that you can use to create a phishing campaign.
The kits include: the phishing email, malicious links, hosted spoof landing pages and evasion techniques. These evasion measures include:
- HTML character encoding
- Content encryption
- URLs in attachments
- Inspection blocking
- Content injection
- Legitimate cloud hosting
- more
The Rise of the Phishing-as-a-Service Industry
Thanks to phishing kits and Phishing-as-a-Service (PhaaS), anyone can be a cybercriminal. This new industry comes with subscriptions and varying levels of service, therefore the technical barrier no longer exists, so new users can use professional phishing tools at an affordable price. They get access to the tools by going to a marketplace (on the darknet) that offers them as packaged products.
These PhaaS service has two offers:
- One-off turn-key phishing attack kits. (These can cost as little as $50, according to Hashedout.)
- Full-service subscriptions. on average. these kits cost between $50-80 per month, according to Hashedout.)
Here’s why they are here to stay.
Lucrative
The price of phishing kits skyrocketed last year by 149 percent and exceeded $300 per item. The price depends on their complexity, quality and number of phishing pages, according to Group-IB, but the most disturbing one is the addition of value-added services such as “technical support” also factor into the prices.
Many kits even offer feature updates, user support, tutorials and community forums for scammers to share notes, and new features may be new languages, new targets, or even new obfuscation methods that attempt to limit detection.
High Demand
The number of phishing kit sellers active on underground forums increased by over 120% in 2019 year-on-year, which is relatively the same growth showed in the number of online ads posted on web resources.
Phishing will continue to be a growing threat in 2021 because criminals continue to exploit the fears and needs of people using their favorite services from their homes.
Perception Point Catches All Evasion Methods Used in Phishing Kits
Content needs to get dismantled and dissected before delivery. Our tools proactively assess every layer to catch all deception methods. It does not matter to us if attackers develop new evasion techniques and attack methods.
Here’s how we do it:
We combined four layers of anti-phishing prevention, which include propriety engines developed to outsmart all advanced phishing attempt. They include:
Recursive Unpacker. Unpacks the most deeply embedded phishing attacks, even if highly concealed by the attacker. Learn more.
Image-Recognition Engine. Uses several advanced image-recognition algorithms to validate if any URL is a legitimate site. Learn more.
URL-Reputation Engine. Incorporates data from the four top URL reputation engines. Learn more.
Threat Intelligence. Leverages intelligence from external security vendors and the cyber community. See more.























