It is no secret that cyber threats are evolving with alarming speed and sophistication. Among these, Vendor Email Compromise (VEC) represents one of the most insidious and challenging threats to detect and prevent. A subset of Business Email Compromise (BEC) attacks, VEC exploits the trusted relationships between businesses and their vendors, leveraging compromised accounts to orchestrate fraudulent activities that can lead to significant financial and reputational damage. The FBI IC3 reported that the average cost of a successful BEC attack is more than $125,000.
Vendor email compromise occurs when an attacker gains control of a vendor’s email account. Once compromised, the attacker uses the hijacked account to impersonate the vendor and send fraudulent emails to clients and partners. These emails often request changes to payment details, issue fake invoices, or attempt to initiate wire transfers.
In this blog, we investigate how an innovative attacker tried to steal over $650,000 from the same organization with seven different VEC attempts.
Initial Compromise
One of our customers was in the process of settling a payment with their supplier. The supplier sent our customer an email, containing an invoice for their services worth over $300K. What the vendor did not know was that this was the exact moment an opportunistic hacker was anticipating.
Before this email exchange began, a few things had happened in the background, unbeknownst to the vendor.
First, the attacker had gained access to the vendor’s account. This likely occurred through a successful phishing campaign. Once inside, the attacker then began the reconnaissance phase, monitoring email traffic to understand the vendor’s communication patterns, financial transactions, and key contacts. During this stage, the attacker waited for the perfect opportunity to exploit the vendor’s business relationships.
Joining the invoice thread, the attacker posed as the vendor and sent a follow up email to our customer, requesting a change in payment details (VEC Attempt #1).
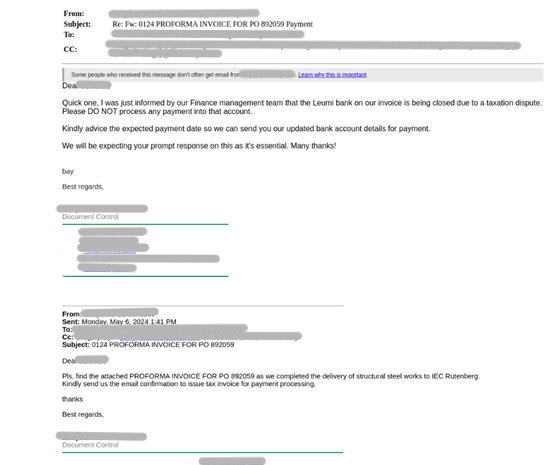
While the email itself may appear ordinary, a closer look reveals that all of the vendor-associated domains had been replaced with lookalikes. The attacker created a new domain that changed “ou” to “uo” to impersonate the vendor and hijack the thread.
Escalation
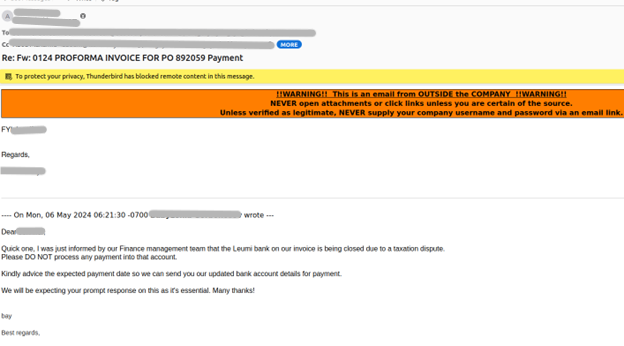
The attacker’s first attempt to hijack the thread failed. This prompted them to forward the fake change in payment request to the customer again, but from the vendor’s legitimate email account (VEC Attempt #2). Using the vendor’s compromised account ensured that the sender had a high reputation, unavailable with newly created or generic (i.e. Gmail) domains.
The attacker then sent another message, attaching the original invoice with altered bank details (VEC Attempt #3).
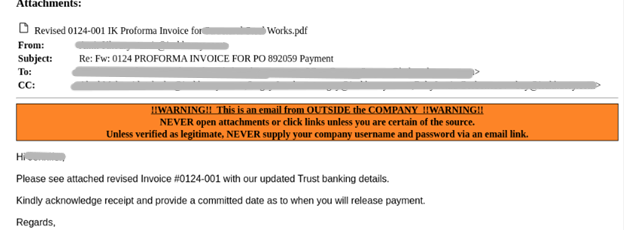
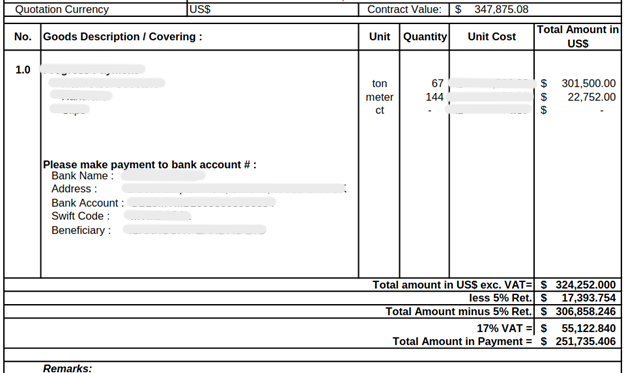
Follow-up Attempts
The first three attempts to defraud our customer were unsuccessful, so the attacker tried again, jumping on a new opportunity to hijack an invoice-related thread. This time, the invoice was for $350K.
Using the same tactic from the initial attempt, the attacker asked for a change in payment method. This request came from another lookalike domain, replacing the “i” in the vendor’s name with an “l” (VEC Attempt #4).
The attacker sent the same invoice again with different bank information enclosed (VEC Attempt #5).
These attempts yielded no success, prompting the attacker to create an additional mailbox with the initial domain lookalike (“uo” instead of “ou”). In the new message, the attacker claimed that due to changes in personnel, all financial matters should now be directed to the sender’s email (VEC Attempt #6).
In a seventh final attempt, the attacker created a Gmail account to impersonate the vendor, pleading once again that all financial matters refer to the included sender address (VEC Attempt #7). On the seventh try, the attacker struck out.

Defense Mechanisms in Action
Perception Point’s Advanced Prevention platform is designed to safeguard customers against sophisticated vendor email compromise attacks. AI-powered, multi-layered detection engines work in parallel to ensure that even the most deceptive tactics are identified and neutralized. Let’s look at some of the key detection methods employed by Perception Point to thwart these VEC attempts:
- Business Partner Recognition: Detects impersonations of known business partners of customers by running advanced similarity algorithms.
- Thread Hijack Detection: Detects very similar email domains used in the same thread.
- Machine Learning (ML) Large Language Models (LLMs): Detects anomalies and suspicious requests using trained models and AI algorithms.
- Extensive Reputation and WHOIS Data: Serves as a strong indicator in catching VEC/BEC emails by using databases to evaluate the legitimacy of email domains.
- Cross-Verification of File Origins: Detects when the same file is sent from multiple different senders to the same recipient—a significant red flag for fraudulent activity.
Together, these advanced detection methods form a robust defense against the sophisticated methods used in VEC attacks.
Taking Proactive Email Security Measures
Proactive measures are essential in identifying and mitigating threats before they can cause significant harm. Regularly updating security protocols, training employees, and using advanced detection technologies can substantially reduce the risk of vendor email compromise and other cyber attacks. Here are some other practical steps we recommend taking to secure your organization:
- Verify Payment Requests: Always verify changes in payment instructions through a secondary communication channel, such as a phone call to a known contact.
- Implement Advanced Email Security Solutions: Use solutions like Perception Point that offer comprehensive protection against sophisticated threats.
- Establish Clear Policies and Procedures: Develop and enforce policies for handling sensitive information and financial transactions.
- Conduct Regular Security Audits: Regularly review and assess your security measures to identify and address potential weaknesses.
- Regularly Update and Patch Systems: Ensure that all software, including email clients, is regularly updated to protect against known vulnerabilities.
- Educate Employees on Cyber Threat Tactics: Conduct regular training sessions to help employees recognize and respond to social engineering attempts.
- Use Strong, Unique Passwords: Encourage the use of strong, unique passwords and change them regularly.
Seven Strikes, You’re Out!
Despite the attacker’s persistent efforts, Perception Point’s unparalleled threat prevention capabilities ensured the protection of the customer’s financial assets. The vendor, impressed by the platform’s effectiveness and the support provided, chose Perception Point as their email security provider. This serves as an important example that even the most determined attacks can be thwarted with the right security measures in place.
Book a demo to learn more about how Perception Point can protect your organization!
























