Overview
Over the last few weeks, we’ve seen an increase in spoofing attempts to Geek Squad that involve “phone scams” with the goal of gaining access to the victim’s computer to hack an organization.
In this article, we will present this sophisticated fraud which starts via email and continues with a phone call to a “call center.”
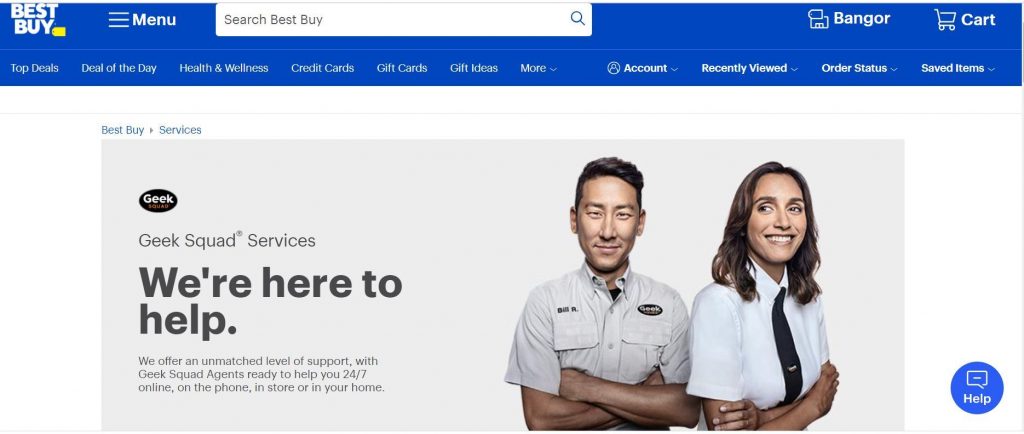
Geek Squad is a subsidiary of American and Canadian multinational consumer electronics corporation Best Buy. The company offers various computer-related services and accessories for residential and commercial clients. Geek Squad provides services in-store, on-site, and over the Internet via remote access, and also provides 24-hour telephone and emergency on-site support.
In this campaign, the attackers spread fake subscription invoices in multiple forms and ask you to call them in order to cancel the payment. They built an entire call center and use over 10 different phone numbers that lead to the same place.
Examples of Emails Sent
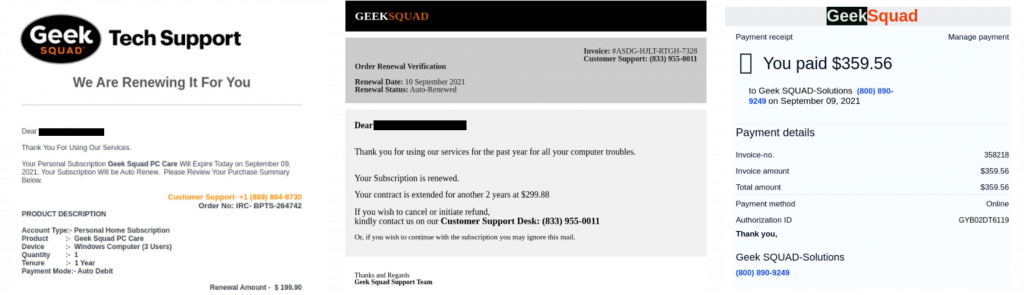
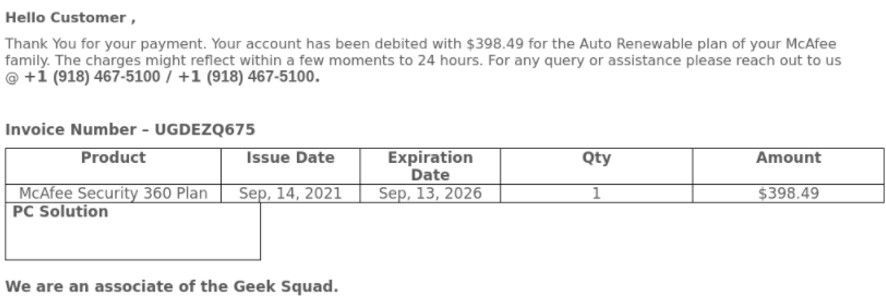
The Scam Used to Hack your Organization
We tried calling some of the numbers provided in the email and during the phone conversation, we could hear background noises of other people talking and realized that the attackers built an entire call center.
At the beginning of the call, the “call center agent” asked how they may help.
We mentioned that we have just received a strange subscription renewal and we would like to cancel it. The person on the line asked us to provide the “Renewal ID” and we did. Then, after being placed on hold for 30 seconds, we were instructed on go on this website:
Listen to the full phone call recording:
The Website
Although the website is extremely well crafted and looks like the actual Geek Squad Website, there are ways to identify that this is an illegitimate site.
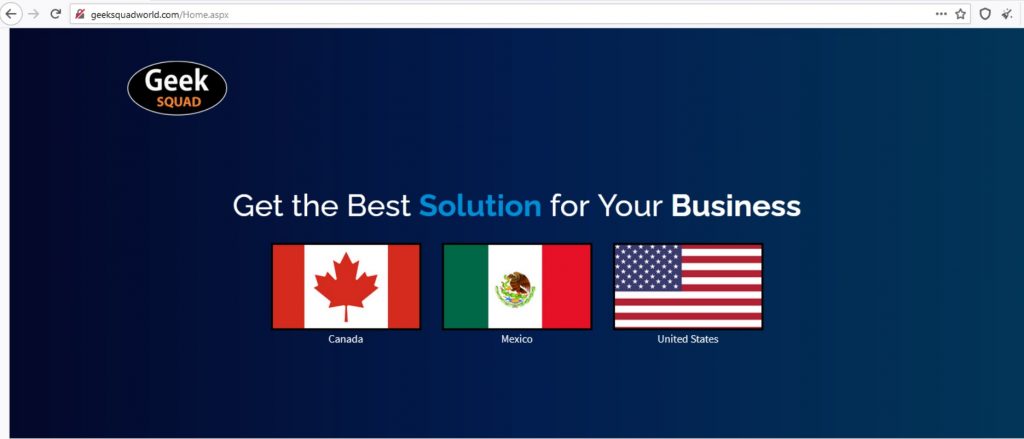
The first thing we noticed is that the website has no digital certificate and that the connection is not secured.
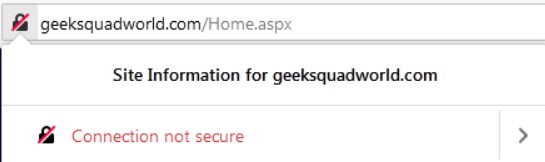
The “agent” guided us to click on the United States logo in order to proceed to the English website. But we noted that every button actually leads to the same page:
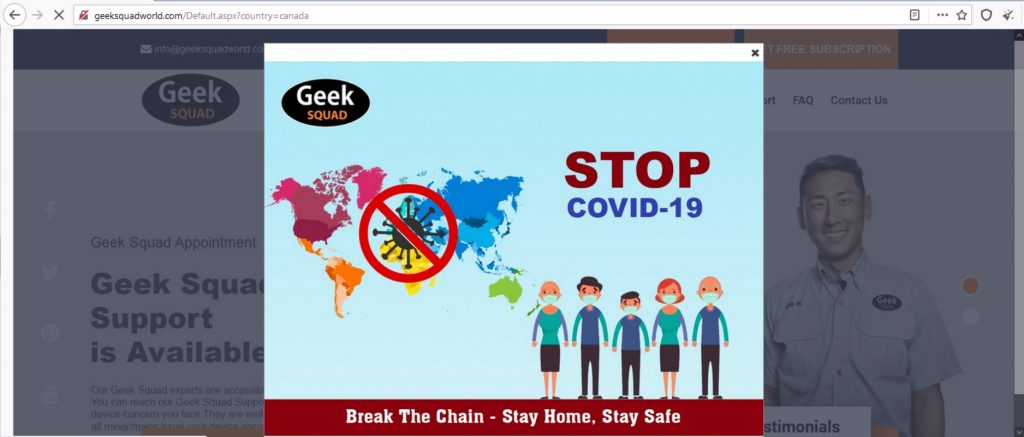
The attackers did an incredible job with the UI and UX of the website which is very uncommon to standard phishing websites.
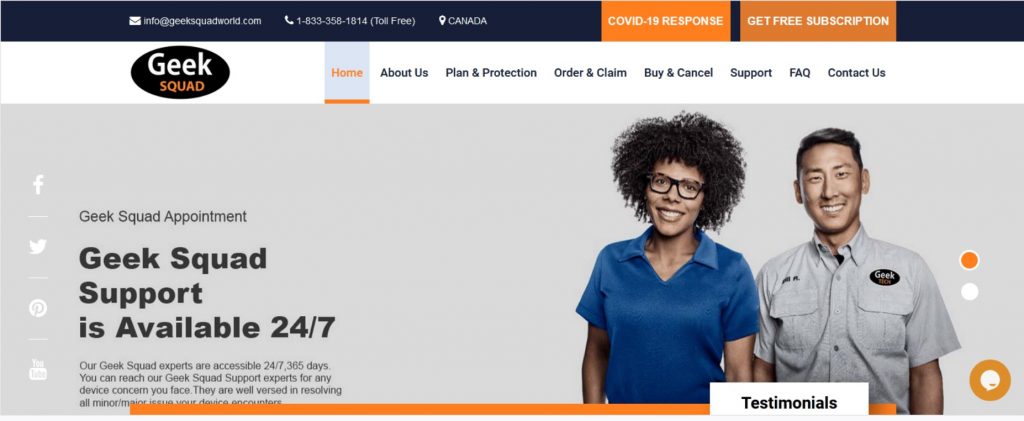
Request to Download Software
Next, in order to help us cancel our subscription, we were asked to go to the “Support” tab and download team viewer.
TeamViewer is remote access and remote-control computer software, allowing IT technicians to remotely log into computers and other devices in order to fix technical issues.
We checked the hash of the installer and compared it with the hash of the software available through the team viewer’s website and it was indeed the same.

We ended the call when we were instructed to give the team viewer’s password to the attacker in order to control our computer.
Points to Notice to Avoid Malicious Campaigns
Site Registration Date
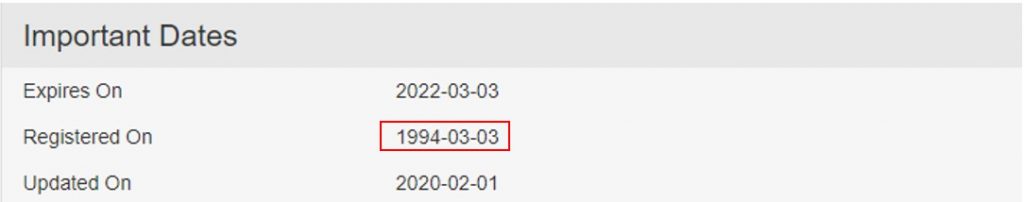
We checked the “geeksquadworld.com” domain on Who. Is and discovered it was recently created.
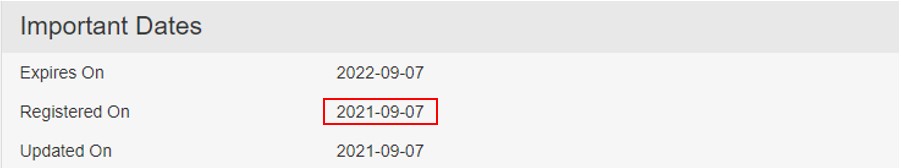
Geek Squad’s actual website, is under Best Buy’s domain which was registered in 1994.
www.bestbuy.com/site/services/geek-squad
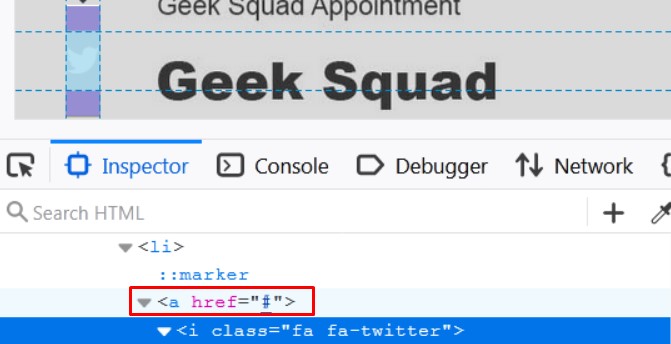
Social Links do Not Work
The buttons in the social media section do not lead anywhere, and we can see that the attacker created them with empty “href” tags. The entire section was created in order to increase the reliability of the website.

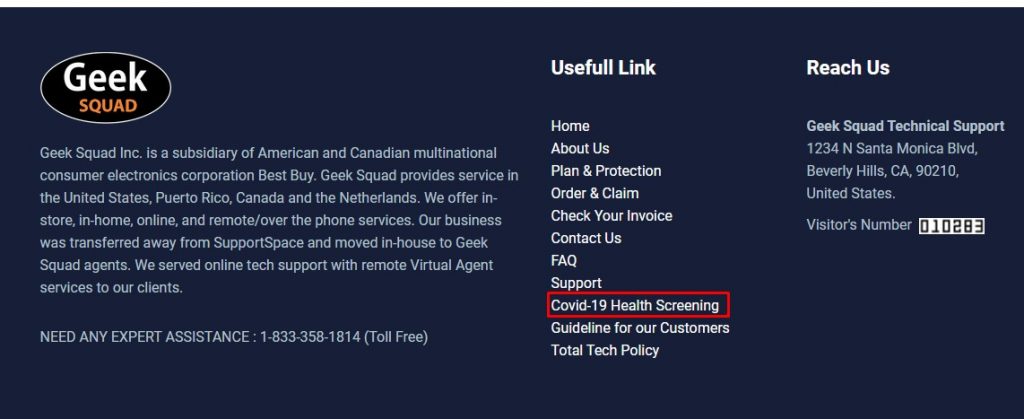
Many Links Return 404
Some parts of the website do not exist and return a 404 error.
Some Unclickable Icons

Design Errors
IOCs
List of email addresses:
- Service Updates [email protected]
- lameha lame [email protected]
- Service Update [email protected]
- Invoice [email protected]
- Billing_Team__v203 [email protected]
- Gavinna_Billing_Team_0325 [email protected]
- Geek_Squad [email protected]
- Coreen Losm [email protected]
List of phone numbers:
- +1-(866)-414-2293)
- +1-803-232-9655
- +1877 253 0093
- +1 (833) 610 – 1374
- +1(800) 494-1681
- +1 (844) 355-0639
- 833 955-0011
- 800 890-9249
- +1 918 467-5100
Recommendations to Protect Yourself from Scams Used to Hack Your Organization
- Beware of generic greetings and unfamiliar email addresses or phone numbers.
- Don’t be afraid – hang up the phone or delete the email. Use block for the email address the scam was sent through.
- Always check the display name and sender’s email address. Changing the display name is very common so validate the email address as well, to decrease the chance of a successful spoofing attempt.
- Contact the company yourself before taking any action. You can always verify whether a communication is legitimate by reaching out to the company directly using an official phone number or email address.
- Never give access to your computer to a third-party service you do not trust.
- When in doubt, ask for a second opinion from your company’s security expert or IT team.
- For organizations, use an advanced email security solution with dynamic analysis of files and URLs and advanced anti-phishing engines, so that these types of email attacks won’t ever land in your user’s inbox. By intercepting these emails, you don’t need to rely on your employees’ ability to catch these sophisticated phishing attacks.
Read more about Perception Point’s advanced Email security detection technology to help secure your business
























