The Rise of Social Media as a Browser Security Challenge
In the modern workspace the lines between professional and personal digital spaces are becoming increasingly blurred. Popular social media platforms like Facebook, LinkedIn and WhatsApp, once relegated to the realm of personal interaction, have long been integrated into the fabric of daily corporate communication and networking.
This integration, however, brings with it some major cybersecurity challenges. Employees engaging with their personal accounts on company devices become inadvertent targets for threat actors who leverage social media platforms as attack vectors and access points to organizations.
From Infostealers to Account Takeover: The Dark Side of Social Networks
Social media has revolutionized the way we connect, share, and engage with our professional communities. Yet, this digital convenience also opened Pandora’s box of vulnerabilities. Recent incidents have underscored the sophisticated ways in which threat actors exploit the wide presence of employees’ social media accounts in enterprise browsers as a vector for hijacking personal and corporate data. For instance, the emergence of a new Python-based Snake infostealer recently made headlines for leveraging Facebook messages to trick users into downloading malware, aiming to hijack accounts by stealing sensitive browsing data.
LinkedIn Catch-22: Networking Meets Net-wrecking
Microsoft’s LinkedIn is another popular social media target, renowned for its emphasis on professional connections. The platform is densely populated with publicly available data on its user base, individuals linked by their professional relationships and organizational ties. For threat actors aiming to compromise a business, LinkedIn serves as an ideal platform for both harvesting business-related email addresses for reconnaissance purposes and a vector for delivering the attacks. LinkedIn users get targeted with HR scams and malicious job offers loaded with malware, those attacks are usually delivered via avatars, fake digital personas or identities, created and nurtured by attackers to appear like real users. The recent discovery by Perception Point highlights a new LinkedIn threat, one that combines breached users’ accounts and an evasive 2-step phishing attack.
Linked In, Phished Out: Unpacking the 2-Step Attack on LinkedIn
Account Takeover
The initial phase of the attack leverages compromised LinkedIn profiles, which at first glance, appear as benign contacts within the victims’ professional network. These profiles, however, are under the control of threat actors who have tailored their attack to exploit the trust inherent in existing professional relationships. The attacker sends a direct message, from a known “1st connection” contact, which contains a malicious link. The legitimacy of the sender’s profile serves as the perfect disguise, significantly lowering the victim’s guard against potential threats.
Social Engineering
The attackers employ social engineering to lure their victims into clicking a “secure” OneDrive link – “a confidential project still in the early phases” and “your skills could be useful in it”
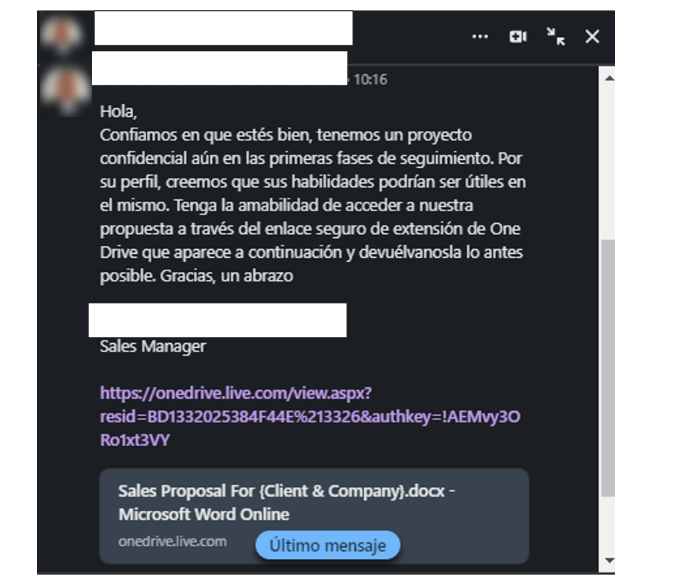
Figure 1: An example of the deceptive message from a compromised account.
Step 1: OneDrive Doc File
Upon clicking the URL in the initial message, victims get to a 100% legitimate Microsoft OneDrive page, where they can access a “Sales Proposal” Word document prepared by the threat actors. This technique is what we refer to as the first step in a two-step phishing attack. Leveraging legitimate hosting websites is crucial as it serves to further build the victim’s trust through the use of familiar interfaces.
Figure 2: “Sales Proposal” Office Word document hosted on onedrive.live.com
Step 2: Evasion & Malicious Payload
On the OneDrive hosted document there is an embedded URL (“OPEN FILE HERE”), in order to access the proposal file the victims are prompted to click it. Once clicked, victims are redirected through a bogus Cloudflare verification prompt before accessing the website managarups[.]com. The introduction of this type of “human verification” is done to further evade detection tools.
Figure 3: Attackers use a hidden JavaScript payload that shows a fake protection DDoS display screen
Following a quick loading animation the victims get redirected to the actual phishing page that mimics OneDrive and aims to steal their Microsoft 365 credentials.
Figure 4: Final destination of the two-step phishing attack – spoofed Microsoft 365 login page
Analyzing the HTML code of the Microsoft phishing page reveals it belongs to an organized group of threat actors by the name of “3rr0r Hun73r” that generate and sell phishing websites on demand.
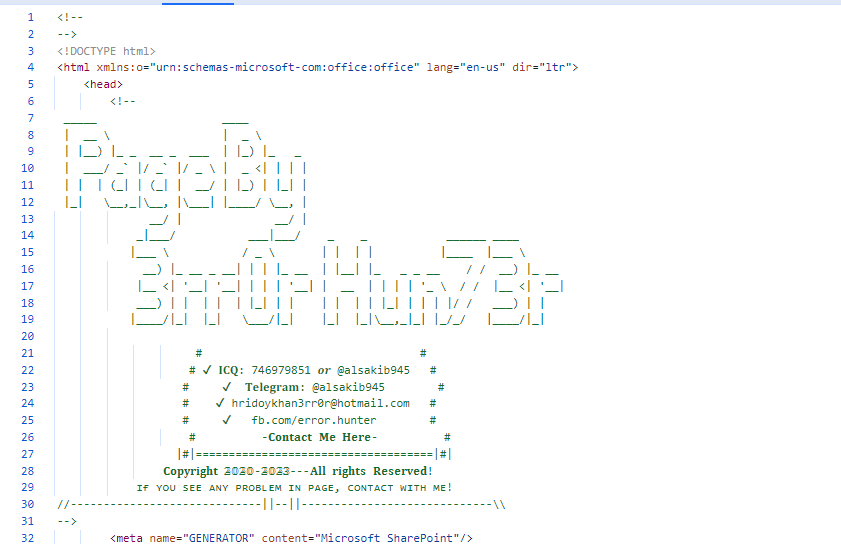
Figure 5: 3rr0r Hun73r – the threat actor behind the phishing website
Prevention at the Point-of-Click: Enterprise Browser Security
Perception Point Enterprise Browser Security extension detected and prevented this Microsoft impersonating attack in real-time using advanced textual and image recognition AI models.
Some of the evidence gathered:
- An image with 0.9662 similarity score to the Microsoft logo
- Microsoft Outlook favicon impersonation – the small, iconic image that represents a website in a browser, displayed in the address bar, browser tabs, and bookmarks.
- A login form written in PHP, containing “Microsoft” and asking for email address and password.
- URL reputation and deep analysis (creation date, HTML content discrepancy, etc.).
Figure 7: the malicious scan as shown on Perception Point’s platform
The Critical Need for Advanced Browser Security
The lines between professional and personal workspaces are getting thinner, making social media platforms a new preferred target for advanced threat actors. With recent incidents showcasing the innovative use of platforms like LinkedIn to launch two-step phishing campaigns, the urgency for robust security measures around the organizations’ browser has never been clearer. These attacks not only threaten individual privacy but also take over enterprise accounts and jeopardize the integrity of corporate data.
To safeguard against these insidious threats, it is crucial for security and risk decision makers to assess and adopt comprehensive browser security solutions. By prioritizing advanced detection technologies and promoting security awareness, organizations can significantly mitigate the risk of social media-based attacks on enterprise devices.
























