In the latest Gartner Market Guide for Email Security, Gartner focuses on two categories of email security solutions: the veteran SEGs (Secured Email Gateways), and a newly introduced category ICES (Integrated Cloud Email Security). The former has been around for over 20 years, and the ladder is a relatively new category which has also been renamed this year.

This blog will provide an overview of the two categories of solutions, how each is deployed in the field, the differences between them, and what’s important to keep in mind when performing an evaluation of a new email security solution from any category.
Secured Email Gateways – The Firewall of Email
Email security for both inbound and outbound email has traditionally been provided by SEG solutions. SEGs process and filter SMTP traffic, and require organizations to change their MX record to point to them. They originated in the era of on-premise email and were built as on-premise solutions. In recent years, as the shift to cloud email began to dominate the market, SEGs moved their solutions to the cloud. It is important to note that although running on the cloud, SEGs are not cloud-native, were not originally designed for the cloud, affecting their ability to support speed and scale, and as a result, may affect their ability to scan 100% of the content coming into the organization. They also lack the agility of cloud-native SaaS applications, in deploying updates and supporting new features.
How are SEGs deployed?
SEGs direct all email traffic coming into the organization to them, serving as the front line of defense. All emails are scanned by the SEG, it quarantines emails it detects as malicious, and only lets clean emails through to the email service provider and to the end user.
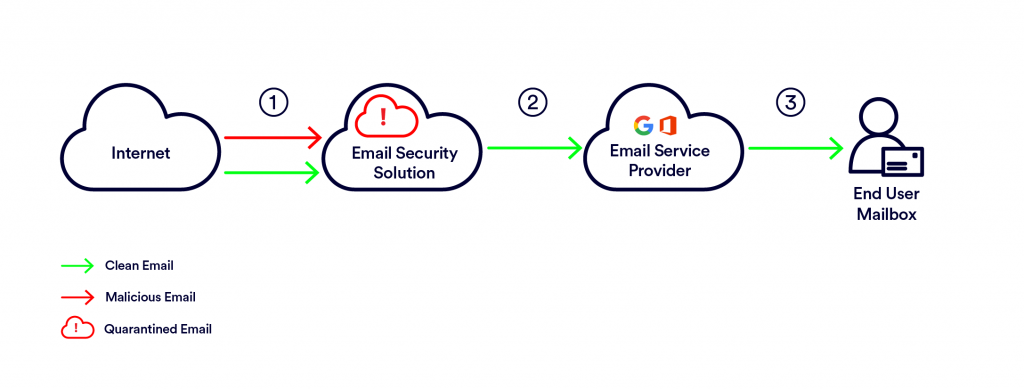
One important benefit of SEG deployment is the fact that all emails are scanned pre-delivery, before reaching the end user mailbox (rather than post-delivery scanning, which scans emails after they are in the inbox, and pulls them out in case they are malicious).
There are some inherent limitations, resulting from the way SEGs are deployed:
- Not utilizing built-in protections from the email service provider – SEGs commonly require disabling of the default email security of the email service provider, so the built-in protections of the email service provider, e.g. Microsoft Office 365 or Google’s Gmail, are not utilized.
- SEG performance is hard to evaluate – because SEGs are located on the MX-record, they always receive the email traffic first. Placing another solution after an existing SEG, usually results in catching additional attacks that the SEG missed. However, that is only half of the evaluation, because you cannot evaluate what the SEG detected as opposed to the second solution.
- SEGs are not seeing internal traffic – being located on the MX-record, SEGs receive all of the company’s inbound and outbound traffic. However, they are not exposed to internal emails, so they have limited ability to monitor for compromised internal accounts, lateral phishing and account takeover attempts.
Along Came ICES
Integrated Cloud Email Security (ICES) solutions, sometimes referred to as “Light SEGs,” provide all detection features, leveraging advanced technologies for email protection. They are SaaS solutions, born in the cloud and provide the benefits of cloud-native applications, which include scale, agile updates and reduced management overhead. Additionally, when using ICES solutions, there is no need to change the MX-record, which results in simplified deployments.
Realizing that organizations are essentially exposed to similar attacks coming in from email through other cloud collaboration channels, some ICES solutions also extend their advanced threat protection to cover these channels.
Gartner puts a special emphasis on this relatively new category, and recommends that organizations address their existing SEG advanced threat defense capability gaps by either replacing the legacy solution or supplementing it with an ICES solution.
According to Gartner, ICES solutions deliver the following benefits to organizations:
- Advanced technologies for email protection, that provide significantly better detection than SEGs for sophisticated attacks
- Ease of evaluation, resulting from the fact they are second in line after the email service provider
- Detection of compromised internal accounts
- Post-delivery capabilities, such as claw-back functionality
- Conditional banners that inform users to help them make decisions
- Ability to move messages into built-in classification mailboxes, e.g. “Promotions”
- Ability to augment the ICES solution on top of existing built-in protections
- Ability to protect additional collaboration tools using the same system used for email protection, e.g. protection of cloud storage and other cloud apps

How are ICES solutions deployed?
ICES solutions integrate directly into the cloud email provider via an API or a Routing Rule/Connector. Most solutions only support the API integration option, while a small number also support a Routing Rule/Connector Integration.
API-based ICES Solution Deployment
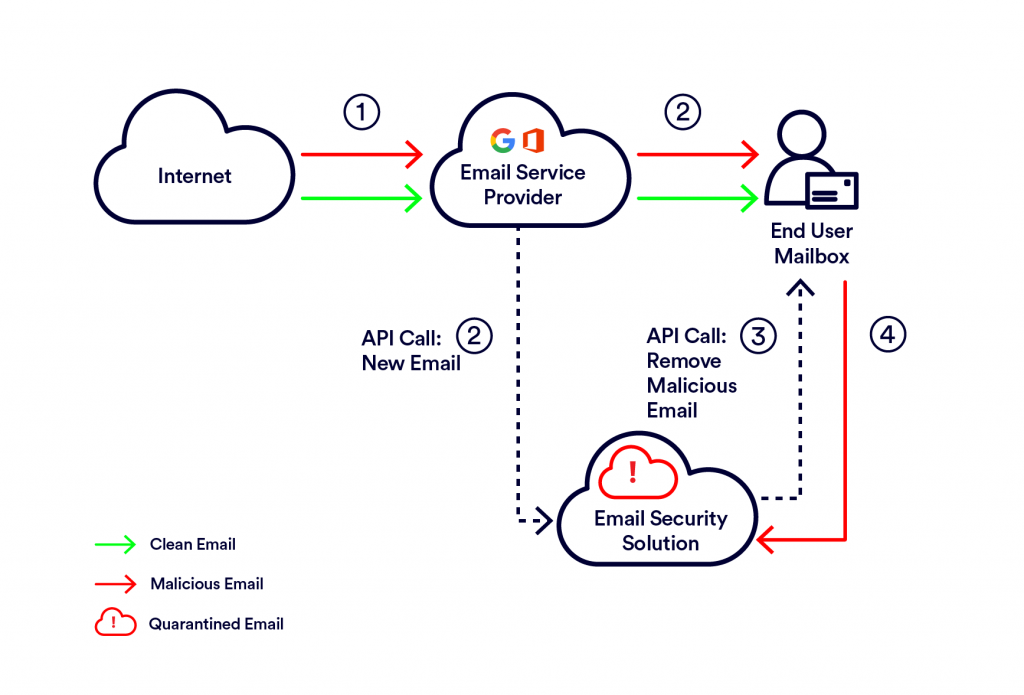
With an API integration the email initially gets to the email service provider; Then, it is sent to the end user and in parallel it is sent to the email security solution using an API call. The email security solution then scans the email, and removes/quarantines it if found malicious.
API based solutions provide many benefits – They’re much simpler to deploy than the typical SEG which requires a change to the MX record. ICES API integrations don’t require network changes. However, one downside is that emails are scanned in parallel to the delivery, so there is a period of time in which a malicious email resides in the user’s inbox, until it is scanned and if malicious, pulled out, leaving the organization exposed to risk.
Another possible issue to note with API-based ICES solutions is related to API throttling. There is a certain cap of API calls permitted by the email provider, and if exceeded, it may stop alerting the email security solution on new emails, sometimes even for hours.
Routing Rule/Connector ICES Solution Deployment
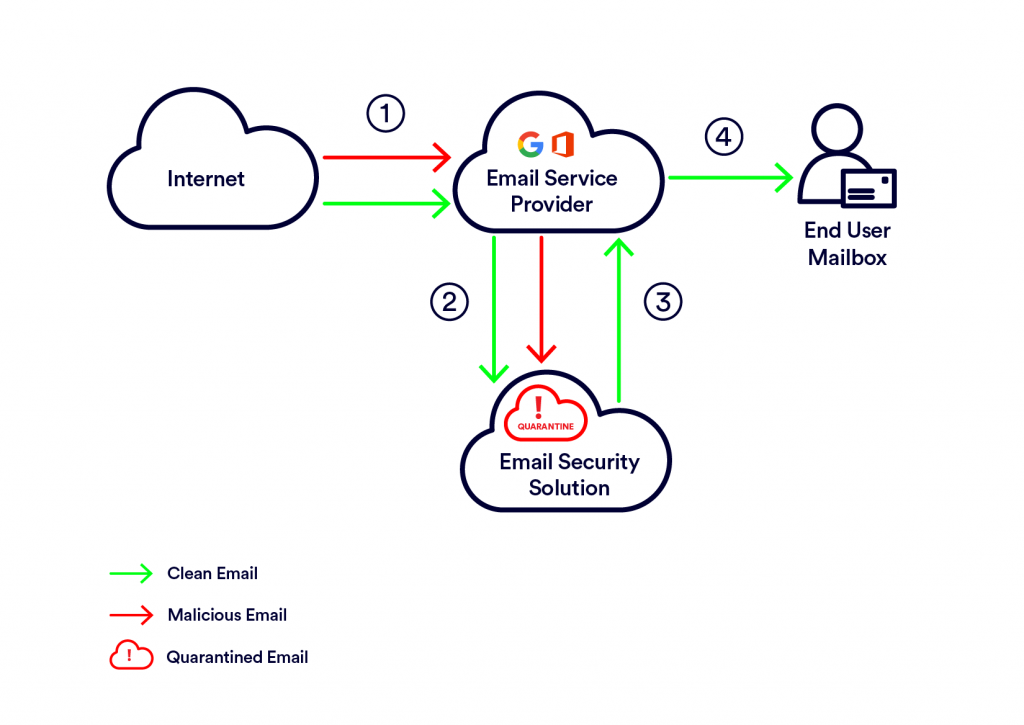
In this option, pre-delivery scanning is performed, so malicious emails are stopped before reaching the end-user’s inbox. An email arrives to the email service provider, but then immediately gets routed to the email security solution and not sent to the end user. Only after it is scanned and found clean, it is returned to the email service provider to be delivered to the end user mailbox.
Routing Rule /Connector deployment, like API integrations are quite simple. They do not require changes to the MX record or any existing infrastructure change.
Bottom Line – SEG or ICES?
Due to the inherent benefits ICES solutions provide, it is not surprising that Gartner estimates the ICES category will significantly grow over the next few years, as the market continues to adopt these next-gen solutions.
Organizations should carefully assess the different ICES solutions available today, to make sure they receive the best protection and select the best fit solution for their organizations.
Here are some important questions security professionals should ask during the evaluation:
- Will the solution improve the organization’s ability to protect against advanced threats?
- Does the solution allow for an easy evaluation of the improvement in detection it is claiming to provide?
- Does the solution support pre-delivery or post-delivery scanning?
- Does the solution provide advanced functionality commonly used today to enhance protection, e.g. context-aware banners, internal email protection?
- Does the solution allow for holistic protection of additional channels in the organization, on top of email?
About Perception Point
Perception Point is a Prevention-as-a-Service company for the fastest and most accurate next-generation detection and response to any content-borne attack across email and all cloud collaboration channels, including cloud storage, cloud apps, and APIs for proprietary applications. The solution’s natively integrated incident response service acts as a force multiplier to the SOC team, reducing management overhead, improving user experience and delivering continuous insights; providing proven best protection for all organizations.
Deployed in minutes, with no change to the enterprise’s infrastructure, the patented, cloud-native and easy-to-use service replaces cumbersome legacy systems to prevent phishing, BEC, spam, malware, Zero-days, ATO, and other advanced attacks well before they reach end-users. Fortune 500 enterprises and organizations across the globe are preventing content-borne attacks across their email and cloud collaboration channels with Perception Point.
To learn more about Perception Point, visit our website, or follow us on LinkedIn, Facebook, and Twitter.
Here’s related content you may enjoy: Default Email Security Not Secure Enough
























