Perception Point researchers have discovered a vulnerability in macOS which allows an attacker to bypass App Sandbox restrictions. The vulnerability was disclosed to Apple, and the fix was announced on the latest macOS Monterey 12.0.1 security update on October 25th, identified as CVE-2021-30864. This vulnerability is closely related to CVE-2021-30783 which was fixed in earlier macOS versions ([1], [2]).
This article provides an overview of what the App Sandbox is and the vulnerability details as disclosed to Apple.

What is App Sandbox?
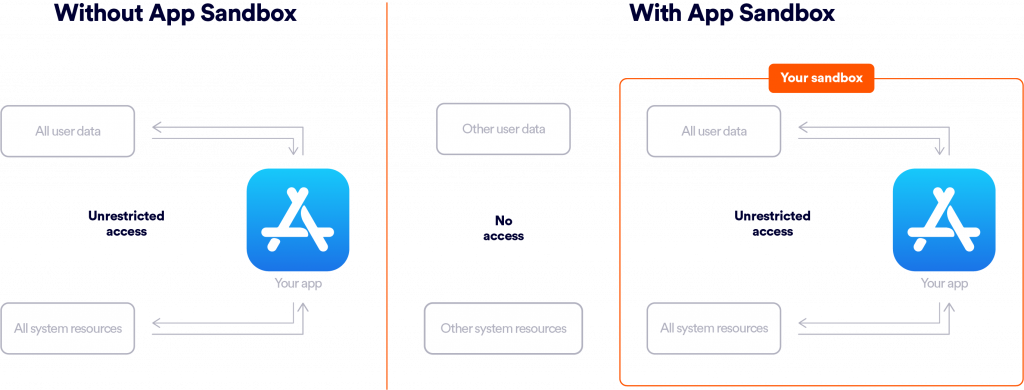
macOS App Sandbox is a mechanism to restrict applications’ access to system resources and user data ([3]). Applications voluntarily put themselves inside the sandbox, configuring through entitlements the necessary resources they are allowed to access, in order to contain damage if the app becomes compromised by an attacker. A user may also use an application’s entitlements to assess its behavior and security risk. Despite the voluntary approach, Apple allows only sandboxed applications into the Mac App Store.

Every sandboxed application gets its “container” – a directory serving as the application’s home directory – and even the most restricted applications have access to their container directory. This detail will become important when we overview the vulnerability.
The Vulnerability
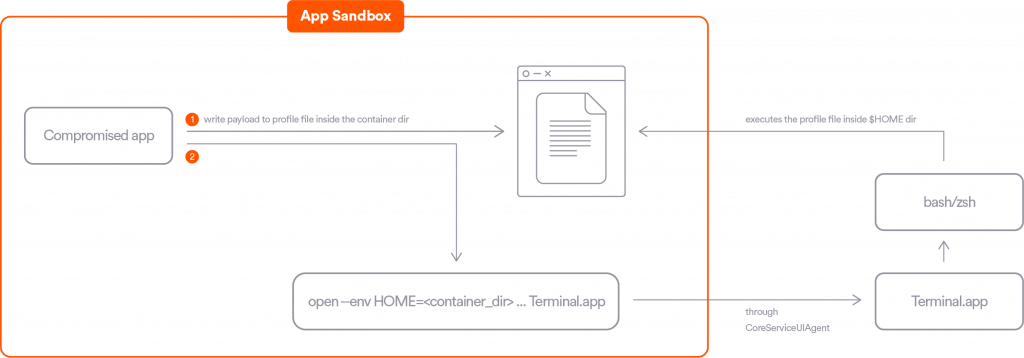
macOS users may be familiar with the open utility which opens files, directories and applications just as if you had double-clicked them. A sandboxed application can use this utility, or its underlying API calls, to execute another application. Independently of the calling application sandbox configuration, the newly opened application would run in its own sandbox configuration, or even outside of a sandbox (if it’s not a sandboxed application).
Our researchers found a way to exploit this behavior by opening the built-in Terminal application, which is not sandboxed. In order to execute an arbitrary command in the context of Terminal, we leverage another feature of the open utility – controlling the environment variables of the target application. Hence it is possible to control the “HOME” environment variable of Terminal and make it point to the container of the sandboxed application. After some research we also discovered that an additional variable, “__OSINSTALL_ENVIROMENT”, is needed in order for the “HOME” variable to take effect inside the Terminal app.
To conclude, these are the steps a sandboxed application could take to bypass its App Sandbox restrictions:
- Write a desired payload to a profile file (e.g. “.zshenv” or “.bash_profile”, depending on the default shell) in their container directory.
- Open the Terminal application with those environment variables:
- __OSINSTALL_ENVIROMENT
- HOME = <path_to_container_dir>
The newly opened Terminal would run bash or zsh, which in turn would look for their profile files in their inherited HOME directory, hence executing the payload written in the container directory.
An extraordinary “bonus” to the fact that the Terminal application is not sandboxed, is that it is often granted Full Disk Access by the user. In these cases, the vulnerability has the advantage of also bypassing any TCC restrictions, allowing access to user’s sensitive data such as contacts, mails, messages etc.
Vendor Communication
- 2021-06-20 – First report to Apple Product Security.
- 2021-06-21 – Apple advises they are investigating.
- 2021-07-21 – Apple releases macOS 11.5, which addresses the reported vulnerability.
- 2021-07-22 – Second report to Apple Product Security with a slightly different Proof-Of-Concept.
- 2021-07-22 – Apple advises they are investigating.
- 2021-09-17 – Apple advises they will address the issue in the upcoming release of macOS Monterey.
- 2021-10-25 – macOS 12.0.1 released, which addresses the reported vulnerability.
For more information, read Perception Point Researchers Discover Two MacOS Sandbox Escape Zero-Days.
Here’s some related content you may enjoy:
























