Perception Point security researchers recently discovered a phishing campaign targeting Meta users on Instagram. The attack leverages legitimate two-factor authentication codes to steal user credentials. Read on to learn more about this evolving attack.
Attack Flow
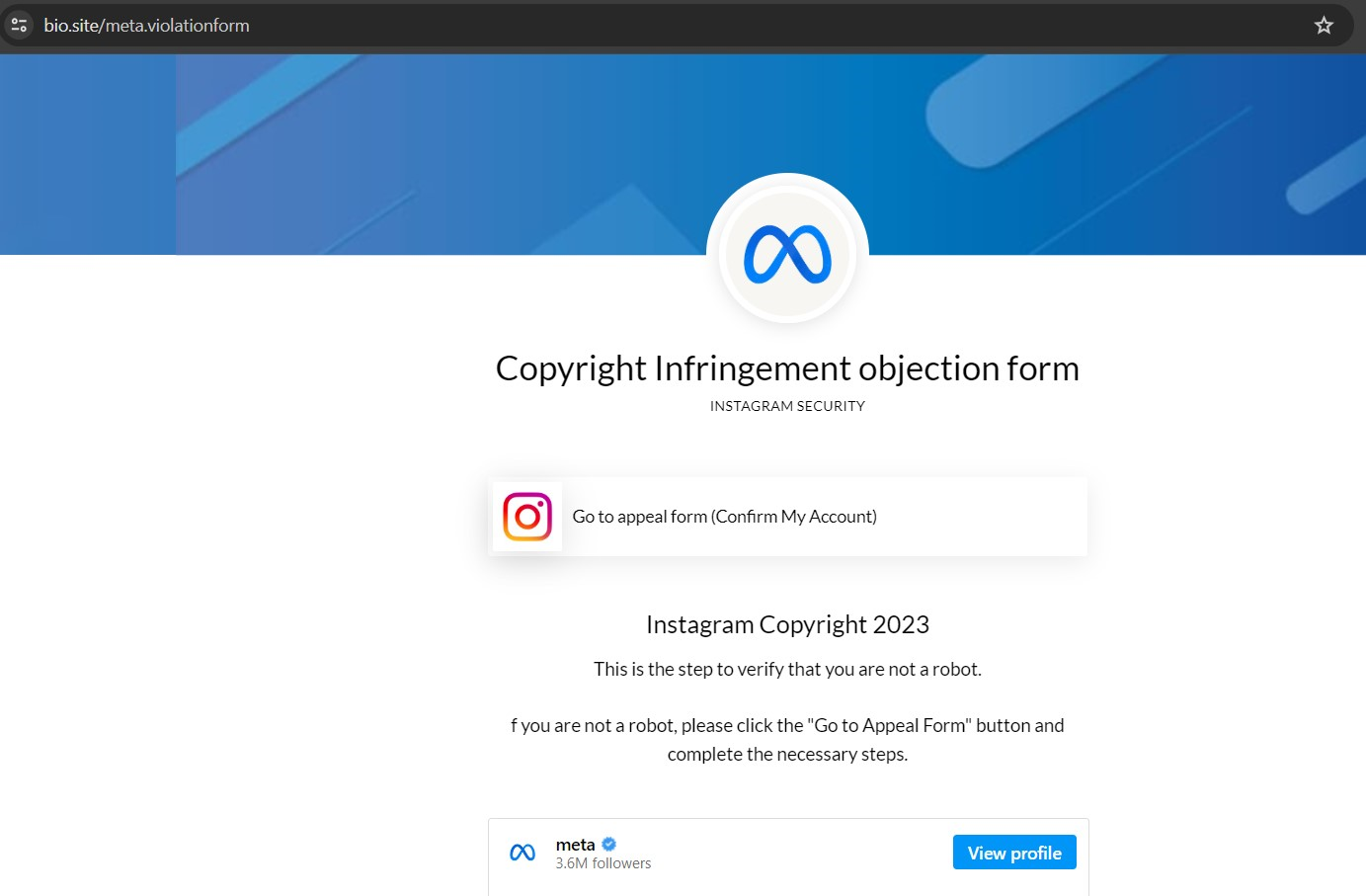
The attacker impersonates Meta and sends the intended target an email, accusing the user of copyright infringement on Instagram. In order to prevent their account from being “permanently deleted from our servers within 48 hours,” the user is pressured to click the link provided and submit an “appeal form.”

Upon clicking on the link, the user is redirected to a webpage which urges them to click on another link that leads to the appeal form.
The second link leads to another webpage reiterating the message that if the target does not complete the appeal form, they risk account deletion.
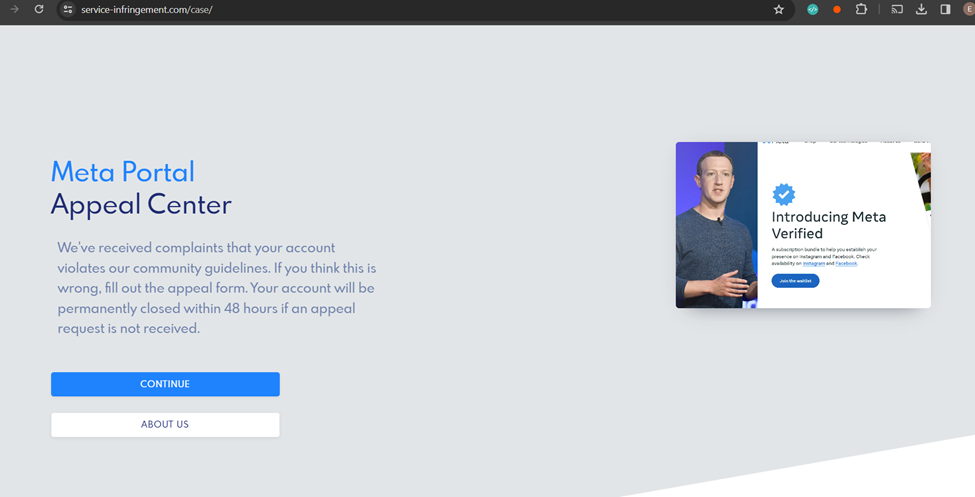
What is unique about this page is that it contains multiple clickable elements and links that lead to Instagram’s actual website, reinforcing the legitimacy of the spoofed page.
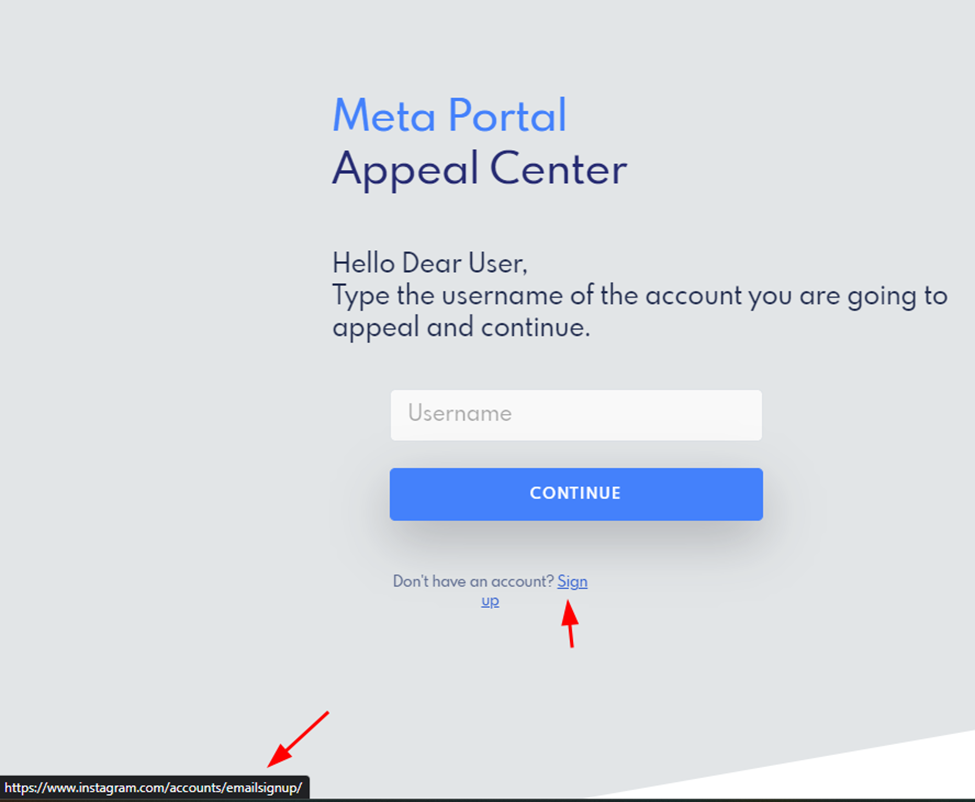
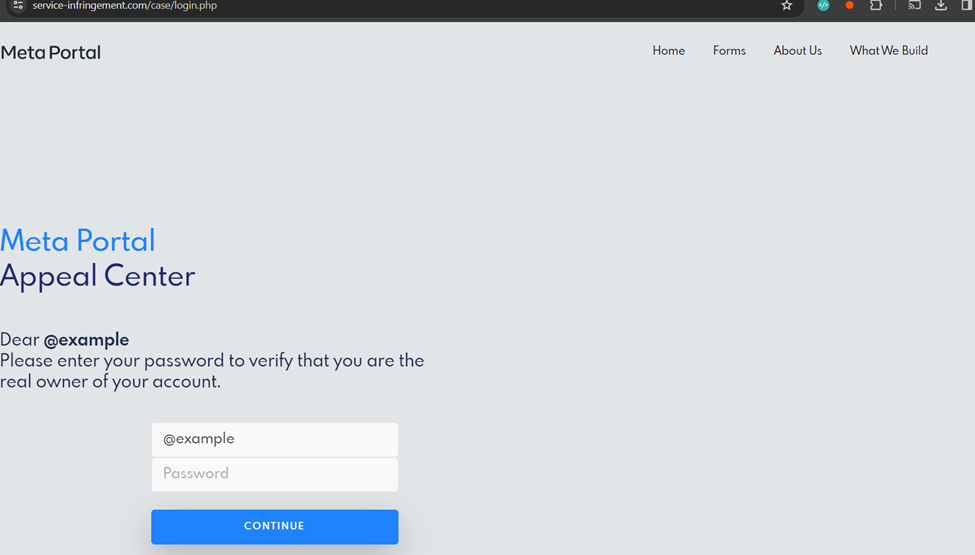
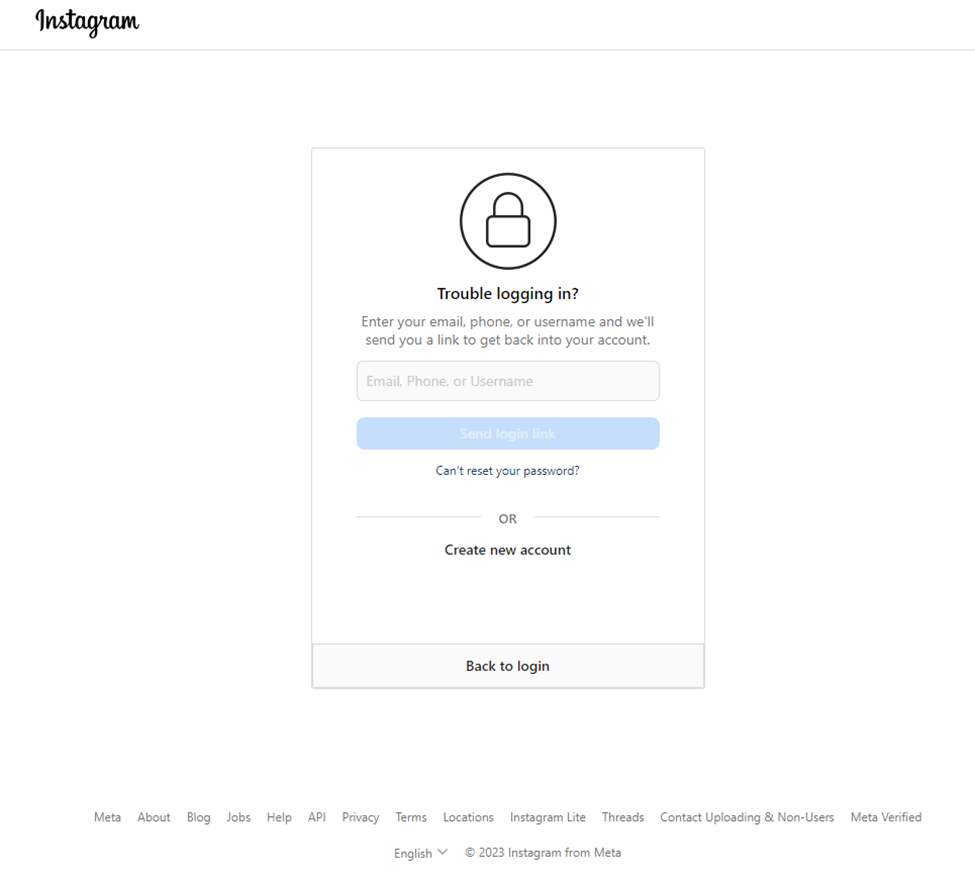
When the user is asked to sign in with their credentials, they are sent to a legitimate Instagram page containing backup codes. This is all in an effort to bypass two-factor authentication (2FA).
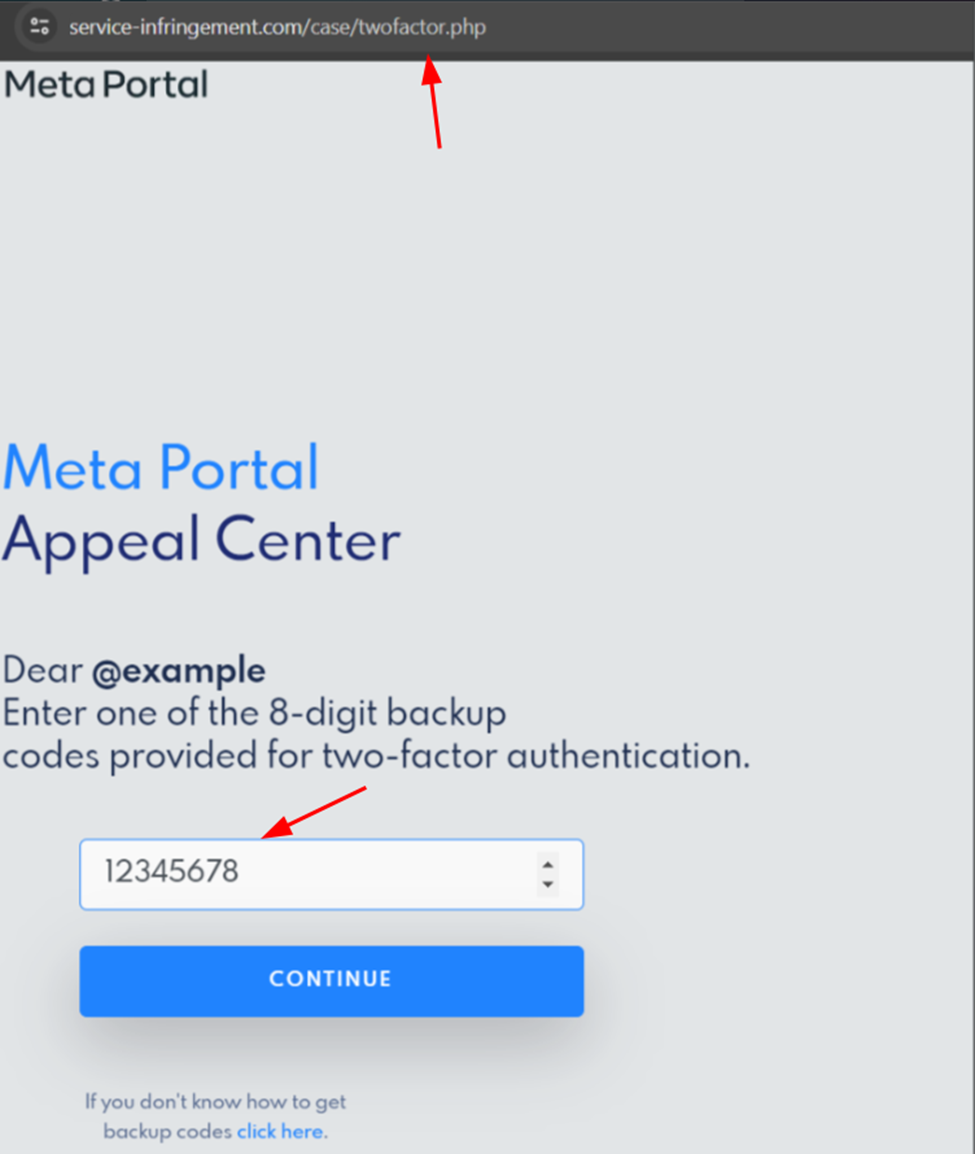
A traditional 2FA involves an authentication code being sent to the user’s email or phone. In this attack, however, the attacker wants the backup code, which would enable them to log into the target’s account independently and without time constraints, thereby bypassing the 2FA process.
After the user enters their backup code, the attacker asks for additional information, including the target’s email and phone number.
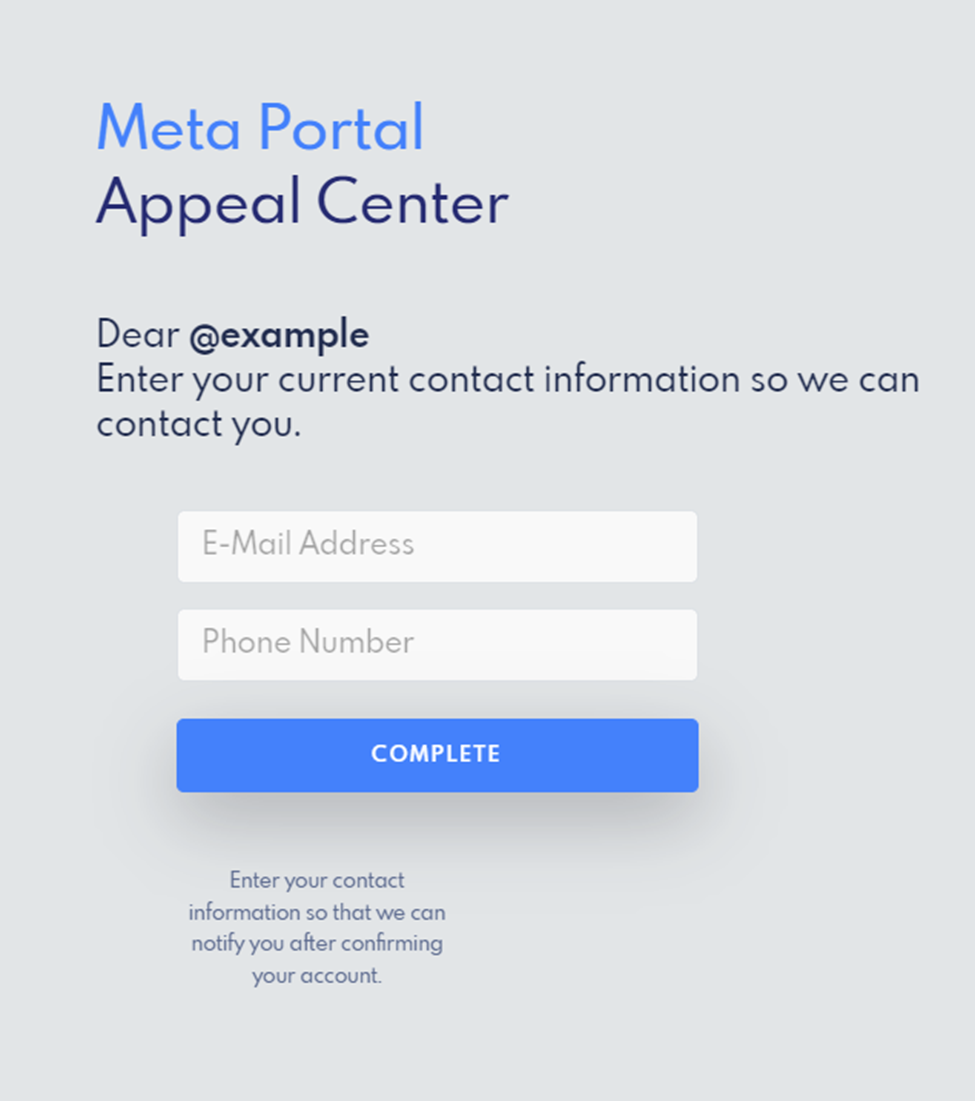
Once the target has submitted their credentials and backup code, they receive a message of completion and are redirected to the Instagram account they registered with. In this case, our security researchers used “@ example” and were sent to that Instagram account.
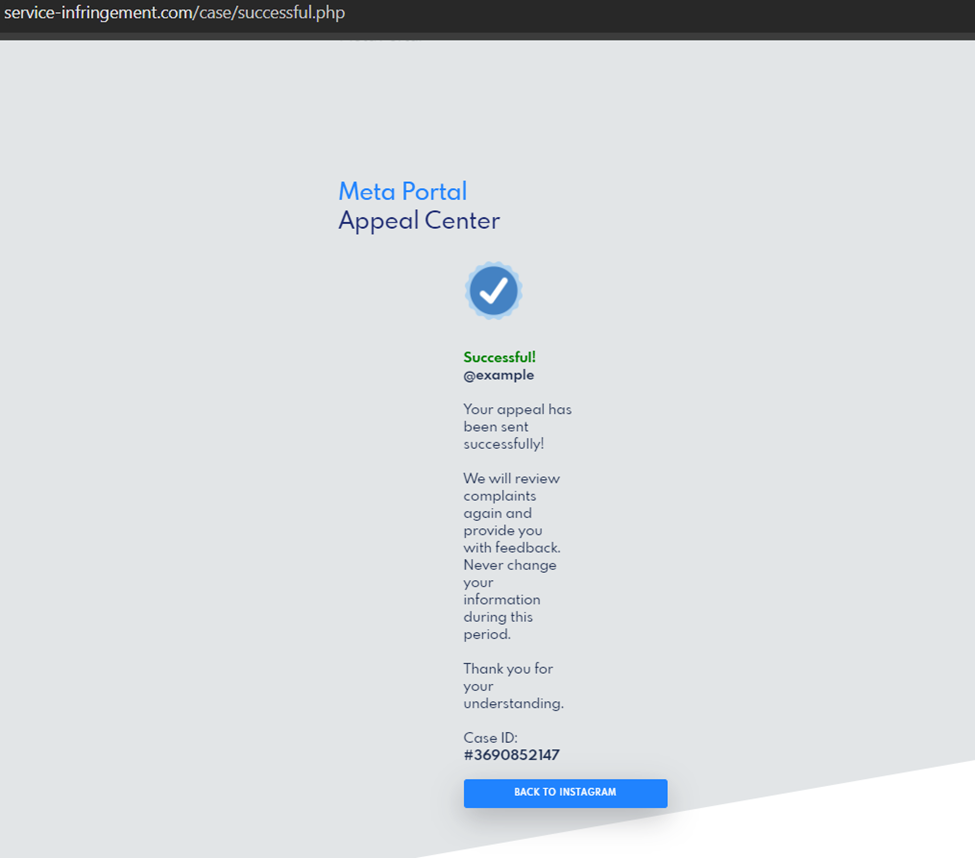
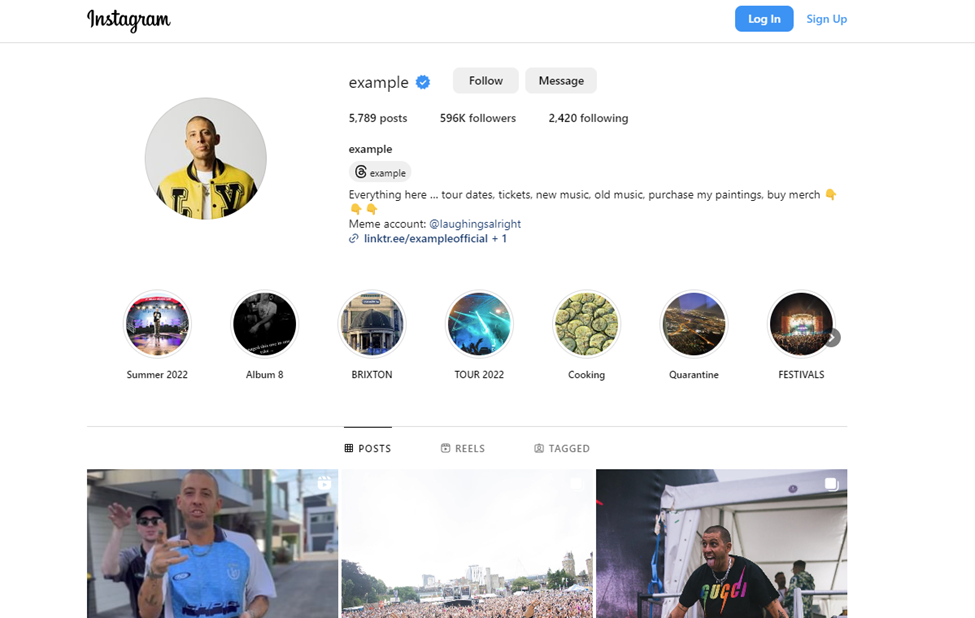
While phishing attacks have used Instagram copyright infringement as a ploy in the past, this campaign is unique in its use of backup codes.
Beyond the Attack
Our researchers noticed that the URLs in the attack changed from page to page. Further investigation revealed a unique index page.
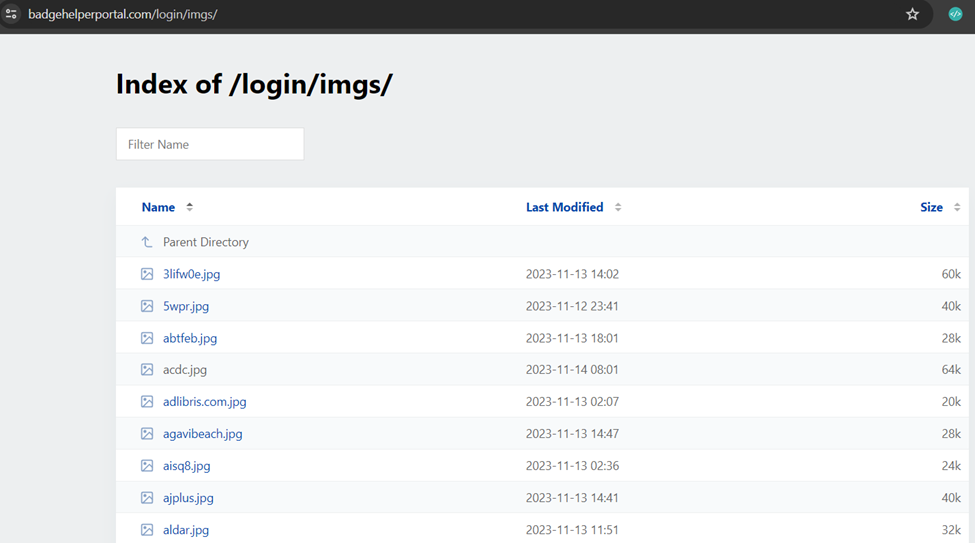
The index hosted a plethora of .jpg files, including logos of organizations and pictures of high profile individuals. Our researchers suspect that the attacker purchased a kit with relevant emails and pictures that corresponded to targets’ Instagram profiles.
Note: As of November 19, 2023 the index is no longer publicly available.
Another interesting aspect of this campaign is that our Advanced Threat Prevention anti-phishing system not only caught the phishing attempt via email, but also through Zendesk. Our phishing prevention platform scanned a seemingly legitimate Google alert, which in turn led to the spoofed Meta pages and the rest of the attack flow.
The Bottom Line
What makes this attack particularly dangerous is its adept use of sophisticated social engineering tactics. The attacker impersonates a well-established entity, Meta, to foster immediate credibility and leverage the instinctive trust often associated with a widely recognized brand. This calculated manipulation is further intensified by the introduction of an urgent scenario, coercing targets into swift action by threatening apparent account deletion.
The combination of brand impersonation and the imposition of a time-sensitive crisis can disarm even the most cautious online users. However, what sets this attack apart is the substitution of authentic backup codes for conventional 2FA. This not only sidesteps users’ reliance on standard security measures but also highlights the sophistication of the attack.
This attack’s multifaceted approach increases the likelihood of successful exploitation and underscores the critical need for heightened awareness and security protocols in the face of evolving social engineering threats like this one.
























