The Verizon Data Breach Investigations Report (DBIR) 2023 has recently been released, providing valuable insights into the current state of cyber threats, incidents and of course, breaches. In this blog post, we explore key takeaways from the report that every cyber defender and security leader should know.
Takeaway #1: The Rising Dominance of BEC (and Social Engineering) Attacks
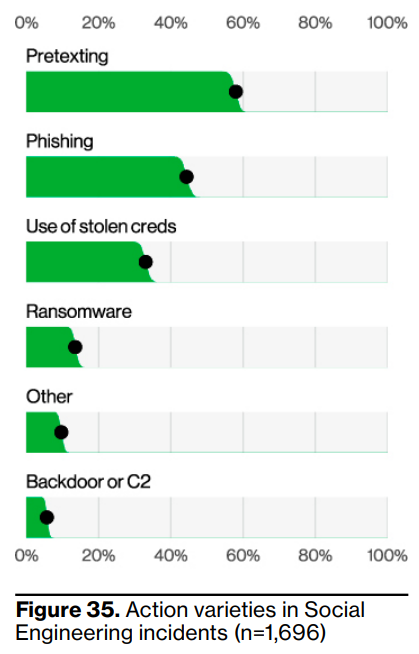
The DBIR report shows that social engineering attacks have become increasingly prevalent in 2023, and quite lucrative for adversaries. Business Email Compromise (BEC) attacks have nearly doubled, accounting for over 50% of incidents involving social engineering techniques, with classic phishing coming in second.
“Business Email Compromise (BEC) attacks (which are in essence pretexting attacks) have almost doubled across our entire incident dataset, as can be seen in Figure 5, and now represent more than 50% of incidents within the Social Engineering pattern.”
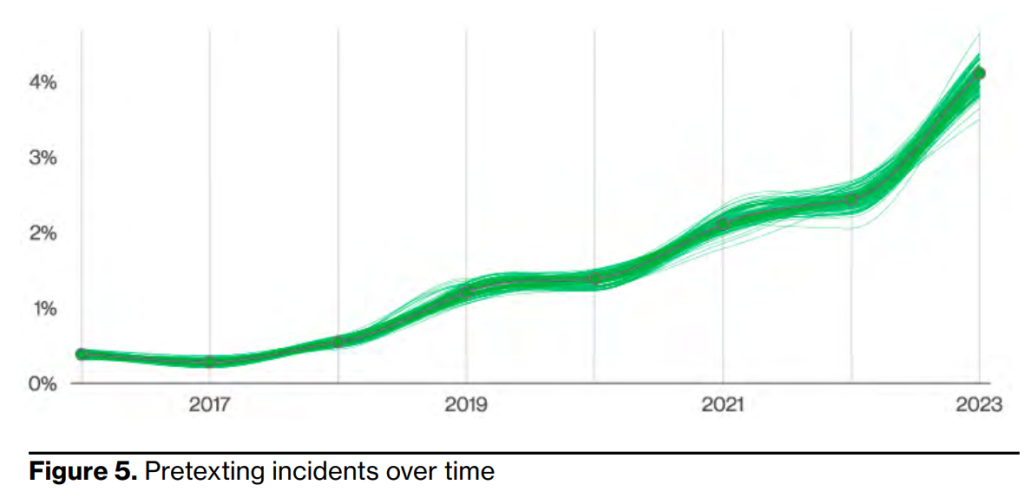
Source: Verizon 2023 Data Breach Investigations Report, “Pretexting” is a deceptive tactic where a false story is used to trick victims into sharing sensitive information, downloading malware, etc.
The report mentions an up and coming sub-type of a BEC, or Pretexting, technique: the notorious thread hijacking.
“In these pretexting attacks, actors leverage existing email threads and context to request that the recipient conduct a relatively routine task, such as updating a vendor’s bank account.”

These attacks are challenging to detect due to the extensive preparation and reconnaissance work done by threat actors. Once attackers gain access to a legitimate email thread, they may purchase and create a similar-looking domain (aka domain spoofing), change contact details on the thread, and make other subtle changes to deceive their targets. The high potential “pay-day” and the complexity of these financial scams could explain why BEC attacks, which now represent over 50% of incidents, have nearly doubled in the last year.
Learn how Perception Point prevents sophisticated BEC and thread hijacking attacks here.
Takeaway #2: The Human Element in Data Breaches
The 2023 DBIR report observed that human involvement is a key factor in 74% of all breaches. This includes errors, privileged access misuse, use of stolen credentials, and, unsurprisingly, social engineering. Regarding the source of a potential data breach, the report says, “External actors were responsible for 83% of breaches, while Internal ones account for 19%.”
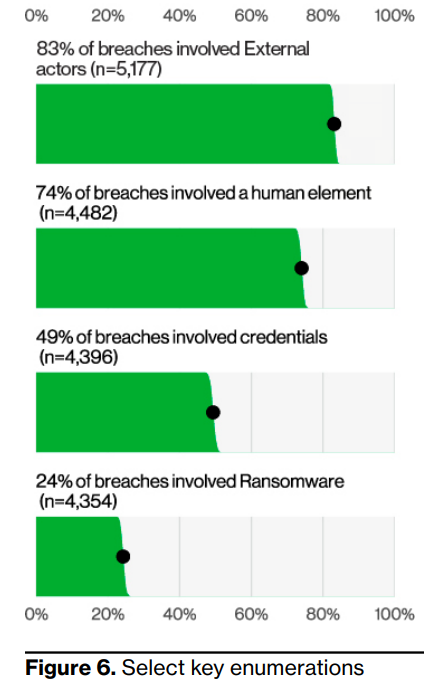
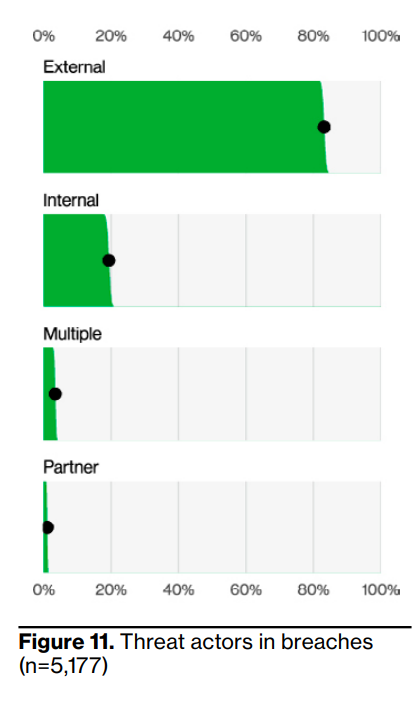
Source: Verizon 2023 Data Breach Investigations Report

This means that one out of every five breaches can be attributed to users within the organization (or partners, vendors, or third parties).
Internal threats can stem from human mistakes, or “error actions”, but they are just as likely come from a “malicious insider”.
These findings highlight the need for a multi-layered approach to cybersecurity. It is not only about securing systems and networks from external attacks, but also about mitigating human behaviors, vulnerabilities, and insider threats at every layer. From enforcing outbound email security to employing endpoint-level DLP controls, securing sensitive data and corporate applications should be highly prioritized by security and risk management leaders in 2023.
Takeaway #3: Zero-Days and Malware Are Still Going Strong

The “Year in Review” section of the DBIR 2023 report provides a detailed month-by-month breakdown of the major cybersecurity events and Zero-Day vulnerabilities. The year kicked off with the tracking of attacks exploiting Log4j, like how the SolarWinds campaigns marked the start of 2021. Log4j, and especially attacks on VMware, remained a persistent risk throughout the year. The report also highlights the resurgence of infamous malware families, Emotet and REvil.
While BEC and social engineering attacks rose to prominence in 2023, complex malware, zero-day exploits, and Advanced Persistent Threats (APTs) also increased in frequency, accounting for many newsworthy breaches. These threats targeting email, web browsers, cloud apps, and other modern workspace attack vectors continue to pose a significant challenge to cybersecurity in 2023.
Perception Point’s innovative HAP (hardware-assisted platform) has transformed the prevention of Zero-Days and APTs. The patented dynamic engine merges CPU-level data with advanced software algorithms to neutralize unknown threats. Instead of detecting malware, the HAP targets attacks at the exploit stage, stopping even unknown vulnerabilities and neutralizing complex attacks in seconds.
Perception Point – Preventing Data Breaches in 2023 (and Beyond)
Perception Point is a Prevention-as-a-Service company, providing the fastest and most accurate next-generation detection, investigation, and remediation of all threats across an organization’s main attack vectors – email, web browsers, and cloud collaboration apps. Perception Point’s solution streamlines the security environment for unmatched protection against spam, phishing, BEC, ATO, ransomware, malware, Zero-days, and N-days well before they reach end-users.
Multiple layers of next-gen static and dynamic engines together with patented anti-evasion technology and image recognition algorithms protect organizations against malicious files, URLs, and sophisticated social engineering techniques. All content is scanned in near real-time, ensuring no delays in receipt, regardless of scale and traffic volume. The solution’s natively integrated, free of charge, and fully managed incident response service which acts as a force multiplier to the SOC team, reducing management overhead, accelerating remediation, improving user experience and delivering continuous insights.
Deployed in minutes, with no change to the enterprise’s infrastructure, the patented, cloud-native and easy-to-use service replaces cumbersome legacy systems.
Fortune 500 enterprises and organizations across the globe are preventing advanced persistent threats and attacks across their email, web browsers and cloud collaboration channels with Perception Point.
To learn more about how to prevent ransomware, phishing, and other cyberattacks with Perception Point. Visit our website, follow us on LinkedIn, Facebook, and Twitter, or contact us today.























