The Incident.
The .msg file is successfully synced/uploaded to the OneDrive. In order to avoid the signature-based security of the OneDrive the attacker has embedded several links and files within this one .msg file. Two of the malicious links lead to a phishing website of a well-known brand. As mentioned, there are over 30,000 employees in this organization, it would have just taken one innocent employee to open this shared file and be exploited by the phishing link.
How Perception Point Prevented the Attack.
Perception Point intercepted this attempt by using two different engines, both of them are part of our Anti-phishing engines stack:
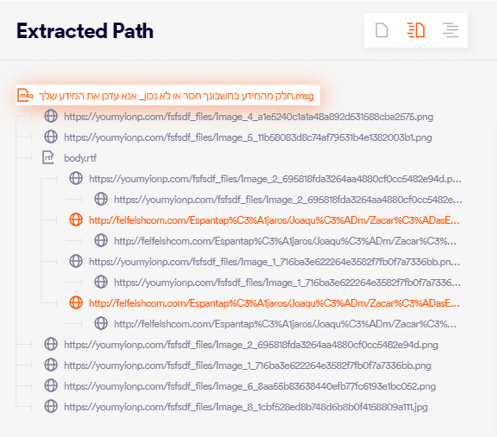
- Recursive Unpacker: If we look at the “Attack Path” below, we can see that Perception Point’s Recursive Unpacker has uncovered several other files/links within the original .msg file. Within this complex web of sub-objects – this engine has detected a malicious link in 2 different locations – showing the robustness of the anti-evasion capabilities.
- Image Recognition: Advanced algorithms scanned each file and link dynamically to detect the use of the known brands assets for malicious purposes.
Interesting Note.
This malicious phishing website in this case was caught on an organizations OneDrive. We have seen the same phishing campaign come through the email channel as well, showing that the attackers are using the same ammunition but getting more creative in their attack vector.
IOCS.
- Channel: OneDrive
- SHA256: e2f435d0070c0172184d40133d9e9f3cf185047cc0e95578bc769b011400a0c0
- Malicious URL: http[:]//felfelshcom[.]com/Espantap%C3%A1jaros/Joaqu%C3%ADm/Zacar%C3%ADasEMiQV5A/C%C3%A1ndidaBqFhMtMipU/Bego%C3%B1ao83Nnuz/Mois%C3%A9sLHnP9pmpwy/Aar%C3%B3nKdMyy7YRvz/DJoaqu%C3%ADnbCHPoCJAX/Abrah%C3%A1n3GsmGDZ3BQ/q0RnfXoL0b/























