Advanced Cloud Storage Security with Perception Point
Perception Point’s Advanced Cloud Storage Security Solution is the ONLY cloud storage security solution that delivers the same robust threat detection typically available only for the email channel.
Advanced Cloud Storage Security prevents malicious files and URLs from being uploaded, downloaded or utilized to infect previously clean files. Deploy in minutes with no impact on user experience.

Cloud Storage:
a Growing Security Blindspot
Cloud storage solutions are amongst the most exposed applications within an organization, and must play a part in any security strategy.
Apps like OneDrive, Dropbox, and Google Drive can be highly effective malware distribution platforms. Once malicious content is on the file sharing service, it can easily travel to any unsuspecting user with access.

Insider Threats
A malicious attack via cloud storage can come from within the organization. For example, an unhappy employee who uploads a malicious file to the company’s shared drive.
Impersonation (Account Takeover)
An attacker may take over a legitimate account or insert himself into a message thread. In this case, the attacker can send an email with a link to a malicious shared file on the drive.
Unmanaged 3rd Parties
A malicious file or URL can come from an external source such as a customer or supplier. For example, a supplier may (unknowingly) sync a malicious file with a shared folder used to transfer files on an ongoing basis.
Fortify a CASB with
Advanced Threat Detection
Fortify a CASB
with Advanced
Threat Detection
CASBs are designed for monitoring access and data leakage, and enforcing policies that will ensure controlled exposure of private and sensitive organizational information.
However, CASBs are not designed for threat detection, including the detection of malicious files, URL or social-engineering attempts, nor are they able to provide forensics on any such attacks. If an organization is only reliant on a CASB for their cloud security, they are likely still very exposed when it comes to cloud collaboration apps.
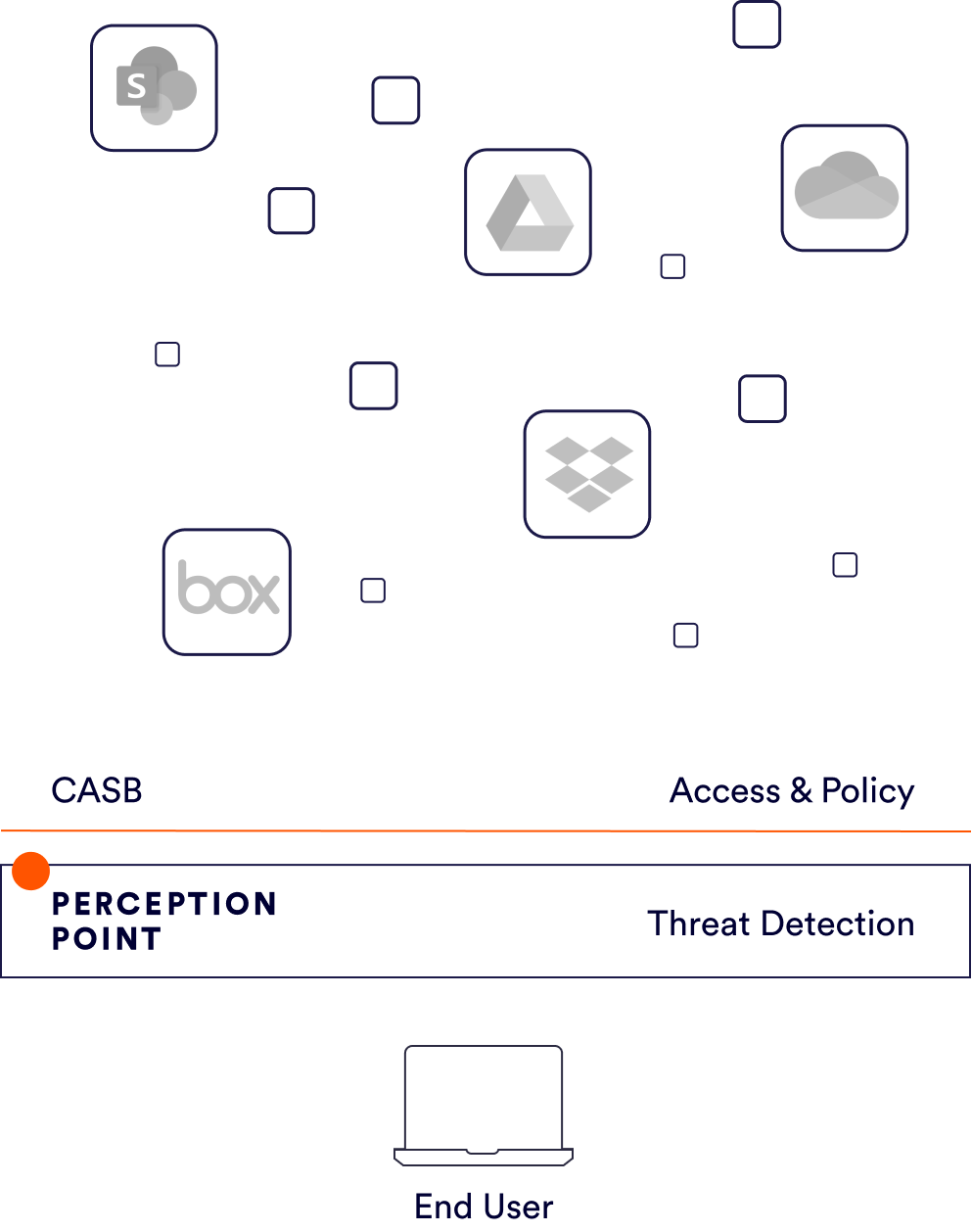
Real-time scanning of all files being uploaded, downloaded or updated. Multi-layered platform detects Zero-days, N-days, phishing, impersonation, and commodity malware.
Upon set up or at regular intervals, scan all historical files to ensure anything malicious is removed from the drive.
Deploy in one-click to any cloud storage app including OneDrive, Sharepoint, Dropbox, Box, and Google Drive. Simply change a setting and you are connected.
Incident Response team, all formerly part of the Israeli Defense Forces, continuously analyzing and delivering insights on malicious content detected.
Proven Results
More and more companies choose Perception Point Advanced Threat Prevention
Case Study
-
Global Financial Services Firm Replaces Proofpoint A global financial firm faced challenges with preventing phishing attacks from reaching their users. Despite investing in security awareness training, the security leadership was concerned about phishing emails that were successfully bypassing their Proofpoint deployment.
-
Enhancing Microsoft Email Security to Prevent Advanced Phishing & BEC Attacks Perception Point’s Advanced Email Security for Microsoft 365 helps a global food distributor achieve seamless and comprehensive protection against advanced email-borne attacks including phishing and BEC.
-
Red Bull Augments Microsoft EOP to Prevent Attacks When given the opportunity to put our solution up to the test, Perception Point’s Advanced Email Security proved to be a cut above the rest.
-
Flow Control: Manufacturing Leader Selects Perception Point to Optimize Their Advanced Threat Protection With Perception Point’s consolidated solution protecting the customer’s email, browser, and Microsoft 365 suite, Flow Control Group benefits from simple deployment and holistic management capabilities.
See Perception Point in action!
Other Related Products
Easily combine our email security platform with these other unique products from Perception Point
Full coverage against any email-borne attacks, including phishing, BEC, malware, and APTs.
Instant Messaging
Light speed protection against any file, URL or content-based attacks delivered via team messaging tools.
Cloud Apps
Stopping any content-based attack via any of your cloud-based collaboration apps in real-time.























