Cyber Threat Detection with Perception Point
Take back control of your organization’s security. Now, you can detect and prevent all major cyber threats across all channels, in under 30 seconds — from one, central platform.
See Perception Point in Action


One Platform. Seven Layers of Security.
Our multi-layered platform provides unprecedented cyber threat detection and prevention of APTs, phishing, malware, spam, BEC, ATO attacks, and more — delivered with the speed, scale, and flexibility of the cloud.
1Spam
Spam Filter
(Email Only)
Receives the email and applies reputation and anti-spam filters to quickly flag an email as malicious.
2Anti-evasion
Recursive
Unpacker
3Files & URLs
Threat Intelligence
4Files & URLs
Phishing Engines
5Files & URLs
Static Signatures
Combines best-in-class signature based anti-virus engines to identify malicious attacks. In addition, we’ve developed a tool that acts to identify highly complicated signatures.
6Text & Context
BEC & ATO
Prevents payload-less attacks that don’t necessarily include malicious files/URLs and intercepts account takeover attempts.
3Files & URLs
Threat Intelligence
4Files & URLs
Static Signatures
5Files & URLs
Phishing Engines
6Text
BEC
7Files & URLs
First Hardware-Assisted Platform (HAP™)
Unique CPU-level technology acts earlier in the kill chain than any other solution. Blocking attacks at the exploit phase – pre-malware release – for true APT prevention.
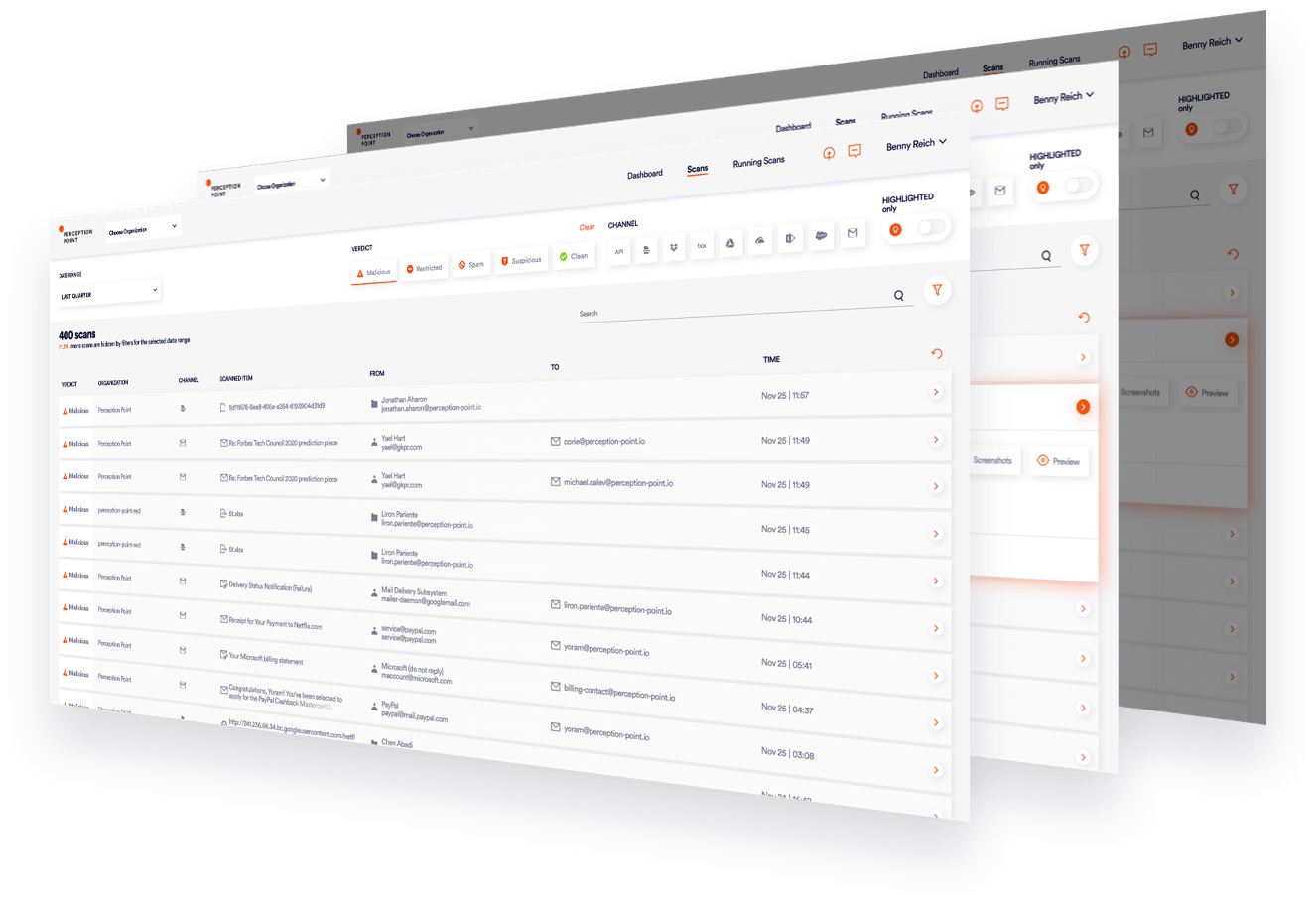
See our Advanced Threat Detection Platform in Action
See how Perception Point’s next-gen cyber threat detection platform can help you protect against any type of content-borne attack with 99.95% accuracy.
One Detection Platform for Any Cyber Threat
Protect against any content-based attack, including files, URLs, and plain texts. Deploy across channels, regardless to scale or traffic volume.
Zero-days
& N-days
Phishing
BEC
ATO & Lateral Phishing
Malware
Evasion
Unique Cyber Threat Detection Capabilities
Easy to Deploy
Easy to Use
No long manuals or complex
configurations needed.
Ultimate User Experience
Provides seamless experience for end-users with maximal efficiency and productivity.
Protection Against Any Attack Type
Outperforms all other solutions in accuracy and speed.
Unmatched Detection
Lowers dynamic threat analysis time from minutes into seconds – scanning 100% of content.
Managed
IR Service
Reduces SOC team resources by up to 75%, managing incidents and remediating threats.
Consolidation
in Action
One platform covers all threat types across email, web browsers and cloud collaboration apps.
Cyber Threat Detection Case Studies
Case Studies
-
Global Financial Services Firm Replaces Proofpoint A global financial firm faced challenges with preventing phishing attacks from reaching their users. Despite investing in security awareness training, the security leadership was concerned about phishing emails that were successfully bypassing their Proofpoint deployment.
-
Enhancing Microsoft Email Security to Prevent Advanced Phishing & BEC Attacks Perception Point’s Advanced Email Security for Microsoft 365 helps a global food distributor achieve seamless and comprehensive protection against advanced email-borne attacks including phishing and BEC.
-
Red Bull Augments Microsoft EOP to Prevent Attacks When given the opportunity to put our solution up to the test, Perception Point’s Advanced Email Security proved to be a cut above the rest.
-
Flow Control: Manufacturing Leader Selects Perception Point to Optimize Their Advanced Threat Protection With Perception Point’s consolidated solution protecting the customer’s email, browser, and Microsoft 365 suite, Flow Control Group benefits from simple deployment and holistic management capabilities.























