Scammers are hijacking hotels’ Booking.com accounts and using them as part of a hotel booking scam aimed at tricking guests into sharing their payment card information.
“Customers of multiple properties received email or in-app messages from Booking.com that purported to be from hotel owners requesting confirmation of payment details for upcoming stays,” Secureworks researchers warn.
“The threat actors directed the victims to malicious URLs for inputting the information, and then used the details to withdraw money from the victims’ accounts.”
The hotel booking scam
Secureworks outlined an attack that occurred in October 2023, when a scammer contacted a hotel’s operations staff member by email, pretending to be a former guest and claiming they had left their password at the property.
This first email did not contain links or attachments, i.e., nothing that would trigger email security scanners. It’s function was to establish the recipient’s trust and prime them for following the instructions in the second email.
A few days later, the scammer contacted the staff member via email again, ostensibly to provide a photo of the document in question and check-in details, downloadable from Google Drive.
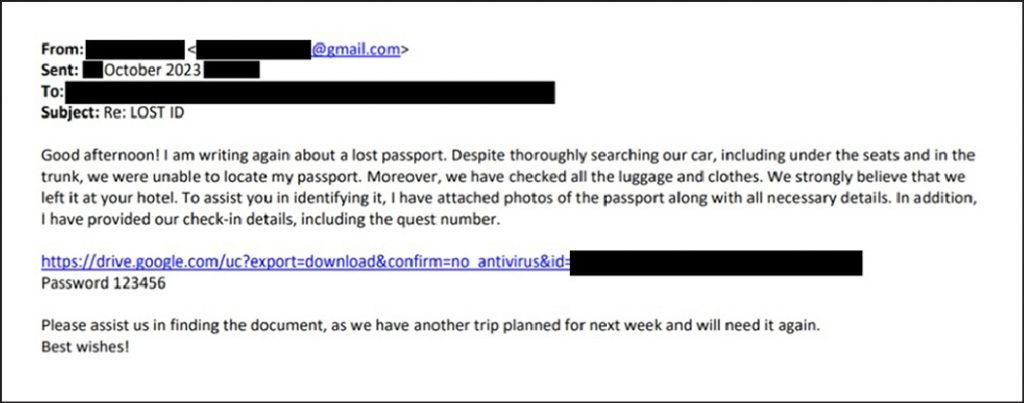
The downloaded ZIP archive file contained the Vidar infostealer, which harvested the credentials for the hotel’s Booking.com account, allowing the attacker to access the Booking.com management portal, access the list of upcoming bookings and directly send out emails to booked guests.
“The day after the malware was executed, a hotel employee observed that multiple messages had been sent to upcoming guests from the hotel’s Booking.com account. Several hours later, hotel customers started to complain that money had been taken from their accounts,” the researchers noted.
Previous campaigns
A few months ago, Perception Point researchers uncovered a similar campaign targeting hotels and travel agencies.
The attackers first booked a stay via email and, after having established trust with a member of the hotel’s operation staff, they would request specific favors (e.g., for the staff to print out a document, or to check whether the cleaning products used by the hotel contain specific compounds to which the guest’s child is allergic).
The first email would set the stage for the ask, and the second one contained the URL to the documents, hosted on legitimate services (Google Drive, Dropbox, Mega, etc.). As in the campaign outlined by Secureworks, the downloaded archive file actually contained an infostealer: Vidar, StealC, or Lumma.
“By weaving in scenarios involving family members with health conditions or specific needs, they tap into the victims’ empathy, effectively sidestepping rational scrutiny,” Perception Point researchers explained.
“Unlike typical phishing attacks that involve a single email, this campaign involves a series of interactions, making it more convincing. The password-protected archive adds another layer of perceived legitimacy, lulling the victims into a false sense of security.”
Hospitality industry and its customers are under attack
The hotel booking scam targeting Booking.com customers has been going on for a while.
“As far back as March 2023, two hotels posted messages on Booking.com’s partner support hub reporting that the official messaging mechanism was abused to defraud their customers. In August 2023, a third hotel contributed to the thread by including the contents of a message used to target one of its customers,” Secureworks researchers noted.
There have been news reports about losses suffered by hotel guests, and extensive forum threads by victims and almost-victims sharing their experiences of having been targeted, usually via Booking.com communication channels.
The scam seems to be highly successful and lucrative, and Secureworks has been seeing high demand on underground forums for Booking.com property credentials.
To protect themselves, organizations in the hospitality and travel industry are advised to:
- Implement multi-factor authentication on their Booking.com accounts
- Educate employees about these social engineering campaigns
- Double-check URLs before opening them
“Individual customers should be wary of emails or app messages requesting payment details, as they may not be legitimate,” the researchers noted. They should be suspicious of such messages even if they come through legitimate channels (i.e., from legitimate Booking.com accounts).
This article first appeared in Help Net Security, written by Helga Labus on December 4, 2023.























