As it turns out, hotels, and by extension, the hospitality industry, are not the most secure organizations around despite handling personal information and credit card details. This is evident in the recent MGM Hotel breach or even further back with the 2022 social engineering of Marriott. Now, an infostealer campaign is hitting hotels, travel agencies, and customers through advanced social engineering techniques, per recent research.
Earlier this month, researchers at Perception Point discovered an infostealer malware campaign specifically geared toward the hospitality industry. This attack begins with a threat actor booking a standard hotel reservation, as anyone would, and waiting for the confirmation email. Once the confirmation email is received, the attacker sends an email in reply with anything from “a query about making a new reservation or a reference to an existing one” with personal touches like mentioning family who might be joining the ‘trip.’
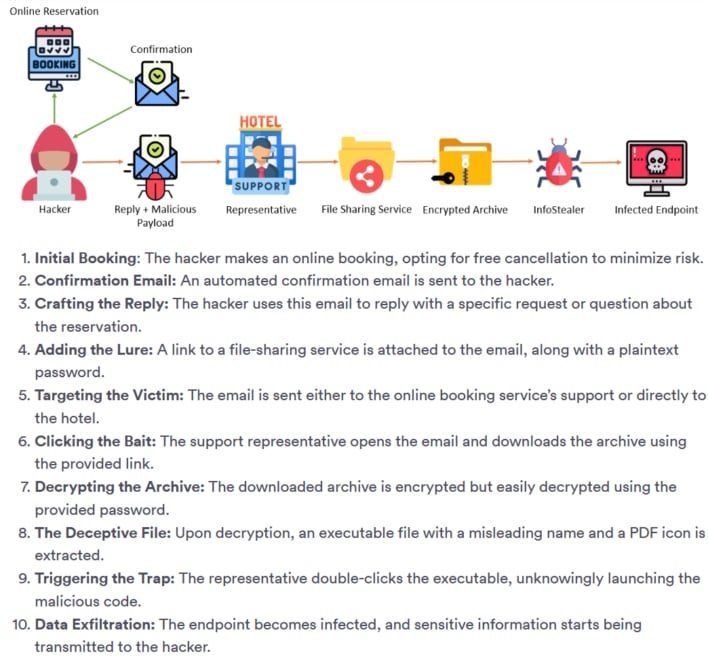
Once the attackers receive a reply to the initial contact, they will then send an email “crafted to elicit both empathy and a sense of urgency,” by mentioning a son with severe allergies or elderly parents who wish to have printed photos during the stay. Along with this email will be a link containing what the hotel employee would think are password-protected documents pertaining to the urgent request. However, this email points toward an archive file which, when downloaded and opened, “unleashes Infostealer-type malwares that infiltrate the victim’s system, siphoning off sensitive data.”
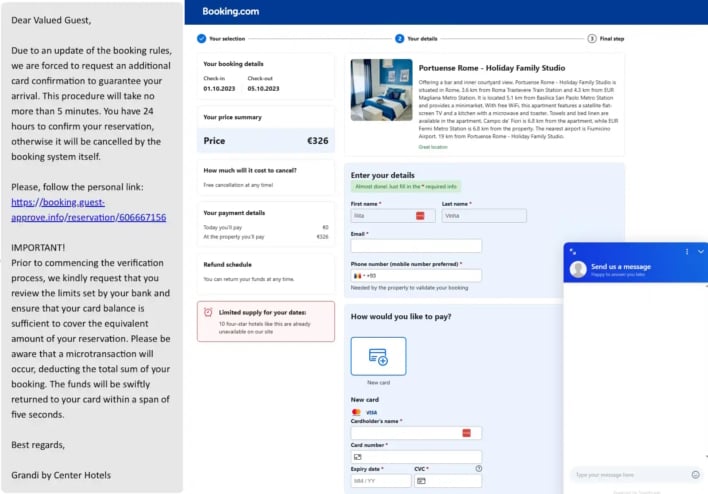
What is interesting, Perception Point researchers note, is that this is realistically a meticulously planned spear-phishing campaign with layers of interaction involving emotional manipulation, ultimately culminating in advanced infostealer executables that bypass detection. With this, it seems that attacks are not stopping at the hotel and are reaching customers as well. Researchers at Akamai report that through the infected hotel, attackers can message customers through seemingly legitimate channels with illegitimate phishing links to steal customer information directly in a sort of supply chain attack.
At the end of the day, humans will always be the weakest link in cybersecurity, as bad people can make plays toward ethos, pathos, and logos to further their goals. However, knowing this alone and pausing to assess content can help everyone stay safe from attacks in email, media, or otherwise. Moreover, people should never click on random or unsolicited links, be wary of all URLs, and contact companies directly through known means, like phone or alternate email, outside the channel used for messages or requests. It is getting ever harder to tell what is real or fake in this day and age, but with some close inspection and care, phishing should not be a problem.
This article first appeared in Hot Hardware, written by Nathan Ord on September 22, 2023.























