Why Browser Security is a Concern
The main vehicles for delivering attacks such as ransomware, phishing, BEC, malware, etc. are email and an ever-increasing variety of web-based SaaS apps including collaboration, messaging, cloud storage, and others, all accessed via the browser. This is why browser security is on the top of mind with CISOs today.
At Perception Point we’re dedicated to delivering a best-in-class managed service that protects our customers against all user threats.

How Perception Point Prevents Attacks
Perception Point is continuously perfecting its prevention as a service portfolio, for securing email and collaboration apps, including Office 365, Google Workspace, Slack, Teams, Salesforce, and other popular apps, all via a modern integrated API-based approach.
We are able to achieve amazing detection accuracy without standing in the way of users’ productivity. The service is able to complete URL/file scans within ~10 seconds on average, while still dynamically scanning all content recursively. And thanks to our dedicated 24×7 incident response service, security teams can now sleep soundly and focus only on the most critical incidents in their organizations.
We’ve been working on tackling the next top attack vector: the browser. As the vast majority of modern apps are now web-based, external attacks often use malicious websites and/or file downloads to breach organizations. Furthermore, malicious insiders and 3rd parties can easily extract data from web-based enterprise apps that do not yet have the necessary security controls.
However, web security solutions have pretty much stayed the same and have not caught up with the frontier that digitization and remote working bring, and the browser, which is the front line of attacks, remains exposed.
The Browser Security Solutions Landscape has been Lacking
SWGs
For example, Secure Web Gateways (SWGs) attempted to secure the web by tunneling and inspecting all web traffic. With the wide adoption of cloud apps, proxying all traffic through an SWG makes less sense and can become very expensive. Furthermore, as services become increasingly encrypted end-to-end, SWGs become less and less useful as they cannot inspect these services. They also lack visibility into the browser and as a result cannot help protect against threats like malicious data-stealing browser extensions and insider threats. SWGs can also impact the user experience, add latency and sometimes falsely block users from getting their jobs done.
Some SWGs include Remote Browser Isolation (RBI) as part of their solution in an attempt to allow users to access some resources that were previously blocked. However, forcing users to use a remote browser and manipulating website content often leads to user frustration due to a degraded/laggy user experience, website/browser compatibility issues, and increased costs as enterprises need to pay for remote VMs/containers running full browser sessions.
Custom Enterprise Browsers
Another web security approach focuses on browser security and offers custom enterprise browsers. These products require enterprises to replace their existing browsers with custom-made hardened browsers. However, Google and Microsoft are innovating fast in the browser space and adding unique features that are only available through their ecosystems and are not part of the Chromium engine. So organizations that select to use a custom browser will not be able to adopt these innovations, and will also experience a lack of interoperability with manageability and security features from Google and Microsoft and related solutions that plug into their systems. Furthermore, these emerging custom browsers run as standard apps and are exposed to the same wide attack surface as the standard browsers – they cannot add significant isolation guarantees and lack in-depth detection capabilities.
Ideal Browser Security Solution
We believe that modern web security solutions that focus on browser security must allow users to leverage their standard Chrome or Edge browsers without experiencing significant latency while benefiting from full compatibility with the web and the Microsoft/Google ecosystems.
Users need to be able to browse any website/cloud service and get the full functionality of these browsers, including logging in to their work profiles, password management, the ability to leverage browser extensions, and any other of the browser vendors’ innovations. Admins must be able to enjoy browser manageability features from Microsoft and Google, as well as ensure interoperability with Zero Trust, identity providers, and other access management solutions.
At the same time, we must significantly strengthen the security offered by standard browsers, including better, deeper, and earlier detection, built-in data loss prevention, and strong threat isolation that dramatically reduces the attack surfaces. To further increase an organization’s security posture, rapid remediation of threats by both external and internal threat actors must be supported.
Introducing Perception Point Advanced Browser Security, a new Web Security Solution
Wondering how to prevent ransomware, phishing, and other cyberattacks with Perception Point?
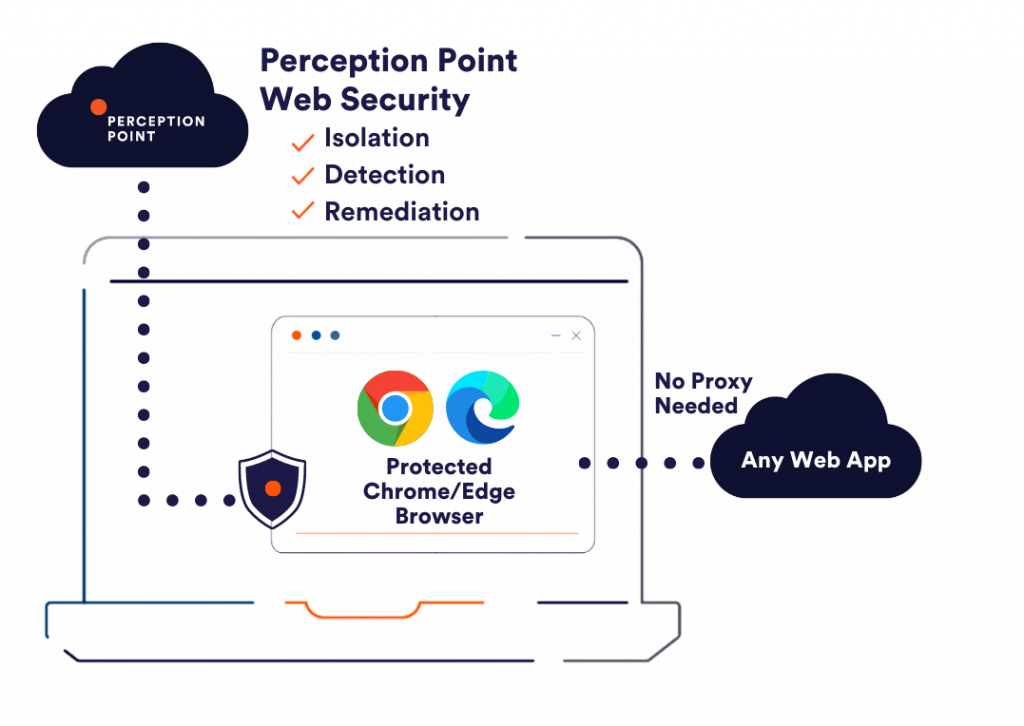
We’re excited to announce our new Perception Point Advanced Browser Security, which adds enterprise-grade security to standard Chrome, Safari, and Edge browsers. Advanced Browser Security ensures that access to harmful web content is fully isolated, leveraging OS virtualization technology. Enterprises can also leverage our browser security technology to protect access to enterprise web apps on 3rd party endpoints or to isolate privileged web apps on internet-exposed corporate endpoints, preventing data loss by design.
Perception Point’s Advanced Browser Security uniquely lets users browse natively without any significant latency and is fully compatible with all websites and common browsers; all while providing best-of-breed isolation of high-risk websites.
Furthermore, our integrated multi-layered dynamic detection capabilities instantly block access to malicious/phishing websites and to malicious file downloads including malware, ransomware, APTs and more, without the need to tunnel all traffic through a secure web gateway or VPN.
Detection and prevention are done within the browser at an early stage of the attack to stop the malicious actors in their tracks. The icing on the cake is that the user experience stays the same and it’s business as usual.
When combined with Perception Point’s email security, cloud-collaboration protection, and 24/7 managed Incident Response service, security teams can be rest assured that they are completely covered across all user attack vectors and the evolving landscape of threats. Our multi-layered detection engines provide visibility into attacks across multiple channels and use this wide context to intercept and remediate, if necessary, all attacks whether they start in the user’s browser, on email, or any other collaboration/file storage app.
Perception Point Advanced Browser Security is easy to deploy, either via a browser extension (for threat prevention capabilities only) or via a light agent adding VM-based isolation to Chrome/Edge/Safari on Windows or Mac. Moving forward, we will double down on our web security solution to make sure organizations can rely on Perception Point’s service to stop all user-centric attacks, on any app.
If you want to reduce breaches, free your users to browse the web and access files, and reduce your costs, take a look at our new web security portfolio today.
























