This article will explain the challenges in detecting phishing, provide best practices and introduce advanced technologies that will help organizations learn about how to prevent phishing attacks.
Phishing attacks are scams where attackers attempt to extract sensitive data or personal information by impersonating a trusted source, usually a well-known organization. Attackers aim to trick individuals into providing sensitive information such as passwords, credit card numbers, or other personal data.
According to the Anti-phishing Working Group latest report, phishing attempts hit an all-time high in December 2021; Attacks have tripled since early 2020. In today’s reality, phishing attempts occur on a daily basis, reaching people via their private and company email accounts.
Phishing prevention refers to measures taken to protect individuals and organizations from falling victim to phishing scams. Some tips that can help end-users prevent phishing are knowing what a phishing scam looks like, avoiding clicking links, never giving away information to an unsecured site, ignoring pop-ups, and opening suspicious documents in an isolated environment.
In this article
What is Anti-phishing?
Anti-phishing involves deploying strategic defenses to prevent or mitigate phishing attacks, where cybercriminals impersonate trusted sources to steal sensitive information. This practice combines human vigilance with sophisticated software solutions. Key components include:
- Email Filters: Anti-phishing software blocks suspicious emails from reaching users, filtering out messages with misleading links or deceptive requests.
- Link Analysis: These systems prevent users from engaging with harmful links contained within emails, reducing the risk of successful attacks.
- Integrated Anti-Malware: Working in conjunction with anti-malware, anti-phishing tools scan incoming emails and attachments for malicious content, effectively blocking these threats before they impact the user.
- Comprehensive Security Measures: Overall, anti-phishing efforts encompass a broad range of security measures, both preventive and corrective, ensuring a multi-layered defense against the evolving landscape of cyber threats.

Tal ZamirCTO, Perception Point
Tal Zamir is a 20-year software industry leader with a track record of solving urgent business challenges by reimagining how technology works.
TIPS FROM THE EXPERT
- Comprehensive Employee Training and Awareness Programs: Conduct regular training sessions to educate employees on identifying phishing attempts, including recognizing suspicious emails, links, and attachments. Implement simulated phishing campaigns to test employees’ responses and reinforce training. Provide feedback and additional training to those who fall for the simulations. Establish and promote a clear procedure for reporting suspected phishing attempts. Ensure that employees know who to contact and how to report suspicious activity.
- Implement Multi-Factor Authentication (MFA): Enforce multi-factor authentication for accessing all critical systems and data, reducing the risk of compromised credentials being used for unauthorized access. Use dynamic and context-aware authentication methods that adapt based on the user’s location, device, and behavior.
- Email and Domain Security Measures: Implement DMARC, along with SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail), to protect your domain from being used in phishing attacks. Set up advanced email filtering rules to automatically flag or quarantine emails that contain common phishing indicators, such as spoofed addresses or suspicious attachments.
- Strengthen Access Controls and Permissions: Implement the principle of least privilege, ensuring that employees only have access to the information and systems necessary for their job functions. This reduces the risk of phishing attacks gaining access to critical systems. Conduct regular audits of user access rights to ensure compliance with access control policies and to identify and revoke unnecessary permissions.
- Establish Incident Response and Recovery Plans: Develop and regularly update an incident response plan that outlines the steps to be taken in the event of a phishing attack. Ensure all employees are aware of the plan and their roles within it. Have robust data backup and recovery procedures in place. Regularly test these procedures to ensure that data can be restored quickly and accurately in case of an attack. Conduct a thorough analysis after any phishing incident to understand how it happened, assess the impact, and implement measures to prevent future attacks.
What are Common Types of Phishing Attacks?
Attackers may choose to employ various types of phishing attacks. The attacks will usually use a common set of phishing techniques, but vary concerning their targets and the channels leveraged in the attack.
Examples of phishing attacks include:
- Email phishing – a classic example of phishing where a malicious message that looks legitimate, lures victims to click a link, open a file or provide their valuable credentials;
- Spear phishing – phishing targeted to a specific person that the attacker has prior knowledge of;
- Whaling – in this type of phishing attack the attacker targets high-profile personas, such as C-level executives.
Related content: Read our guide to phishing types
7 Tips to Prevent Phishing Attacks in Your Organization
1. Provide Anti-Phishing Tips and Training to Your Employees
Providing training to employees is an important aspect of phishing prevention in organizations. Employees need to know what phishing scams look like, in order to actively prevent them. The training can cover topics such as:
- Understanding the types of phishing scams: Educate employees about different types of phishing scams, including email, text message, and phone phishing.
- Spotting the signs of a phishing email: Teach employees how to identify common indicators of a phishing email, such as urgent language, suspicious sender addresses, and requests for personal or sensitive information.
- Not clicking on links: Employees need to be extremely careful when clicking on links, whether in email communications or on the web.
- Blocking popups and ads: Employees should be instructed on how to block popups and ads, because these might contain malicious links or other threats.
- Never giving away private information: Employees should know never to divulge passwords or any sensitive information without carefully verifying the source and reason for the request.
- Safe practices for handling emails: Emphasize the importance of not opening attachments and verifying the legitimacy of emails before taking any actions. If absolutely necessary, employees should open suspicious documents in an isolated environment.
- Reporting phishing attempts: Encourage employees to report any phishing attempts they receive, so that the organization can take appropriate measures to prevent further attacks.
By providing regular training to employees, organizations can help create a culture of awareness and vigilance that can help prevent phishing attacks.
2. Utilize End-to-End Encryption
End-to-end encryption ensures that the data being transmitted between two points can only be read by the intended recipients and not intercepted by any third party. This makes it more difficult for attackers to intercept sensitive information, such as login credentials, credit card numbers, or confidential business information. To implement end-to-end encryption, organizations can use tools such as encrypted email services and encrypted instant messaging tools.
3. Conduct Simulated Phishing Attack Tests
It is critical to show employees what a phishing attack looks like, giving them real-life experience with the threat. Simulated phishing attack tests are designed to mimic real-world phishing attacks and measure an organization’s susceptibility to these threats. These tests can be conducted in various ways, including sending mock phishing emails to employees and tracking who falls for the scam.
The results of these tests can be used to improve the organization’s phishing prevention efforts by:
- Identifying vulnerable areas: By discovering which employees are most susceptible to phishing attacks, organizations can identify areas where additional training is needed.
- Evaluating the effectiveness of current security measures: The results of simulated phishing tests can help organizations assess the effectiveness of their current security measures, such as email filters and anti-phishing tools.
- Improving employee awareness and vigilance: By conducting simulated phishing tests, organizations can help employees become more aware of the threat of phishing and more vigilant in detecting and avoiding these attacks.
4. Domain-Based Message Authentication, Reporting and Conformance (DMARC)
DMARC is an email authentication protocol designed to protect organizations against phishing and email spoofing attacks. It works by allowing a domain owner to publish a policy in their domain’s DNS records, specifying which mail servers are authorized to send an email on behalf of the domain, and what action receiving mail servers should take when a message fails DMARC evaluation.
DMARC uses two other email authentication protocols, SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail), to verify the authenticity of the sender’s domain. If a message fails DMARC evaluation, it can be treated as spam, rejected, or quarantined, depending on the policy specified by the domain owner.
To implement DMARC, the domain owner must create a DMARC record in their DNS, which includes the following information:
- The domain owner’s email policy (e.g., to reject all unauthenticated messages).
- Reporting instructions for receiving mail servers (e.g., to send DMARC reports to the domain owner).
By publishing a DMARC record, organizations can protect their domains from being used in phishing attacks, increase the security of their email communications, and maintain control over the reputation of their domains.
5. Use Passwords with Phishing-Resistant Multi-Factor Authentication (MFA)
Phishing-resistant MFA is a type of multi-factor authentication that offers immunity against attempts to compromise the authentication process, typically through phishing attacks. This is achieved by requiring not only proof of identity but also proof of intent through deliberate action. A FIDO authenticator is an example of a phishing-resistant MFA that provides both security and a smooth user experience.
Phishing-resistant MFA provides stronger security than traditional MFA by eliminating the risk of using passwords or shared secrets, and helps organizations meet security and regulatory requirements. It assures consumer identity and enhances compliance with Single Sign-On solutions.
6. Using Antivirus and Cloud Email Security Solutions
At a bare minimum, organizations should deploy antivirus and anti-malware solutions and keep them updated, as these can protect against malware deployed by phishing techniques.
However, cloud email security solutions go several steps further than basic antivirus tools, providing a centralized, cloud-based platform for securing email and protecting against phishing, malware, and other cyber threats.
Cloud email security solutions typically provide the following key features:
- Anti-phishing: Protection against phishing attacks by filtering out suspicious emails and marking them as spam or quarantining them.
- Anti-malware: Protection against malware by scanning incoming emails and attachments for malicious content and blocking it from reaching the user.
- Anti-spam: Protection against spam by filtering out unwanted emails and marking them as spam or quarantining them.
- Data loss prevention (DLP): Protection against data loss by identifying and blocking sensitive information from leaving the organization via email.
- Encryption: Encryption of emails and attachments to protect sensitive information from unauthorized access.
7. Using Dedicated Anti-Phishing Solutions
Anti-phishing software can help detect and prevent phishing attempts by:
- Filtering emails: Anti-phishing software can scan incoming emails for signs of phishing, such as suspicious sender addresses and links to known phishing sites. These emails can then be automatically blocked or sent to a quarantine folder.
- Blocking malicious websites: Anti-phishing software can prevent employees from accessing known phishing websites, helping to reduce the risk of successful attacks.
- Monitoring network activity: Anti-phishing software can also monitor network activity, looking for signs of phishing activity and alerting IT staff to potential threats.
- Providing real-time protection: Anti-phishing software can provide real-time protection against phishing attacks, helping organizations stay ahead of these evolving threats.
The Danger of Advanced Phishing Techniques
Common phishing techniques will lure victims to enter their credentials or to click a malicious link. But there are many more advanced techniques employed by attackers that make phishing difficult to detect. We’ll give a couple of examples.
Phishing Sites Using Legitimate Domains: Website builder tools like Weebly or Wix are providing attackers with free, quick and simple templates to build sites for attacks. Since these websites are delivered via legitimate links, e.g. a site hosted on Wix platform, they are hard to spot and require a combination of abilities from advanced threat detection tools, such as the ability to add new logic that will recognize new malicious URLs on the go, ability to adjust image recognition capabilities to recognize new phishing site URLs and more.
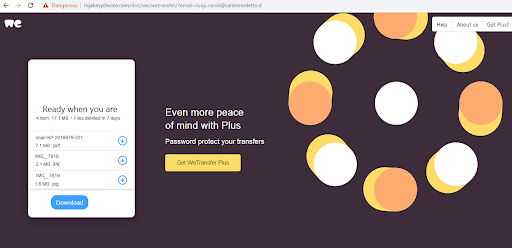
Phishing Attacks using legitimate file hosting services: Services such as WeTransfer and JUMBOmail can be easily and freely used by attackers to deliver malicious files. These websites obviously pass as legitimate sites, so Advanced Threat Detection solutions will need to actually scan and intercept each file before it is delivered or downloaded by the user, and files can be quite large so scanning speed can be an issue.
How to Prevent Phishing with Next-Generation Anti-Phishing Technology
The task of protecting employees and organizations from phishing attacks is not an easy one, however there are key techniques that advanced threat detection security solutions must provide in order to sufficiently protect against these attacks from ever successfully entering end-user inboxes.
Identifying Brand Impersonation with Image Recognition
In brand impersonation phishing attacks, attackers impersonate targeted popular brands using the brand logo, brand signature, brand color pallet and language, and more. An excellent example can be seen in this recent OpenSea phishing attack where you cannot see the difference between the malicious and actual site:
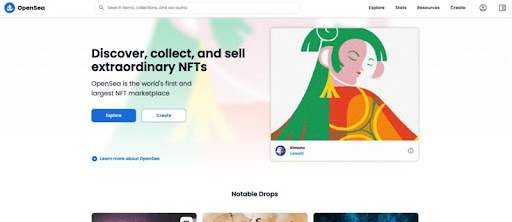
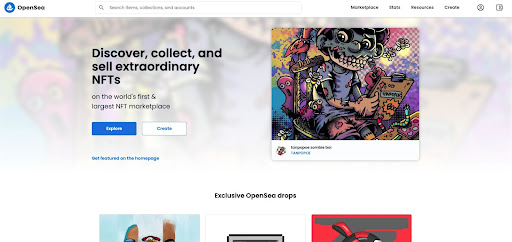
Image recognition is a key technology used to be able to validate if any URL is actually the legitimate site it is claiming to be. Similarities that are difficult to identify using human eyesight are easily caught using algorithms that know the original brand and analyze the potentially malicious content (e.g. an email, or a URL) against it – not leaving it up to chance, if the user is able to spot the attempt or not.
Identifying Malicious URLs with Lexical Analysis
Lexical analysis is another technique, helpful in determining if a URL is malicious or not. In Lexical analysis, the structure of the URL is analyzed to detect:
- If it contains suspicious words
- How many parameters are passed inside the URL
- What type of encoding is used to encode the parameters
- If the URL contains email address or suspicious domain names, and more
Analyzing Reputation Vectors of Sender and Recipient Parameters
A Reputation vector is the collection of parameters maintained on both the sender and recipient, derived from the data and metadata collected on them. Information collected could be related to the legitimacy of the IP or the domain that the email is being sent from and more. The reputation vector will ultimately result in a score that will assist in making the decision if any type of content is malicious or not.
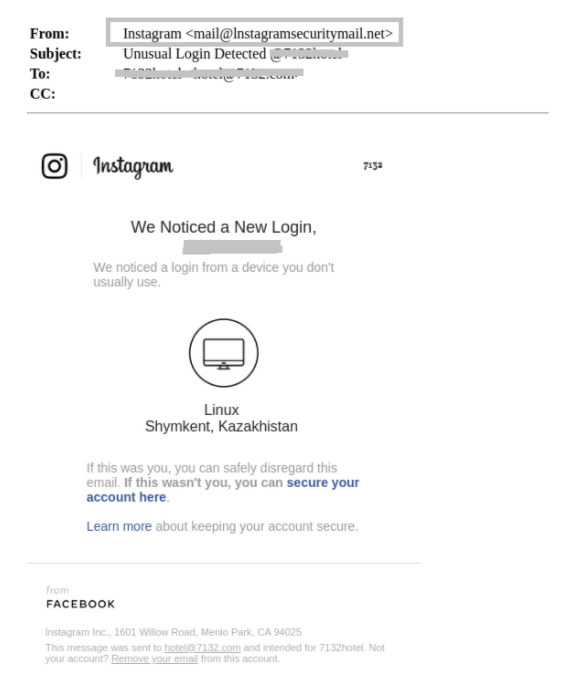
Identifying Smartly Spoofed Domains with Advanced Algorithms
Attackers will use similar domain names that are visually very close to popular brands that they are spoofing. A standard approach to address spoofed domains is to use a database of known domains, for example: Coca Cola and Microsoft, and then counting the amount of differences. While this technique can work in some cases, it can be challenging to identify more sophisticated obfuscations.
Novel algorithms, available in advanced email security solutions, significantly lower the success rate of such evasion attempts. A good example is usage of biological algorithms that have been found to significantly help identify such spoofing attempts.
Dynamically Scanning URLs via Sandboxing
In addition to using the techniques mentioned above, and checking potential threats against threat intelligence sources, it is critical to dynamically scan all URLs, including the ones buried several levels deep inside the original content that was sent. Scanning all URLs dynamically, also referred to as “Sandboxing”, will make sure new and unseen attacks, or new senders that look legitimate but actually are not, are identified. Next generation sandbox technologies will perform this scan in a speedy and accurate manner, getting rid of “traditional” sandboxing technologies’ delays.
How to Prevent Phishing with Perception Point Email Protection
As cyber crimes escalate, companies need to fortify their cyber security systems even more substantially. Get ahead of these types of phishing by having a dependable email security provider, allowing your team to focus on what matters.
Start today with Perception Point’s email security platform. We offer comprehensive email security that eliminates threats before they reach your employees. Our end-to-end advanced cyber threat detection protects your enterprise against modern-day phishing scams.
Stay on top of the latest email security trends through our other blog posts and resources.
Want to know how we stop phishing at Perception Point? Contact us for a live demo.

Phishing prevention refers to measures taken to protect individuals and organizations from falling victim to phishing scams.
Anti-phishing involves comprehensive security measures implemented by individuals and organizations to guard against phishing attacks.
Examples of phishing attacks include:
– Email phishing – a classic example of phishing where a malicious message that looks legitimate, lures victims to click a link, open a file or provide their valuable credentials;
– Spear phishing – phishing targeted to a specific person that the attacker has prior knowledge of;
– Whaling – in this type of phishing attack the attacker targets high-profile personas, such as C-level executives.
1. Provide Training to Your Employees
2. Utilize End-to-End Encryption
3. Conduct Simulated Phishing Attack Tests
4. Domain-Based Message Authentication, Reporting and Conformance (DMARC)
5. Employ Phishing-Resistant MFA
6. Cloud Email Security Solutions
7. Using Dedicated Anti-Phishing Solutions
– Identifying Brand Impersonation with Image Recognition
– Identifying Malicious URLs with Lexical Analysis
– Analyzing Reputation Vectors of Sender and Recipient Parameters
– Identifying Smartly Spoofed Domains with Advanced Algorithms
– Dynamically Scanning URLs via Sandboxing
























