What is an invoice redirect attack?
An invoice redirect attack is a malicious technique aimed at businesses and organizations. Attackers impersonate trusted vendors and send seemingly legitimate emails to their targets. The emails include invoices with payment links. However, these links actually redirect to spoofed payment sites orchestrated by the attacker. Once a target clicks on the link and enters their financial information, the attacker is ready to steal the sensitive data.
Invoice redirect attacks have become an increasingly effective way for attackers to exploit businesses. Attackers prey on the fact that organizations often pay invoices without careful verification. That, coupled with spoofed payment pages nearly identical to their legitimate counterparts has created a dangerous attack method threat actors are eager to adopt.
Now that we know what an invoice redirect attack is, let’s look at some real life examples. Keep reading to learn more.
Waiting in the Void
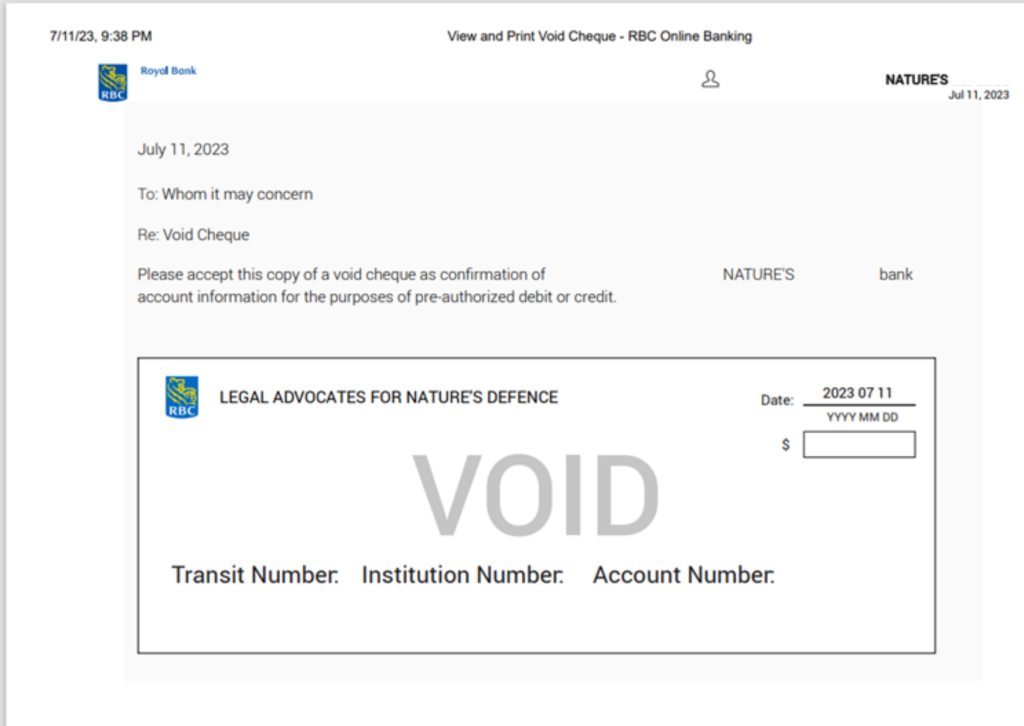
This first attack began when one of our customers reached out to a vendor, requesting a void check to complete a payment. The vendor quickly replied, attaching a seemingly harmless PDF file, containing the requested void check.
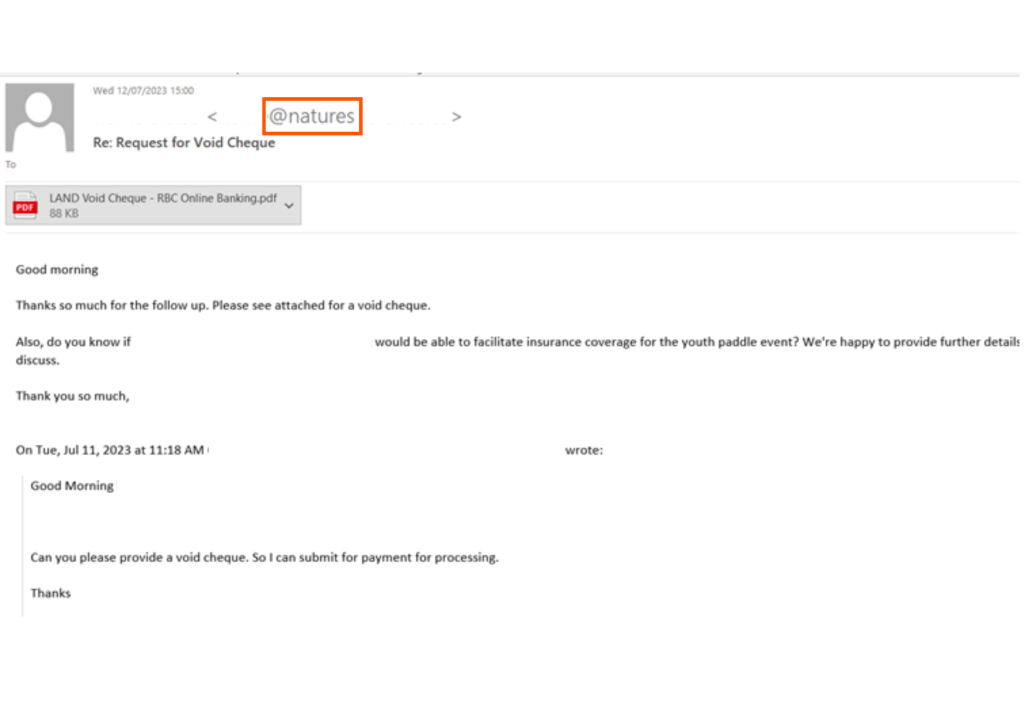
Within hours, the attacker began executing their malicious pursuit. First, the attacker established a new domain, expertly crafted to spoof that of the legitimate vendor. The legitimate domain was “naturesdefence.ca,” while the spoofed domain became “naturedefence.ca” (missing the “s”). Next, the attacker created a new mailbox with the spoofed domain, assuming the identity of the vendor. This served to establish a sense of legitimacy and trustworthiness, setting the stage for the final step.
Finally, the attacker sent an email from the spoofed domain, claiming that the bank details provided earlier were no longer valid. The attacker attached a PDF file with the same name as the one from the legitimate conversation. The only difference between the two files was an altered account number for payment, designed to divert funds into the attacker’s account.
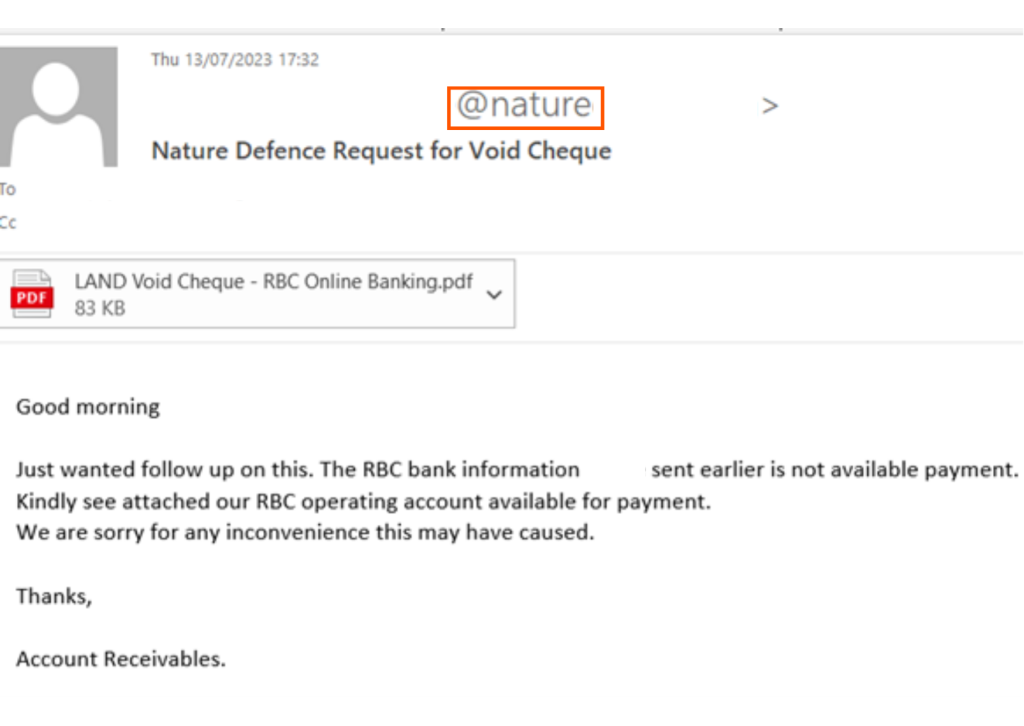
What is interesting in this attack is the attacker’s aim to gain access to a legitimate void check. The attack can only execute this goal by compromising one of the parties involved. Since Perception Point provides our customer with comprehensive ATO protection, it is safe to say that the vendor’s account was compromised in this case.
Unlike most attackers that jump to capitalize on compromised accounts, this attacker displayed exceptional patience. They strategically waited until the vendor took the initiative to start payment discussions. Letting the vendor lead the conversation before hijacking the thread lessens the victim’s suspicion and ultimately lends an air of legitimacy to the attack. Moreover, the victim’s intent to make a payment makes them more inclined to heed the attacker’s instructions.
The Chameleon Approach
In these next BEC attacks, attackers attempt to redirect large sums of money using legitimate invoices through domain lookalikes (with a twist).
The attacker begins by compromising a vendor’s account and gaining access to a legitimate invoice. From there, the attacker establishes a lookalike domain. Armed with this new domain, the attacker sends the invoice to the intended target, impersonating the legitimate vendor.
Since the invoice is real, charging for legitimate goods and services, and the email contains all the accurate details, including an accurate signature and the recipient’s name, there is no cause for suspicion. To the recipient, it appears to be just another invoice from a trusted associate.
The true maliciousness of the attack lies in the twist. The attacker creates a new Gmail mailbox account, impersonating the vendor’s accounting department. They then send an email to the from this new mailbox, notifying that all future invoices must be paid using updated ACH information format. To reduce suspicion, the attacker requests an ACH change form or, if one is unavailable, offers to email the new ACH details. To further enhance credibility, the email includes the same real invoices as in attachment and the vendor’s company signature.
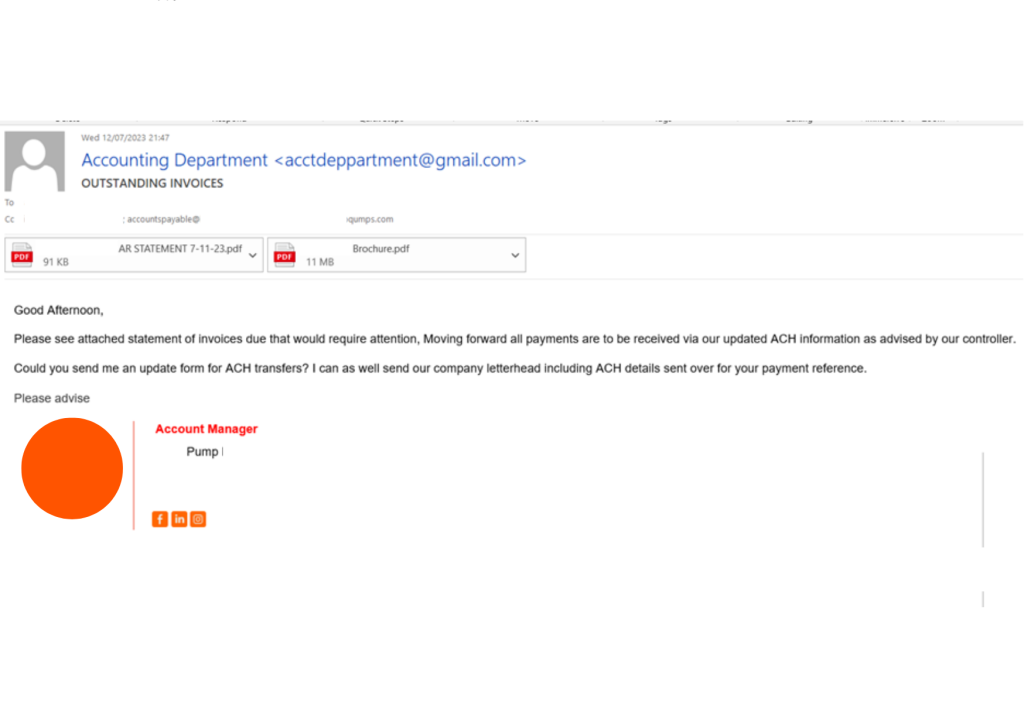
Perception Point’s advanced threat prevention platform successfully detected and prevented three of these attacks, each targeting different customers and impersonating different vendors. This complex BEC method seems to originate from a single threat actor. In total, the attacker attempted to gain over $600,000 from our customers. Fortunately, Perception Point’s Advanced Email Security had other plans.
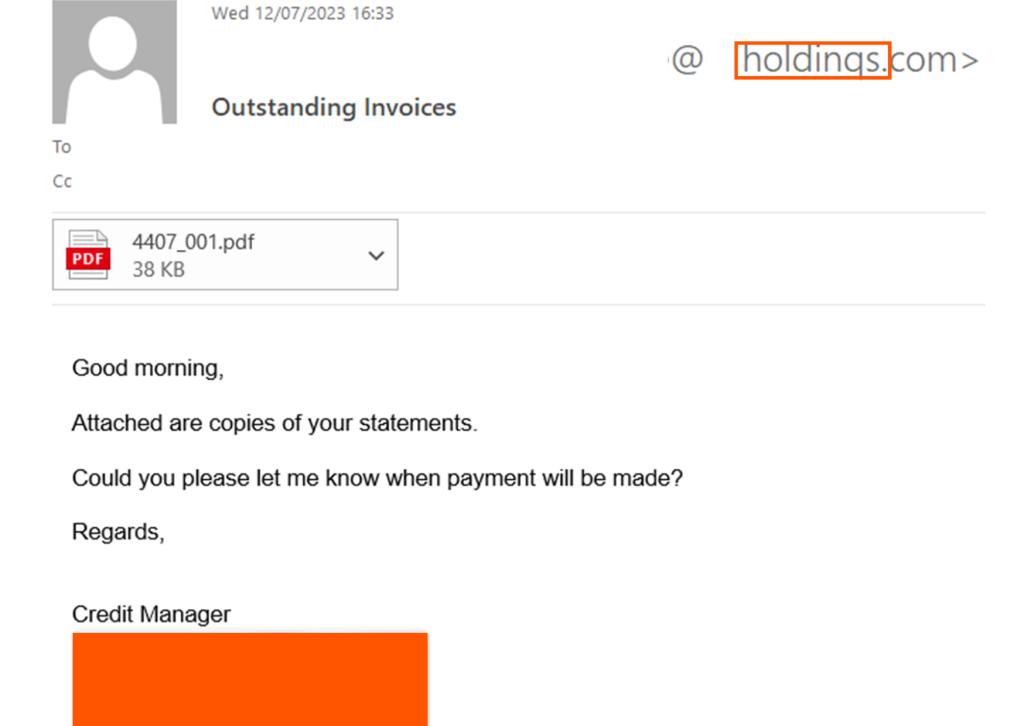
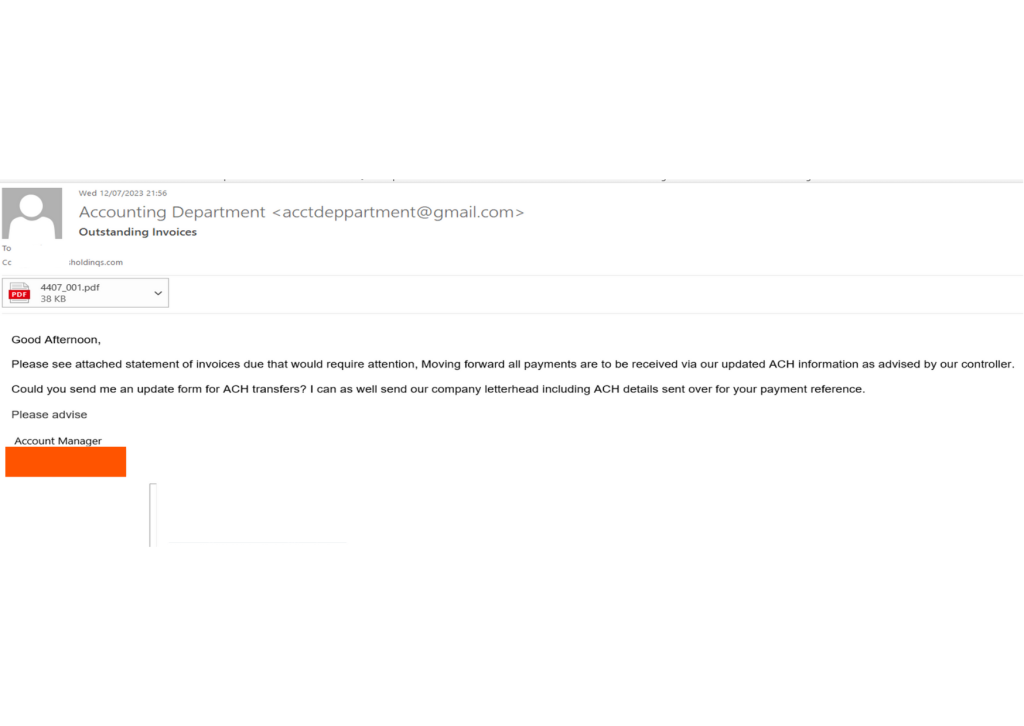
In this attack, the attacker used Gmail to evade email security solutions. Unlike new domains or impersonations of vendors, Gmail has a reputable domain reputation, making detection even more challenging. Additionally, the attacker’s use of two different email addresses in these attacks presents a formidable challenge. Most email security solutions analyze each email independently; detecting anomalies across multiple events requires extremely advanced and sophisticated models, making it unlikely for them to catch these advanced attacks.
Squeezing the Lemon
In this BEC attack, the attacker impersonates a vendor and requests a payment method update, trying to convince our customer to make payments to a fraudulent account.
The attacker starts by creating a new email domain almost identical to the legitimate email domain used by the vendor. From this new domain, they send emails to multiple clients, announcing a change in bank account information. They instruct the recipients to direct all future payments to the new account. Since the attacker uses a domain closely resembling the vendor’s, it is challenging for recipients to detect the deception at first glance.
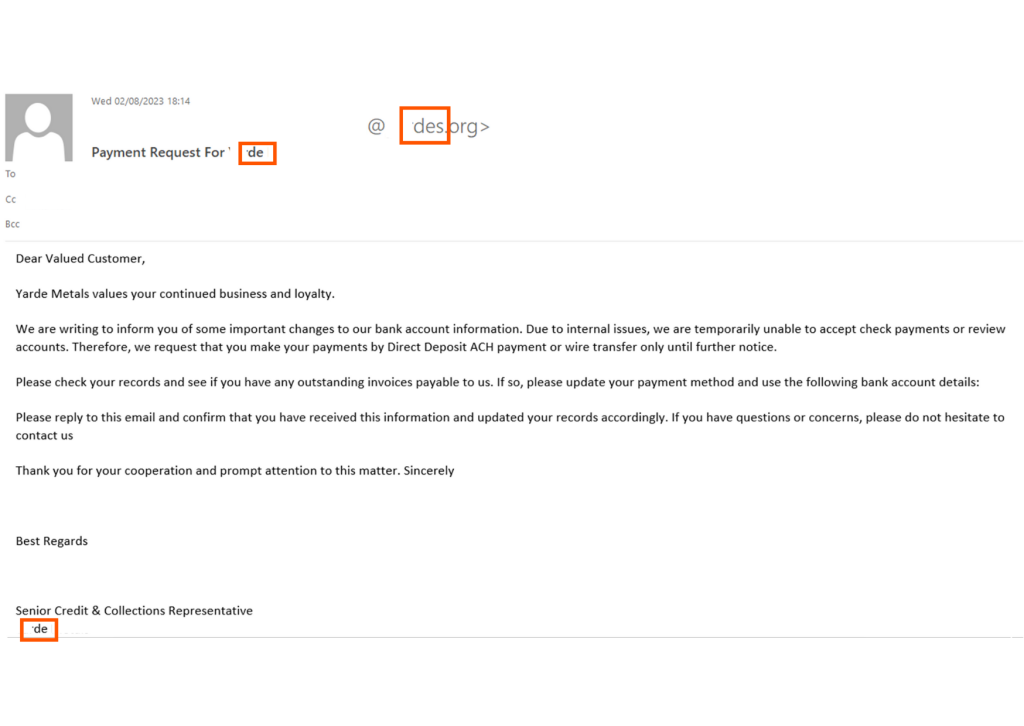
But what truly sets this attack apart is the striking commonality among the victims – they all have real business relationships with the impersonated vendor. This indicates that the attacker gained an in-depth understanding of the vendor’s operations before acting, enabling them to carefully select their targets. It also suggests that the attacker has compromised multiple accounts belonging to the vendor in order to obtain invaluable insights into their business relations and communication patterns.
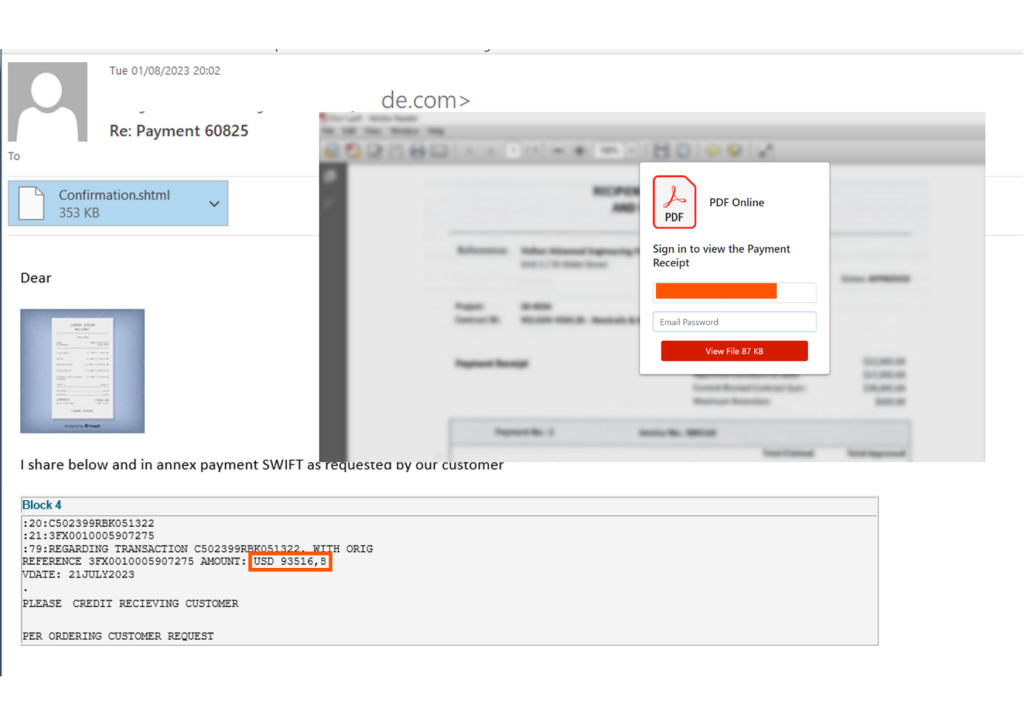
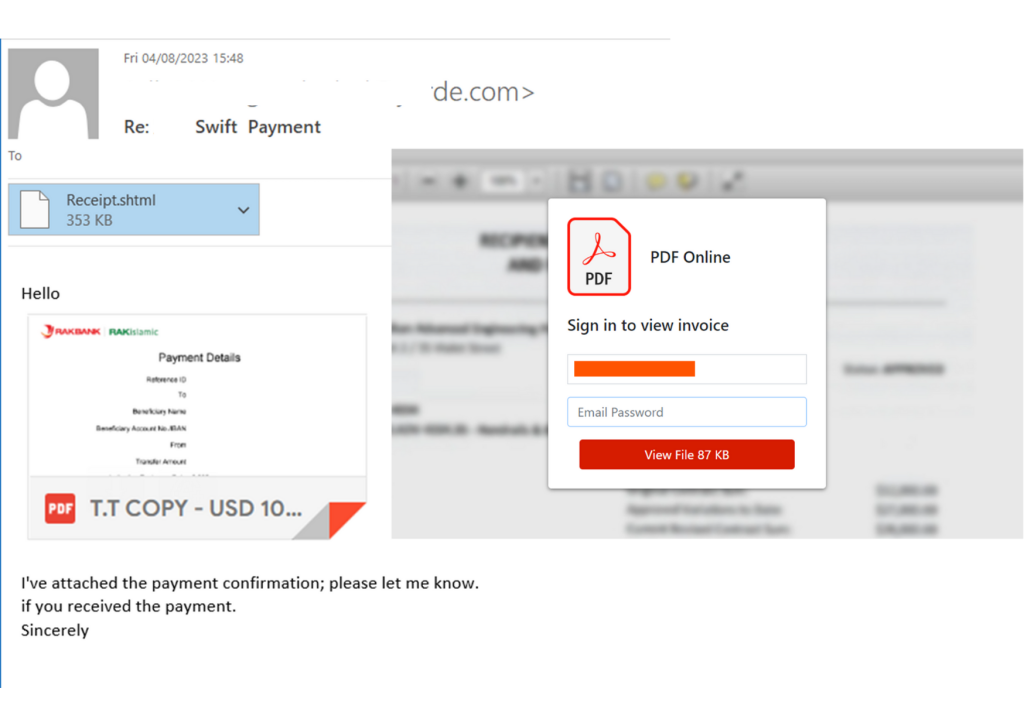
Perception Point also intercepted malicious phishing emails sent from the actual domain belonging to the vendor. The phishing emails were sent from multiple different recipients, indicating that there is a major breach on the vendor’s side.
Cash in on Perception Point
Perception Point managed to stop all of these complex BEC attacks before they reached our customers due our state-of-the-art ML models. Our defense strategy boasts a multi-layered approach, combining various advanced ML models and anomaly detection techniques.
The initial step in our defense is supply chain recognition, in which we employ sophisticated ML models to classify our customers’ business partners accurately. Our models do not just recognize vendors, but we also maintain a dynamic list of potentially breached vendors, a feature that helps our system to make decisions in real time.
This has enabled us to apply additional advanced ML models for detecting potential spoofing attempts targeting these trusted entities. These models incorporate both content-based analysis, such as Natural Language Processing (NLP), and visual-based analysis using computer vision techniques.
Furthermore, our system runs advanced anomaly detection models that promptly raise red flags when suspicious events occur. This involves running NLP models on files to detect sensitive information like account numbers or conducting periodic big data queries to identify these potential anomaly cases.
For more information on how Perception Point leverages generative AI to defend against BEC attacks, read:
An AI for an AI: LLM-based Detection of GPT-Generated BEC Attacks
Fighting Fire with Fire: Combatting LLM-Generated Social Engineering Attacks With LLMs























