Last year we wrote a blog post about phone scams. Our IR team detailed the sophisticated “Geek Squad Phone Scam”, in which victims were prompted to call “customer support” to cancel a fraudulent subscription charge. Upon calling the provided number, a scammer would walk the victim through the necessary steps to give the attacker access to their computer. If an attacker gains remote access to your device, the detrimental implications are endless.
Phone scams, like in the one mentioned above, are delivered to numerous organizations and even sent to personal email accounts with motives ranging from monetary gain to stealing personal information directly from a user’s computer. In this blog we will discuss how phone scams have upped their game in the past year, appearing even more legitimate and managing to evade the detection engines of many email security vendors.
First, show me the receipts
Let’s start off with a recap about the basics of phone scamming:
A typical phone scam is relatively straightforward. It starts with an email. Scammers use the display name of a legitimate company to appear as though they themselves are that vendor. Common display names include PayPal, Norton, Geek Squad, and Windows Defender.
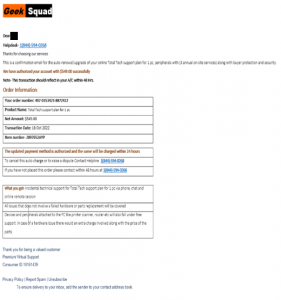
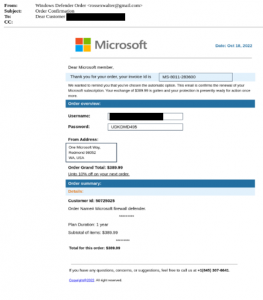
Figures 1 and 2: Typical phone scam email
Armed with the phony (pun intended) display name, scammers then send their target a receipt. This is a common method, as a receipt allows the attacker to organically slip in the phone number that they want the user to call.
To make the receipt seemingly even more realistic, scammers provide information about the fake order and a number to call for support. Scammers also add details in the footer of their emails for more “legitimacy”, like buttons to report spam, unsubscribe, or read the private policy. All of these spoofed specifics serve to bolster the legitimacy of the phone number, which scammers want their targets to call, call, call!
Once they have you on the line, scammers pose as helpful experts. In reality, their goal is to have you play into their hands and willingly offer up your personal information (date of birth, address, identification numbers, etc.) and/or financial details. As we learned in the “Geek Squad Phone Scam,” attackers can also leverage calls to convince you to provide them with access to your computer.
Now that we have established the basics to an email phone scam, let’s review some more complex examples.
Please find the invoice attached
Part of a scammer’s job is to adapt their methods to evade email security engines. In the following two examples, we discuss two ways scammers try to bypass detection:
Did you see my PDF?
To avoid detection, some scammers opt to send PDF files to their targets. These PDFs are usually sent without much text in the body of the accompanying email, prompting the user to open the attachment to learn more.
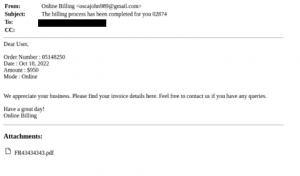
Figures 3 and 4: PDF phone scams
All I got were these PNGs and JPEGs
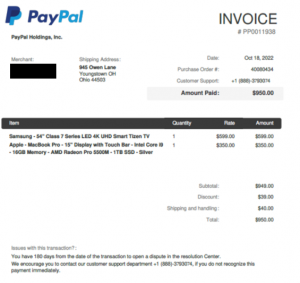
The second evasion technique beloved by scammers involves using embedded photos. Embedding PNGs or JPEGs into the body of an email makes malicious activity even harder to catch because there is little to no written information to extract from a photo.
Upon opening the PDF, PNG, or JPEG file, there is usually a receipt that contains a prominent contact number, revealing the scammer’s ultimate payload.

Figure 5: JPEG file phone scam example
While it is difficult to detect phone scams like these, it isn’t impossible. Perception Point’s advanced threat detection platform, for example, was able to catch these phone scams by leveraging visual similarity and content-based rules. Without our proprietary detection engines, we would not be able to properly scan more PDF and image-based files.
If it’s from them, it must be real!
In these next examples, the scammers leveled up: they put their money where their mouths were and signed up for popular accounting application services like Intuit QuickBooks and Xero to increase the legitimacy of their invoice request. By sending the invoice through third-party accounting software, the user is more likely to trust the source of the invoice. Upon viewing the fake invoice, users are then prompted to call the provided phone number for help, going through the motions of a phone scam.
Our IR team used a Sender Policy Framework (SPF) to verify the identities of the senders. As it turned out, the emails originated from the same domain as non-fraudulent invoices and the IP addresses corresponded to the legitimate IP addresses of Intuit Quickbooks and Xero. This makes these phone scams all the more dangerous, as attackers attempt to evade detection by abusing legitimate services.
Note that prior to publishing this post, we contacted both Quickbooks, an Intuit company, and Xero. Intuit confirmed that they are taking the necessary steps to address this issue.
Perception Point was able to catch these emails by using the same visual similarity capabilities and content-based rules that helped identify the previous set of PDF/JPEG/PNG emails.
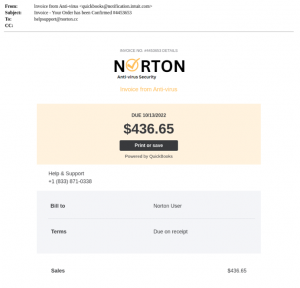
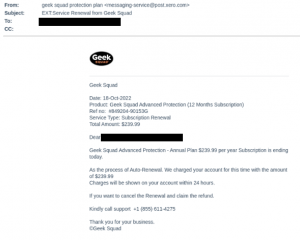
Figures 6 and 7: Scammers abuse legitimate services to carry out their malicious activity
We’re here to fix your phone (scam)
What makes these phone scam examples particularly difficult to detect are the evasion techniques employed by the scammers. Rather than simply providing a number and a stress-inducing situation, these scammers go the extra mile to bypass the detection engines trying to stop them.
However, one thing remains unclear: who am I speaking to?
Hello, who is this?
When a victim calls the provided number, 9/10 times they are greeted by an English speaker who just so happens to have a South Asian accent. This is because most phone scams are run through Indian scam call centers.
Phone scammers exploit the existing infrastructure of the call center industry to carry out their scams. It is no secret that many organizations outsource their support services to call centers in India. By doing so, these companies’ databases are at risk, as they are made more accessible to scammers looking to steal large amounts of information. Once a scammer possesses a database, they can set their operation in motion.
Goodbye for now
To combat these malicious actors, some white hat hackers have taken the vigilante approach. They call the fake support center and manage to hack the scammers. It is through these exploits that many of the scammers’ IP addresses are exposed, often leading back to India. To learn more about these anti-phone scammer “missions,” we recommend checking out this video by YouTuber Scammer Payback or this one by YouTube’s Kitboga.
Thank you for calling
Now that we have reviewed some of the origins and evasion methods used in phone scams, let’s go over some tips on how to protect yourself and your organization from this type of attack:
- Beware of generic greetings and unfamiliar email addresses or phone numbers.
- Don’t be afraid – hang up the phone or delete the email. Block the email address and number associated with the scam.
- Always check the display name and sender’s email address. Changing the display name is very common so be sure to validate the email address to decrease the chance of a successful spoofing attempt.
- Contact the company yourself before taking any action. You can always verify whether a communication is legitimate by reaching out to the company directly using an official phone number or email address.
- Never give access to your computer to a third-party service you do not trust.
- When in doubt, ask for a second opinion from your company’s security expert or IT team.
- Use an advanced email security solution with dynamic analysis of files and URLs and advanced anti-phishing engines, so that these types of email attacks won’t ever land in your user’s inbox. By intercepting these emails, you don’t need to rely on your employees’ ability to catch these sophisticated phishing attacks.
Find more information on how to secure your business with Perception Point here.
A special thanks to Elad Damari for his research on this piece.























