Perception Point’s team of security researchers recently discovered a phishing campaign targeting users by exploiting an open redirect vulnerability from a domain belonging to coffee connoisseur, Nespresso.
Attackers use compromised accounts and the redirect in order to bypass detection and steal victims’ Microsoft login credentials.
The Attack Flow
This attack starts with an email. Albeit, in this instance a very strange email that at first glance appears to be a multi-factor authentication request from Microsoft. The email sender is unaffiliated with Microsoft.
At the bottom of the message it seems that the email has been forwarded twice. This creates a rather muddled message that the attacker likely fabricated entirely. Perhaps the intent of the “forwarding” was to provide an explanation as to why the email doesn’t originate from Microsoft. Regardless of the convoluted details, the overall message is clear.
The email urges the recipient to check their recent login activity.
Upon clicking the link, the user is first directed to the infected Nespresso URL, followed by a redirection to an .html file. The goal of using the Nespresso open redirect vulnerability is to evade security measures. Attackers know that some security vendors only inspect the initial link, not digging further to discover any hidden or embedded links. With this knowledge, it makes sense that the attacker would host the redirect on Nespresso, as the legitimate domain would likely be sufficient to bypass many security vendors, detecting only the reputable URL and not the subsequent malicious ones.
“https://t.uk.nespresso.com/r/?id=h859505ee,590c6122,56f60c49&p1=intervisus.com.br”
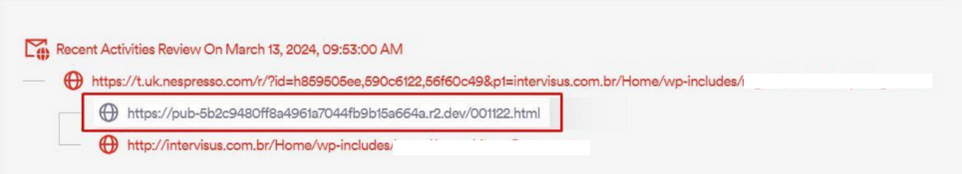
The .html file serves as a fake verification page to establish a sense of legitimacy with the user.
The .html file then redirects to the final URL – a spoofed Microsoft login page.
The fake login page makes the payload clear: harvest credentials, presumably to fuel more of these deceptive campaigns.
Campaigning
Perception Point security researchers observed this attack flow carried out with multiple different sender domains. The commonality in each attack was the Nespresso redirect and apparent forwarding from a Bank of America employee.
Example 1:
Example 2:
Behind the Phishing Attack
This attack begins before it starts. For an attack like this to be successful, the attacker must first do some groundwork. In this case, the preparation involves 1) Account Takeover and 2) Identify Open Redirect Vulnerability. Let’s break down each of these steps and examine how they work together to form this campaign.
- Account Takeover
The best way to send a phishing email is with an email account that has already been phished. When an attacker obtains stolen credentials via a successful phishing campaign or by other malicious means, they aren’t done there. Rather, receiving the credentials allows them to execute account takeover attacks, using the credentials to log in and thus compromise the victim’s account.
In this attack, all the senders pass the SPF check, as the domains are legitimate. This indicates that the domains were not newly created for the attack but rather historied accounts that had most likely been compromised. This way, the attacker’s malicious emails could appear genuine, as they were sent from reputable domains.
- Identify Open Redirect Vulnerability
The most unique and debatably complex aspect of this attack is its inclusion of an open redirect vulnerability. Open redirect vulnerabilities occur when an attacker manages to redirect users to an external, untrusted URL through a trusted domain. This is possible when a website or URL allows data to be controlled from an external source. In this attack, the threat actor located an open redirect through Nespresso’s site, which they then used to forward to a spoofed Microsoft login page.
In combination with the compromised accounts, the attacker optimized the campaign for maximum success to bypass security measures and trick users into handing over their credentials.
Preventing the Attack
One of the ways that Perception Point’s Advanced Threat Prevention platform detected this phishing attack was with the Recursive Unpacker, one of our detection engines. The engine scouts for files and URLs embedded within the email or attachments. It then extracts the elements and scans them separately through the rest of our detection engines. This capability allows us to uncover even the most evasive techniques.
In this case, our platform was able to discover the malicious payload that lay beyond Nespresso’s site.
For more information about how to prevent phishing attacks like these from reaching your organization, check out our guide here.
























