Perception Point’s security researchers recently detected a new and sophisticated QR code phishing campaign, targeting hundreds of organizations worldwide.
This campaign exploits open redirect vulnerabilities within Microsoft services, a critical component that amplifies the threat’s severity. By leveraging these vulnerabilities, attackers deceive victims using the trusted reputation of Microsoft platforms.
Our in-depth analysis reveals the inner workings of this campaign, highlighting the increasing sophistication of threat actors and their advanced evasion tactics.
What is Open Redirect Vulnerability?
Before analyzing the campaign, it is crucial to understand the technical nature of open redirection vulnerabilities. These vulnerabilities arise when a web application or server is configured in a way that allows an attacker to redirect a user to an external, untrusted URL through a trusted domain. In this context, attackers exploit such vulnerabilities within one of Microsoft’s cloud services, using parameters in URL queries that are unvalidated or improperly sanitized. This oversight allowed them to craft URLs that appear to belong to Microsoft, yet redirect to a spoofed login site, thereby gaining a sense of legitimacy and dramatically increasing the effectiveness of their phishing attempts.
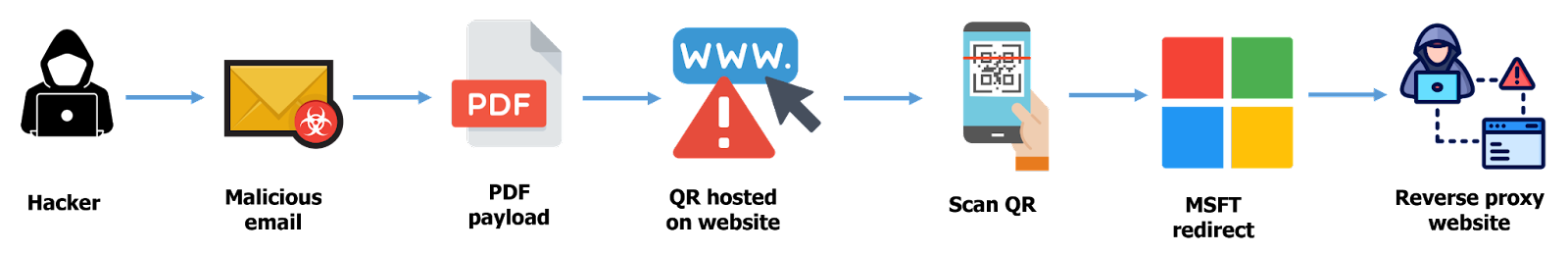
Step #1 – The Opening Email
The campaign starts with users receiving emails from a seemingly legitimate domain, designed to easily pass standard SPF checks. These emails contain the subject line “Please fix your credentials,” which creates a sense of urgency, prompting recipients to take immediate action.
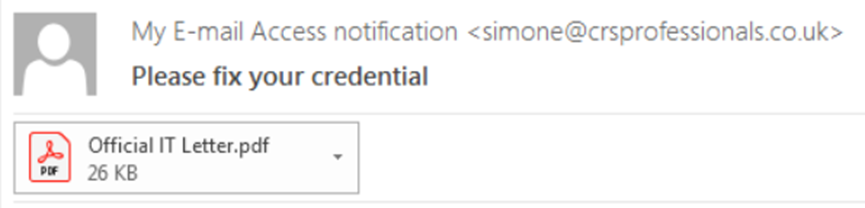
Apart from the vague subject line and a PDF attachment titled “Official IT Letter,” the email itself contains no other textual content.
Step #2 – A Decoy PDF
Every email includes a PDF purportedly from Microsoft Support. The PDF instructs users to update their passwords promptly using a provided code. The attackers included actual logos of targeted organizations and addressed the message on the PDF to the specific targets. The users are prompted to click on a link contained in the PDF in order to update their email credentials.
The user is instructed to open the link and scan it with their phone camera in order to access the code. This primes the user for the next step of the attack.
Step #3 – Flickering the Malicious QR Code
When the user clicks on the link in the PDF it leads them to an image of a QR code with the Microsoft logo on it. The picture of the QR code is hosted on a legitimate server that belongs to popular image hosting platform Flickr. This step is critical in the process, as it mirrors the first phase of a two-step phishing attack.
In two-step phishing attacks, the first step is designed to build trust. By using legitimate online services like Flickr, attackers lend an air of authenticity to their campaigns. This first step is akin to a magician’s initial trick or ‘show’ in the two-step process – it’s meant to captivate and distract. The target, seeing familiar elements like the Microsoft logo and a credible hosting platform, is more likely to trust the source and proceed with the action.
The inclusion of the malicious QR code utilizes a psychological maneuver that greatly benefits attackers and increases their success rates. They move the “playground” from the computer screen onto a mobile phone which is far less protected; there, victims are less likely to inspect the URLs and follow security protocols.
Step #4 – Microsoft Open Redirect Exploitation
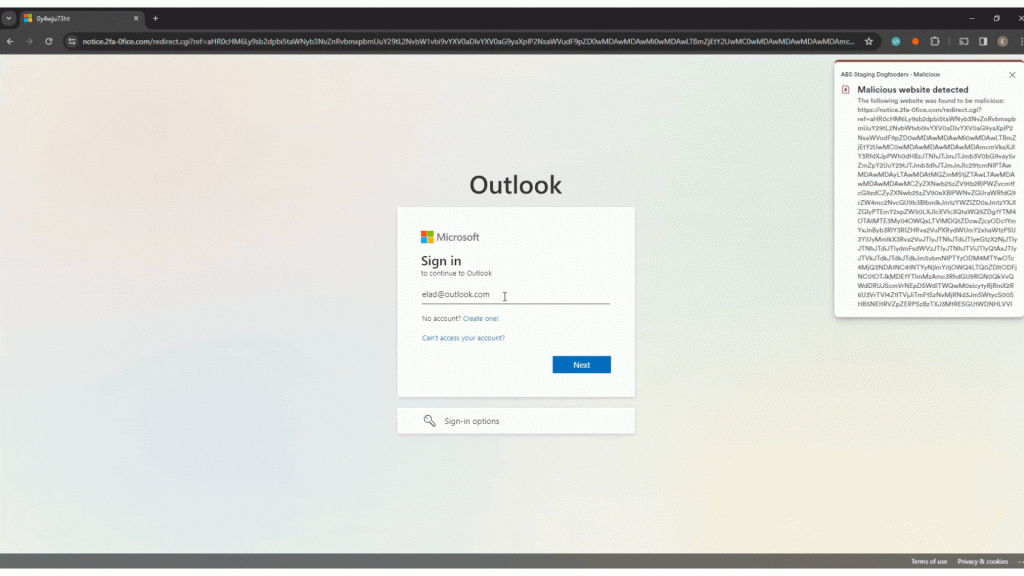
Scanning the QR code leads the user through a series of URLs, exploiting an open redirection vulnerability in one of Microsoft’s services. The attacker managed to exploit an open redirect on Azure Functions, a Microsoft cloud service for app developers, to create a convincing chain of redirections that end up with a spoofed Microsoft 365 login page. This tactic masks the phishing attempt under the guise of legitimate Microsoft URLs.
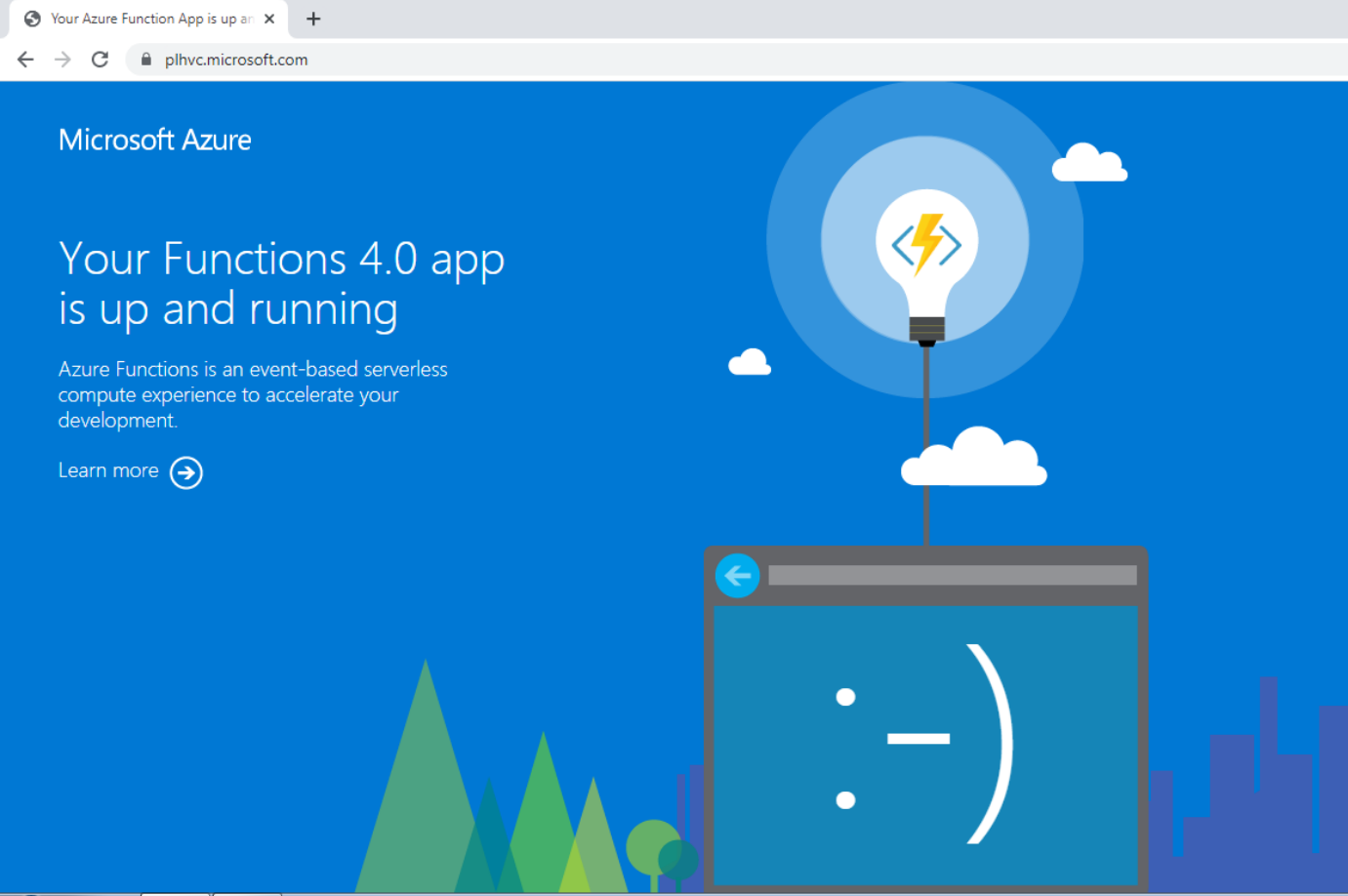
This is how the redirection plays out after the user scans the QR code:
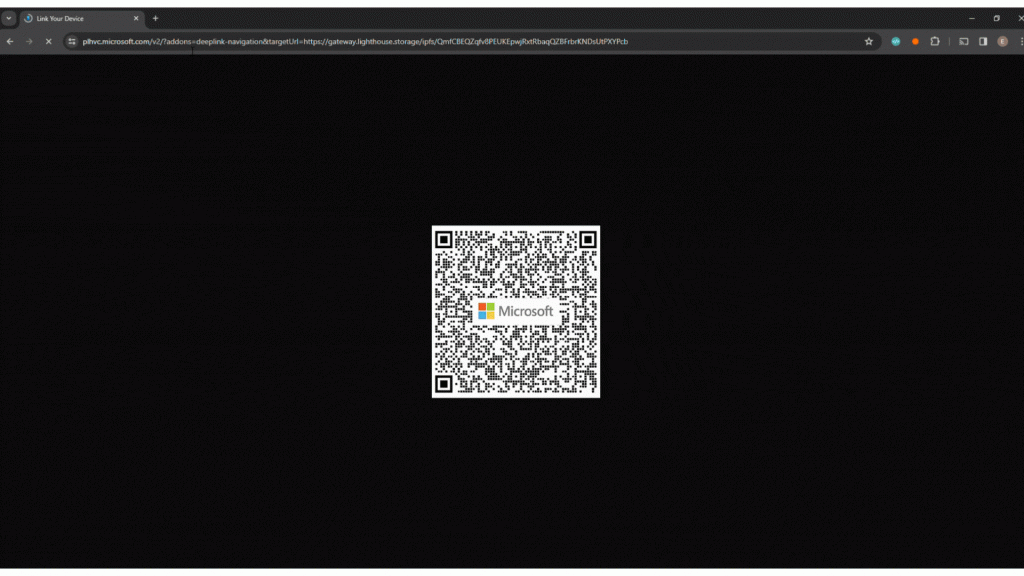
This approach not only bypasses basic email security filters but also plays on the inherent trust users have in Microsoft’s security infrastructure.
The “NakedPages” Phishing Kit
The final step of the sophisticated phishing campaign is the use of the “NakedPages” phishing kit. This kit employs advanced techniques like reverse proxy and cookie manipulation, which are effective even against robust security measures like two-factor authentication.
Upon inserting the username/email address on the spoofed Microsoft login page the target gets redirected again to the legitimate login.live.com – Microsoft’s real login page. The threat actor sets a session cookie on the user’s device during the redirection process and operates as a “man-in-the-middle” to easily access the victim’s account.
NakedPages Phishing Toolkit
Some of the features that make the NakedPages toolkit extra dangerous include:
- Reverse Proxy Functionality: Uses a reverse proxy to hide the malicious server’s location, evading detection.
- Cookie Manipulation: Sets cookies during redirection, tracking user interactions and maintaining persistence.
- Seamless Login Experience: Ensures a smooth login process for the victim, avoiding suspicion.
- Bypassing 2FA: Designed to circumvent two-factor authentication, possibly capturing 2FA tokens or exploiting vulnerabilities.
- User-Agent Spoofing: Mimics legitimate user behavior by spoofing user-agents, complicating detection.
- Real-Time Phishing: Adapts dynamically to user interactions, enhancing the attack’s believability.
- Persistence Mechanisms: Maintains control over compromised accounts through regular cookie updates.
- Obfuscation Techniques: Employs code obfuscation to evade security scanners.
- Data Exfiltration: Extracts sensitive user data, like login credentials, for malicious use.
- Continuous Updates: Regularly updated to exploit new vulnerabilities and adapt to changing security measures.
Collaborative Response: Perception Point Alerts Microsoft to Mitigate Threat
When Perception Point’s Incident Response team came across this attack, they quickly notified Microsoft’s security team, sharing the findings about the open redirection vulnerability. Microsoft subsequently addressed the exploit and mitigated the issue.
Conclusion: Vigilance and Adaptation Key to Countering Evasive Quishing Threats
This sophisticated campaign exploiting Microsoft’s open redirect vulnerabilities is a stark reminder of the evolving nature of evasive phishing attacks. It highlights the need for constant vigilance and adaptation in cybersecurity strategies. At Perception Point, our swift detection and mitigation of this quishing threat exemplify our dedication to staying ahead of cybercriminals’ evasive maneuvers. We urge organizations to remain alert, regularly update their security protocols, and educate their teams to recognize and respond to such advanced threats effectively.
Contact us to find more about our AI-powered security solutions and gain deeper insights into protecting your organization’s workspace.
























