In recent months, researchers report seeing a surge in social engineering attacks that target hotels that use Booking.com and steal the hotels’ access credentials for the site to scam their customers. Many of the attacks appear to be targeted or opportunistic and are fueled by information stolen via information-stealing malware, or info stealers.
“The most common infections used to steal accommodation accounts have been Raccoon, Redline, Lumma, Vidar and MetaStealer – all commodity info stealers available for purchase as malware-as-a-service,” says a new report from threat intelligence firm Kela. “This means that after different actors had targeted properties using this malware – whether in targeted or opportunistic campaigns – they decided to monetize it by selling. Consequently, this opened the door for numerous other cybercriminals to exploit the same access point.”
Each batch of information stolen from a system is known as a bot, and bots are sold via dedicated marketplaces and Telegram channels (see: Info Stealers Thrive in Hot Market for Stolen Data).
This year alone, Kela said, it has counted over 185,000 accounts for sale on such markets that are “associated with Booking.com” and an average of 16,800 newly harvested ones that are being offered for sale each month. The firm said it also discovered for sale “hundreds of other corporate accounts, particularly those with property-related keywords in their emails,” such as the word “reservation” in the username plus a hotel name in the URL, which could be used to scam customers.
Cybersecurity firm Secureworks said its threat intelligence researchers “have observed a high demand on underground forums for Booking.com property credentials,” and some buyers are requesting “info stealer logs that include credentials for the admin.booking.com property management portal, while others have offered to sell logs and associated services such as log checking and parsing.”
While Booking.com offers two-factor authentication to help block stolen credentials from being used to log into its site, researchers said victim hotels didn’t appear to have enabled it.
Hotels and their booking software remain regular targets for malicious hackers, oftentimes as a source for payment card data. Verizon’s latest Data Breach Investigations Report, based on 5,199 confirmed data breaches investigated by over 60 organizations, found that in every hospitality breach, the attackers’ motive appeared to be purely financial.
One-third of hospitality hits involved ransomware, according to the latest DBIR, and in the majority of cases, attackers instead deployed RAM-scraping malware – most often against point-of-sale software – designed to steal payment card data, although sometimes they also stole customers’ personal information.
How Info Stealers Fuel Attacks
In a September report, researchers at cybersecurity firm Perception Point detailed ways in which this information is used to socially engineer hotels and associated organizations.
Many times, attackers first book a room and then email customer service with a message “crafted to elicit both empathy and a sense of urgency,” the researchers said. Common tactics included claiming to be traveling with a child whose food allergies made them prone to suffering anaphylactic shock or elderly parents who wanted to print photos during the trip.
Researchers said the next step was to trick the victim into retrieving supposed dietary information or images to be printed via a password-protected website, via a link in an email that led to a cloud repository such as Google Drive. If clicked, the link would download the supposed information or photos onto a user’s computer and execute, installing info-stealing malware on the system.
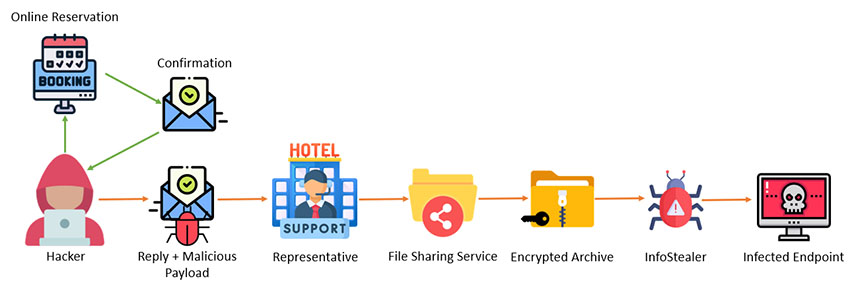
In one case investigated by Secureworks, “the day after the malware was executed, a hotel employee observed that multiple messages had been sent to upcoming guests from the hotel’s Booking.com account,” it said. “Several hours later, hotel customers started to complain that money had been taken from their accounts. The threat actor likely deployed Vidar to steal the property’s Booking.com credentials and then abused them to access the account.”
Best Defense: Technical Controls
Social engineering expert Sharon Conheady said this type of trickery remains extremely difficult to repel, because of the customer-first nature of hospitality. Many public-facing people in such organizations, such as receptionists, are “trained to help people – that’s their job,” and of course they’re going to bend over backwards to try to meet apparent customers’ demands, Conheady said in an interview at this month’s Black Hat Europe conference in London.
Help desks remain another frequent target. “I had a client lately who asked me to call the help desk and obtain BitLocker keys,” she said, referring to a recent penetration test. “Every single one of the help desk agents gave us the BitLocker key.” That prompted her to ask: Do these personnel even know what a BitLocker key is, and why they shouldn’t share it? The client said they didn’t know.
While training people in customer-facing roles can help, Conheady said the only truly effective approach would be to put in place strong technical controls to outright prevent and block such attacks.
Scammers Reaching Out to Customers
In the meantime, information stolen from hotels that use Booking.com continues to be used to target its customers. One repeat scam seen since March and detailed on the Curated Intelligence site, which tracks cybercrime trends, involves attackers using the stolen credentials to masquerade as a hotel and directly message customers via the Booking.com site. “The message was letting the guests know that they are required to enter their information in an online form, with the premise of combating stolen credit card fraud (the irony!),” the researchers reported.
If a target clicks a provided link, the researchers said, it appears to take them to a Booking.com look-alike site that accurately lists the details of their stay, leading to a page where they can input their credit card details, which get routed to attackers.
This article first appeared in Bank Info Security, written by Mathew J. Schwartz on December 22, 2023.
























