A new phishing campaign detected by Perception Point and reported by Akamai is targeting Booking.com users and is a prime example of the lengths threat actors will go to for a payday. This attack exemplifies the alarming threat levels the hospitality sector as a whole faces in 2023 as threat actors leverage InfoStealer malware compromised hotels to access guests’ booking information and attack them in follow up campaigns.
Check-In Charade: From Booking a Stay to Hooking the Pay
1. Breach and Takeover: The campaign kicks off with threat actors breaching hotel systems, subsequently taking control of the hotel’s official account on Booking.com.
2. Guest List Hack: With the official Booking.com account in their hands, malicious actors access sensitive customer data: full names, booking dates, hotel details, and partial payment methods used to make the reservations on the platform. This data forms the foundation for the attacks that ensue.
3. Reservation Ruse: Using the harvested data, attackers craft individualized messages. These messages are designed with precision, using social engineering techniques to create a sense of urgency. Victims are informed that they need to provide their credit card details again as a verification “test,” with the threat of their booking being canceled within 24 hours looming, if they fail to comply.
4. Linking to the Lobby Trap: The attackers’ message, sent to the guests via the Booking.com platform and also by email from Booking.com, contains a link that leads victims to a meticulously crafted phishing page, mirroring Booking.com’s interface. This page is pre-filled with the victim’s personal details, including their full name, stay duration, and hotel information. The URL, designed to further deceive, follows the pattern: ‘booking.id(numbers).com’ or ‘booking.reserve-visit.com’.
Since the threat actors have partial information on the original payment method used by the targets to book the reservation, the message specifically asks for it in full (a Mastercard card, for example).
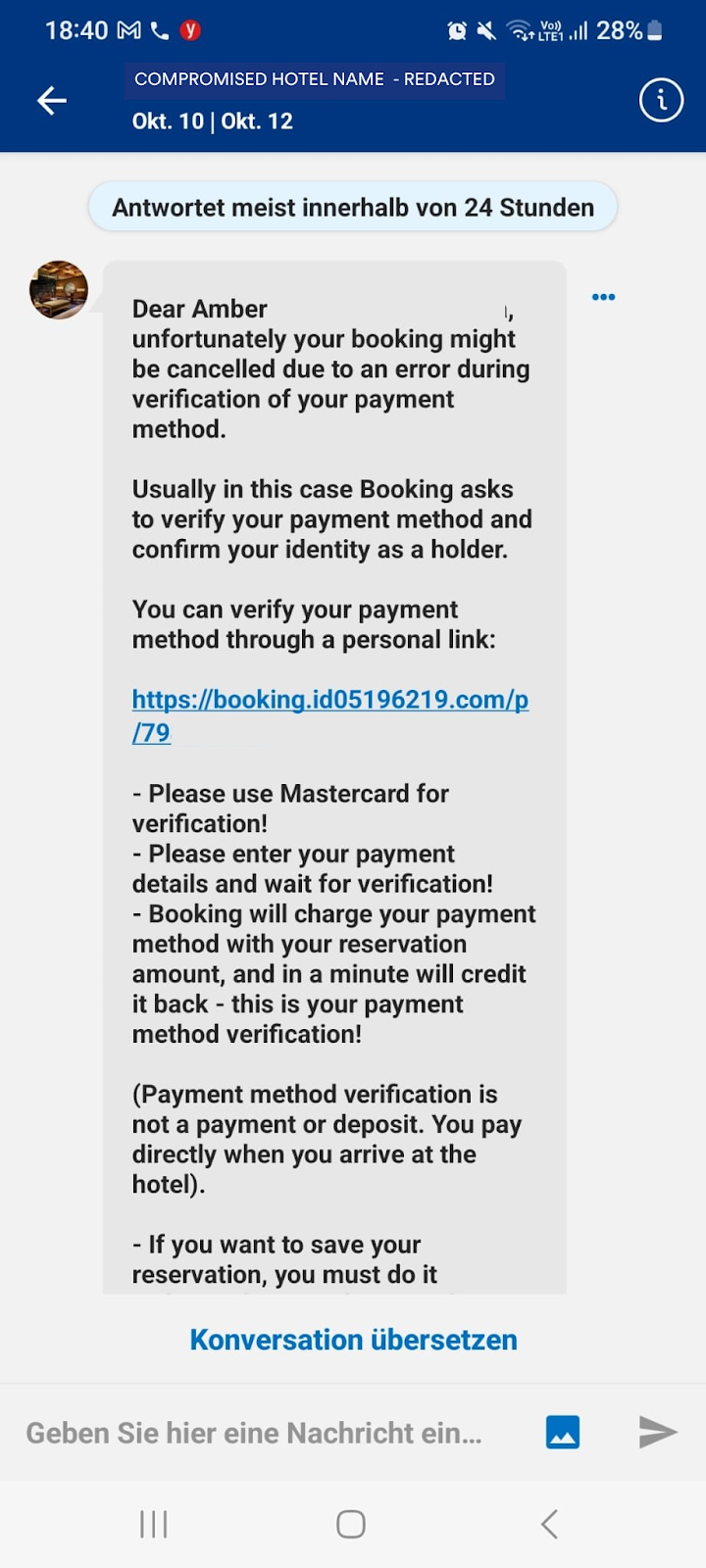
The Final Snare – Harvesting Financial Details: Once on the phishing page, victims are prompted to re-enter their credit card or bank information. Unknown to them, this data is directly harvested by the attackers, paving the way for potential financial fraud.
The Deceptive Details: A Deep Dive into the Attack
A Phishing Trip via Booking.com
One of the most alarming aspects of this phishing campaign is its method of delivery. The phishing links are dispatched directly through the Booking.com platform, whether it is the site or the app, depending on what the customer is using.
This isn’t a case of a rogue email or a suspicious SMS (aka Smishing); these messages come from the very platform users trust. The source of these malicious messages? Legitimate hotel accounts that have been compromised earlier. This adds an extra layer of authenticity, making the phishing attempt all the more convincing.
A Mirror Image: The Super Convincing Phishing Page
Upon clicking the link, victims are led to a phishing page that is the spitting image of what one would expect from Booking.com. But it is not just the design that is deceptive; it is the details. The page comes pre-injected with specific information tailored to the victim: their name, the hotel they’ve booked, and the exact dates of their stay. This level of personalization, combined with the urgency conveyed in the message, creates a perfect storm. The immediate threat of a canceled booking, especially when plans are often set in stone, can lead victims to act impulsively, providing their credit card details without a second thought.
The Global Impact: Millions of Dollars Potentially Lost
Perception Point’s research indicates that this is far from an isolated incident or a small-scale scam. We estimate that hundreds of hotels and resorts worldwide have fallen prey to these breaches. The ripple effect? Thousands of targets, if not more. While the exact scope of the losses remains undisclosed, preliminary assessments suggest that a single victim could be out of pocket anywhere from hundreds to thousands of dollars. The financial implications are severe, but the breach of trust and the potential misuse of personal data could have even more far-reaching consequences.
Connecting the Corridors: From Infostealer to Booking.com
Drawing parallels with a previous campaign, Perception Point’s security research team suggests that the intricate InfoStealer campaign targeting hotels and travel agencies could potentially serve as a precursor to the recent Booking.com phishing attack.
In our recent report we shed light on the up and coming alarming trend.
The modus operandi discovered:
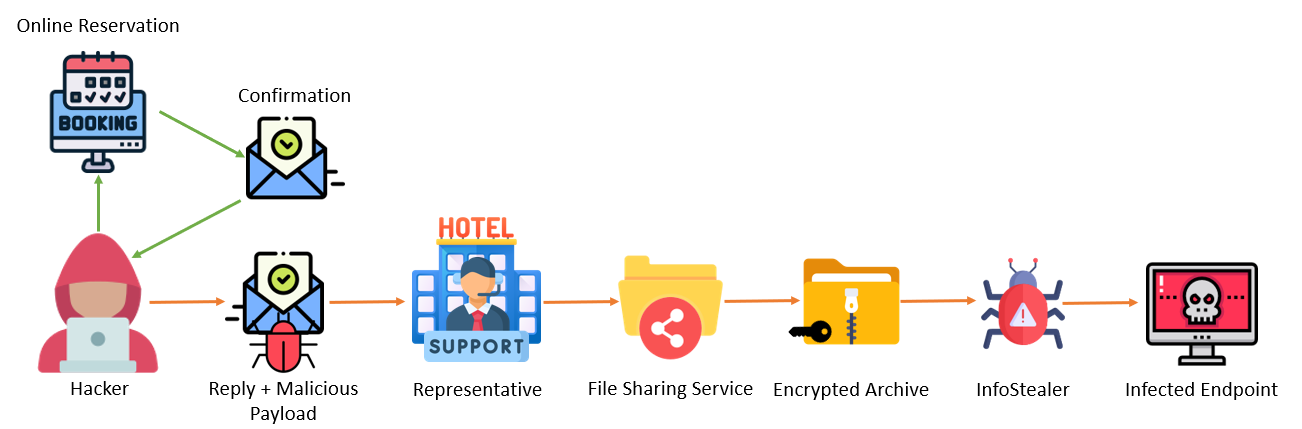
- Initial Booking: The attacker makes an online booking, often with free cancellation to minimize risk.
- Crafting the Reply: Using the confirmation email, the attacker replies with a specific request or question about the reservation.
- Adding the Lure: The attacker attaches a link to a file-sharing service, providing a plaintext password for “important files.”
- Baiting the Victim: The email is directed either to the online booking service’s support or directly to the hotel.
- The Trap: The representative, believing the email to be genuine, downloads an archive from the provided link, which, when opened, releases Infostealer-type malware into the system.
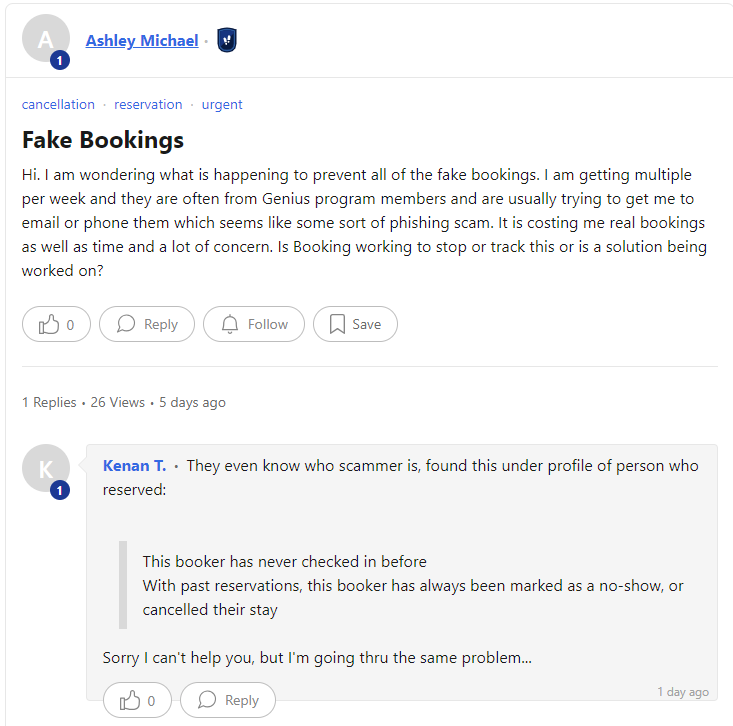
Booking.com partners are beginning to raise a flag regarding bogus reservations made for phishing and scam purposes.(Source)
Policies and Phishers: A Dangerous Intersection
It is important to note Booking.com’s payment policy for its hotel partners: Booking.com charges guests based on the hotel’s policies and ensures they pay in full before arriving at the property. If a guest provides invalid credit card information and fails to update it or provide valid card details within 24 hours, Booking.com will automatically cancel the reservation. This policy adds another layer of authenticity to the attacker’s claim, making the phishing attempt even more convincing.
Final Call at the Front Desk: Safeguarding Your Stay
As cyber threats continue to evolve, it is crucial for users to be vigilant and informed. Here are some recommendations to ensure a safe online experience:
Double-Check URLs: Always scrutinize URLs to ensure they align with the legitimate website. Look for subtle misspellings or unfamiliar domain extensions. Look for suspicious links on pages that don’t function properly or lead to broken pages.
Beware of Urgent Requests: Cybercriminals often induce a false sense of urgency to trick victims into acting without thinking. Always take a moment to verify the legitimacy of any urgent request.
Contact Directly: If you receive a suspicious email or message from a service provider, contact them directly using official contact details, not the ones provided in the suspicious message.
Educate & Inform: Share your knowledge about phishing and other cyber threats with friends and family. The more people are aware, the less likely they are to fall victim.
Trust Your Instincts: If something feels off, it probably is. Always trust your gut feeling when it comes to online interactions.
Regularly Monitor Your Accounts: Keep an eye on your bank and credit card statements for any unauthorized transactions.

























