Perception Point’s security research team often finds itself at the forefront of advanced campaigns, tackling a diverse array of cybersecurity threats.
Recently, the team encountered a particularly malicious quishing campaign, involving password-protected PDFs with the password being cleverly concealed within an image. This subtle maneuver not only outsmarts most email security solutions and OCR safeguards, but it also sets the stage for concealed QR codes, hidden within the PDF, which lead to malicious credential phishing destinations.
Using such covert tactics showcases the ingenuity of the attacker in crafting a method that goes beyond conventional approaches, potentially increasing the success rate of the phishing campaign.
In this blog, we peel back the layers of this emerging evasion tactic.
But wait, what is OCR?
Optical Character Recognition (OCR) is a tech superhero that not only reads text in images and scanned documents but also serves as a protective shield. Think of it as magic glasses for your computer – it can turn pictures of words into actual text that your computer can understand. This not only makes information accessible but also adds a layer of protection by helping to ensure that the text is accurately recognized and processed. OCR is like a guardian for your digital documents, making them more manageable and secure.
Sleuthing in the Shadows: a Closer Look
Attackers are constantly refining their methods to slip past the watchful eyes of detection engines and bypass OCR safeguards. In this blog we hone in on a meticulous attacker, motivated by orchestrating an attack so advanced and discreet that it effortlessly bypasses these robust security measures. Here’s how it works:
The attacker focused on specific targets within the hotel industry. Each email contains a password-protected PDF supposedly sent from a hotel’s store.

The attacker sets a ‘reference code’ for each email in a Microsoft SharePoint file, such as ‘1483033.’ The password for the locked PDF is then automatically generated from the three numbers following the initial one in the reference code, e.g., ‘4830.’ This automated process is applied to every email, showcasing the clever and deceptive nature of the attack.
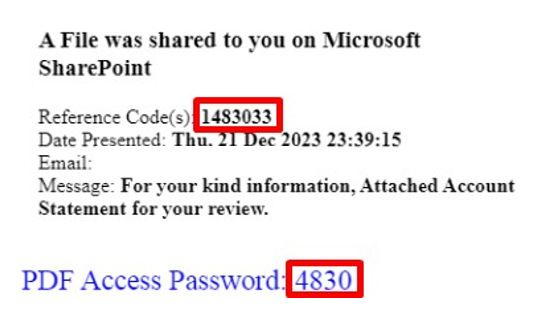
The password is hidden within an image in the email, exploiting OCR gaps for a sophisticated attack. This strategic image maneuver is a calculated move to outsmart detection engines, turning the password into a graphic element to evade OCR detection.
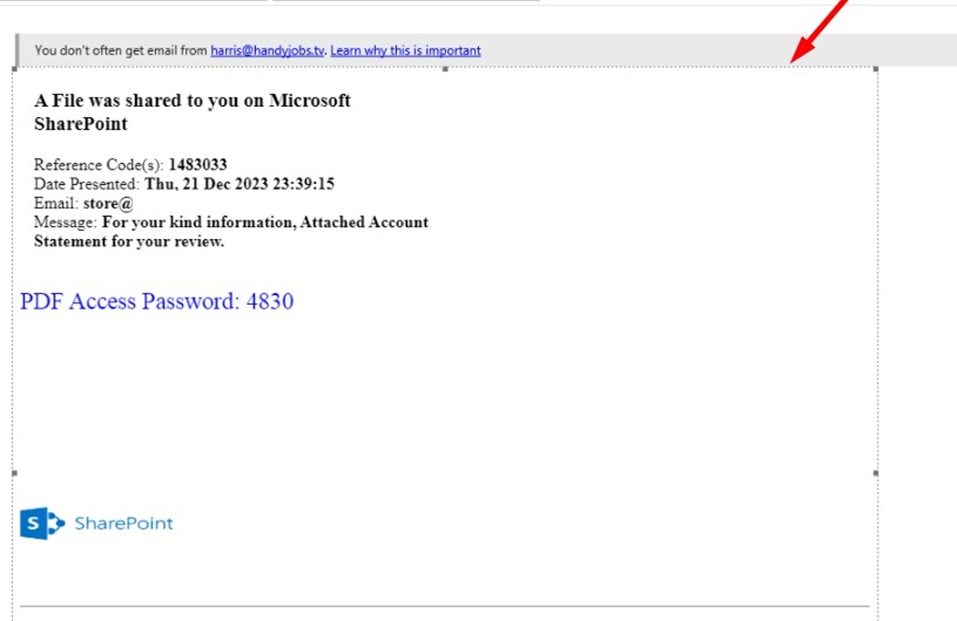
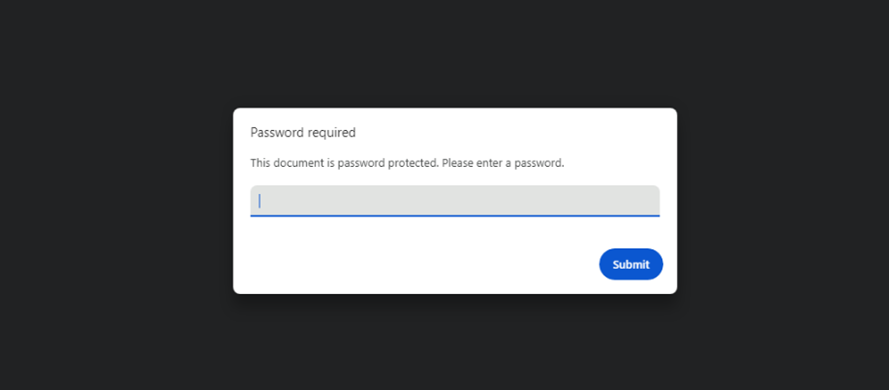
The target is prompted to open the secure PDF file. Once the PDF is opened, the recipient must enter the provided password.
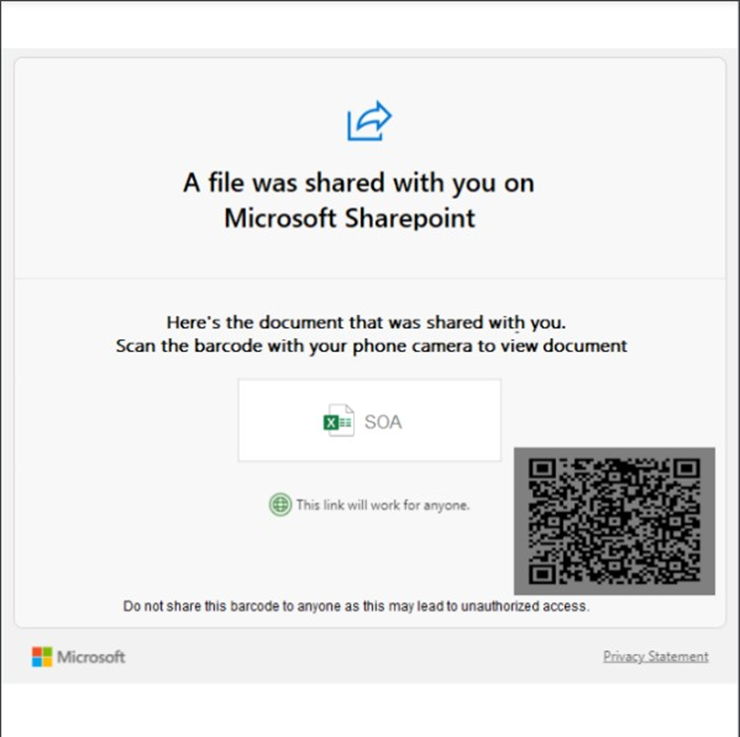
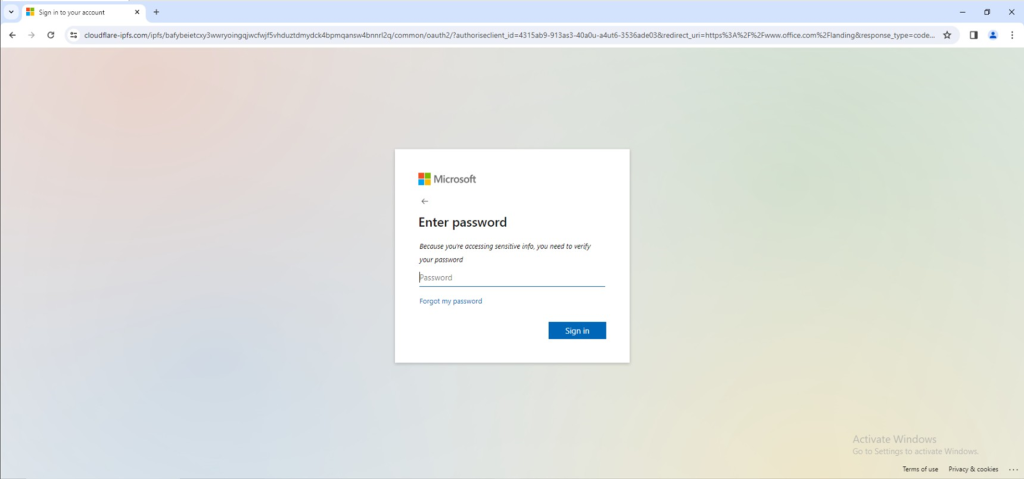
Upon accessing the PDF, the target encounters what appears to be a Microsoft SharePoint file leading to a document. In order to view the document, the user must scan a QR code. Below the QR code is an advisory, underscoring the importance of not sharing the link to avert unauthorized access. This ultimately adds the guise of authenticity to the file.
In the last phase of the attack, the target is prompted to provide login credentials, thinking they are accessing shared content. Scanning the QR code redirects the user to a fake Microsoft login page, where they believe entering credentials is the final step to access the shared document. In reality, the attacker steals the user’s credentials and finalizes their malicious agenda.
Broader Implications and Countermeasures:
This attack underscores the critical need for heightened cybersecurity measures. Organizations should consider bolstering email security protocols, educating employees about phishing threats, and implementing robust OCR protection to thwart such calculated and multifaceted attacks.
By comprehensively understanding the attacker’s methodology and potential impact, organizations can fortify their defenses and individuals can remain vigilant against evolving cyber threats.
We recommend considering the following actions to mitigate your organization’s risk:
- Implement advanced email security protocols to detect and prevent phishing attacks.
- Utilize email filtering solutions to identify and block suspicious emails before they reach employees.
- Implement Optical Character Recognition (OCR) protection to safeguard against attacks that involve manipulated or malicious documents.
- Conduct regular security assessments, including penetration testing, to identify vulnerabilities in the organization’s systems and applications.
- Develop and regularly update an incident response plan that outlines the steps to be taken in the event of a cybersecurity incident.
- Regularly assess and update the organization’s systems to address known vulnerabilities.
- Enforce strict access controls and adhere to the principle of least privilege to limit the potential impact of a security breach.
- Conduct regular cybersecurity awareness training for employees to educate them about the latest phishing threats and social engineering tactics.
Read more blogs like this here:
- QR Code Red: Quishing Attacks and How to Prevent Them
- QR Code Phishing (Quishing) Attacks Have More Than Quadrupled In Just One Month
- Navigating the Next Wave of Quishing Attacks
- Quishing Campaign Exploits Microsoft Open Redirect Vulnerability
























