Enterprise Communication Protection with Perception Point
Unique, next-gen solution delivers advanced threat protection across all enterprise communication platforms while maintaining the user experience required by the modern work environment. Easily deployed, our cloud-based solution ensures no malicious URL or file is being shared, offering the same level of security expected only in email for optimal enterprise communication protection.
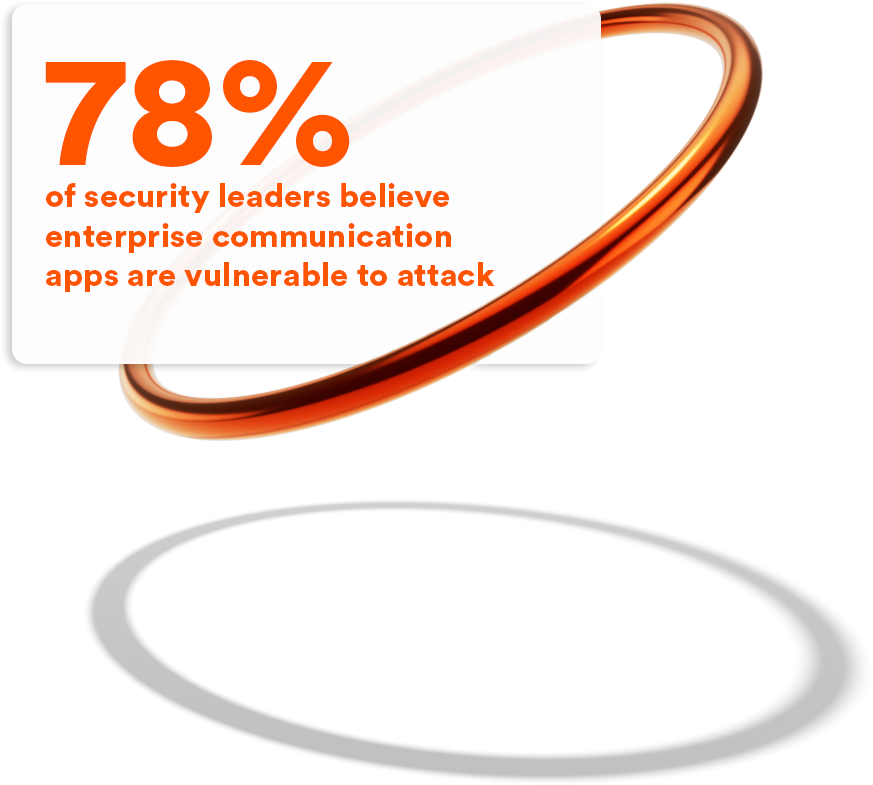
Enterprise Communication: New Platforms, Same Dangerous Threats
Insider Threats
Public Channels
An external party interacts with one of your employees via public channels – for example, open channel about sport events, music or other shared interests.
Unmanaged 3rd Parties
Secure your Enterprise Communication Apps
Content-based attacks are spreading across more and more channels, and enterprise communication (sometimes referred as “the email killers”) apps are among the best used tools. However, although considered innovative and modern, they are fertile ground for content-based attacks.
Perception Point provides the right solution specifically for this type of threat. Unlike services that monitor the access to the shared data (e.g. CASB), we scan the data itself to enable your employees to work freely and safely.
Scanning content without causing any delays to ongoing operations, keeping the same level of functionality expected from enterprise communication apps.
Allowing you to extend your current policies from your email domains to other enterprise communication apps. Capabilities include: file blocking, opening archived files for inspection, and incident management.
Creating an additional obstacle in the way of sophisticated attackers from gaining financial benefits, improving the organization’s overall network protection.
Proven Results
See Perception Point in action!
Other Related Products
Easily combine our email security platform with these other unique products from Perception Point
Internal Email
Full coverage for all internal emails to prevent ATO and lateral phishing attack from within your organization.



Cloud Apps
Stopping any content-based attack via any of your cloud-based collaboration apps in real-time.



Cloud Storage
The only solution to provide cutting-edge technology to stop malicious files and URLs from being uploaded or downloaded to your cloud storage.




























